Contents
Configure Azure AD Single Sign-On (SSO) with Joomla OAuth Client Plugin
Single Sign-On (SSO) with Microsoft Entra ID (Azure AD) in Joomla uses OAuth Authorization to provide users secure access to the Joomla site. With our Joomla OAuth Single Sign-On (SSO) plugin, Microsoft Entra ID (Azure AD) acts as the OAuth provider, ensuring secure login for Joomla websites.
The integration of Joomla and Microsoft Entra ID (Azure AD) simplifies and secures the login process using OAuth protocol. This solution allows users to access their Joomla sites with Single Sign-On (SSO) using their Microsoft Entra ID (Azure AD) credentials, completely removing the need to store, remember, and reset multiple passwords.
In addition to offering OAuth Single Sign-On (SSO) using Microsoft Entra ID credentials, the plugin also provides advanced SSO features like user profile attribute mapping, role mapping, and Azure multi-tenant login and providing site access based on organization roles. For further insights into the array of features we offer within the Joomla OAuth & OpenID Connect Client plugin, kindly visit our page here. You can follow the below steps to setup Microsoft Entra ID (Azure AD) OAuth SSO with Joomla.
Pre-requisites: Download And Installation
Steps to Install Joomla OAuth Client Plugin
- Download the zip file for the miniOrange OAuth Client plugin for Joomla.
- Login into your Joomla site’s administrator console.
- From left toggle menu, click on System, then under Install section click on Extension.
- Upload the downloaded zip file to install the Joomla OAuth Client plugin.
- Installation of the plugin is successful. Now click on Start Using miniOrange OAuth Client plugin.
- Under Configure OAuth -> Pre-Configured Apps tab, select your OAuth Provider. You can also search for custom OAuth or custom OpenID application in the search bar, and configure your own custom provider.

Steps to configure Microsoft Entra ID OAuth SSO into Joomla
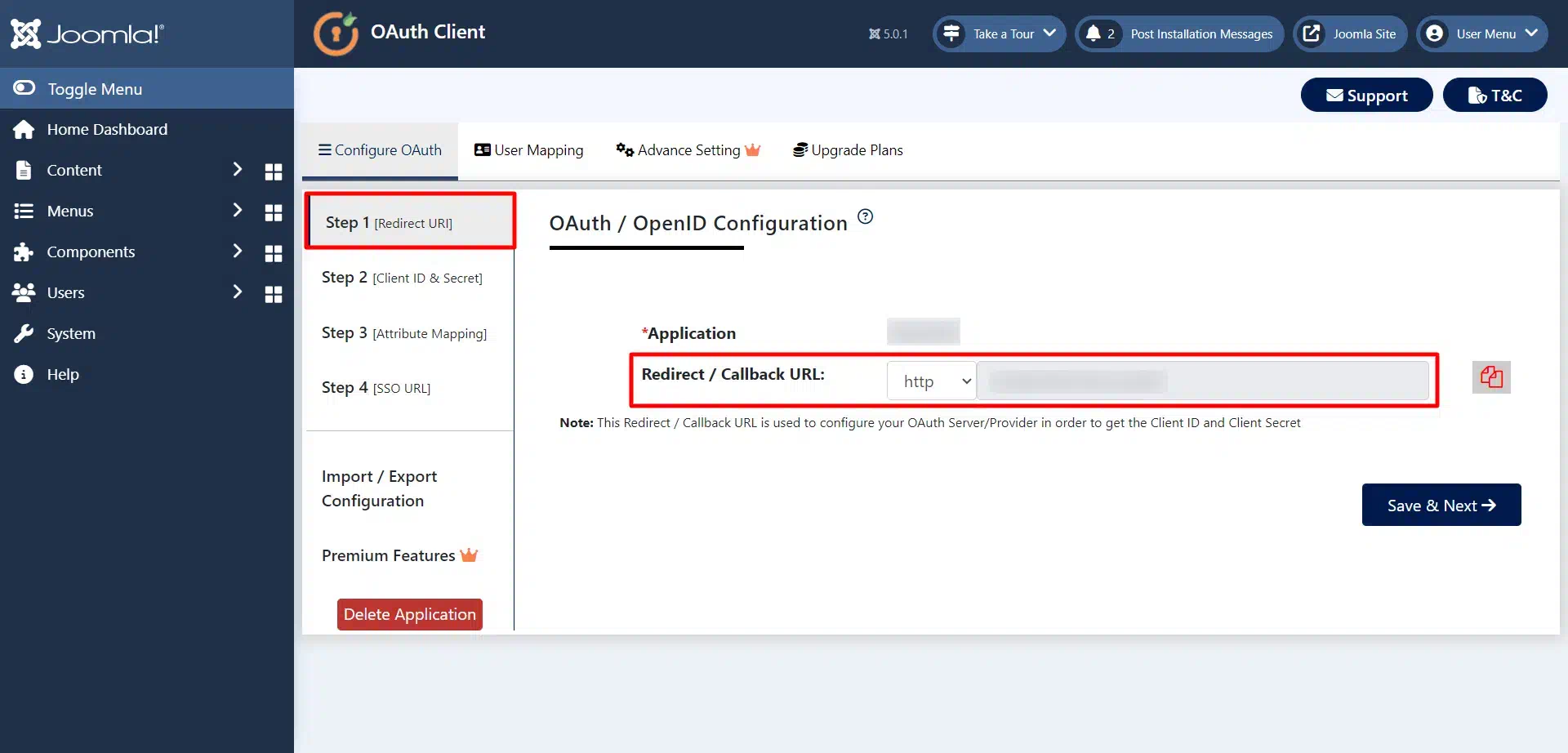
1. Configure Callback/Redirect URL
- After selecting your OAuth provider, you will be redirected to the Step 1 [Redirect URL] tab. Now copy the Callback/Redirect URL which we will use to configure Microsoft Entra ID as OAuth Server, then click on the Save & Next button.
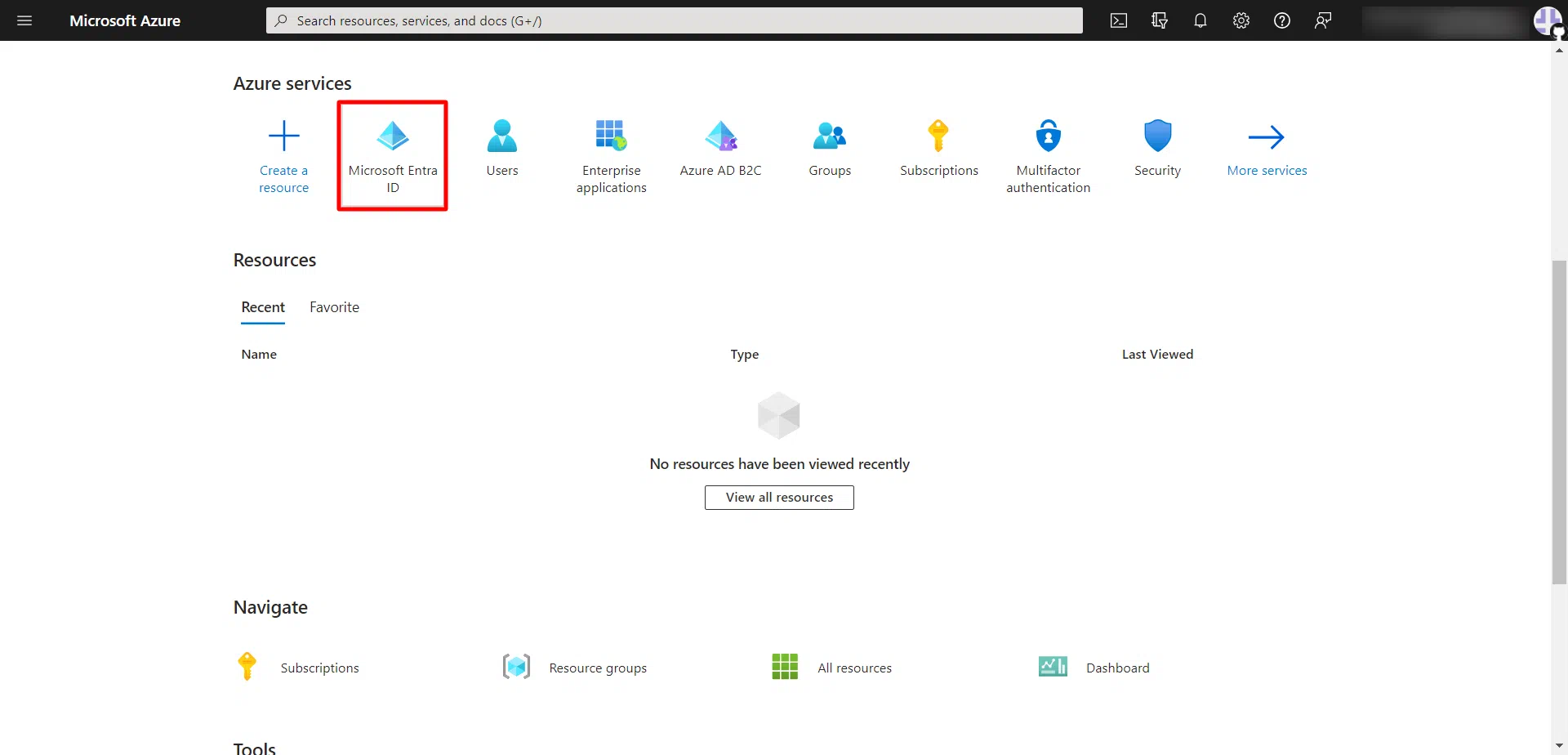
- Log into the Azure portal.
- Click on Microsoft Entra ID under Azure services.
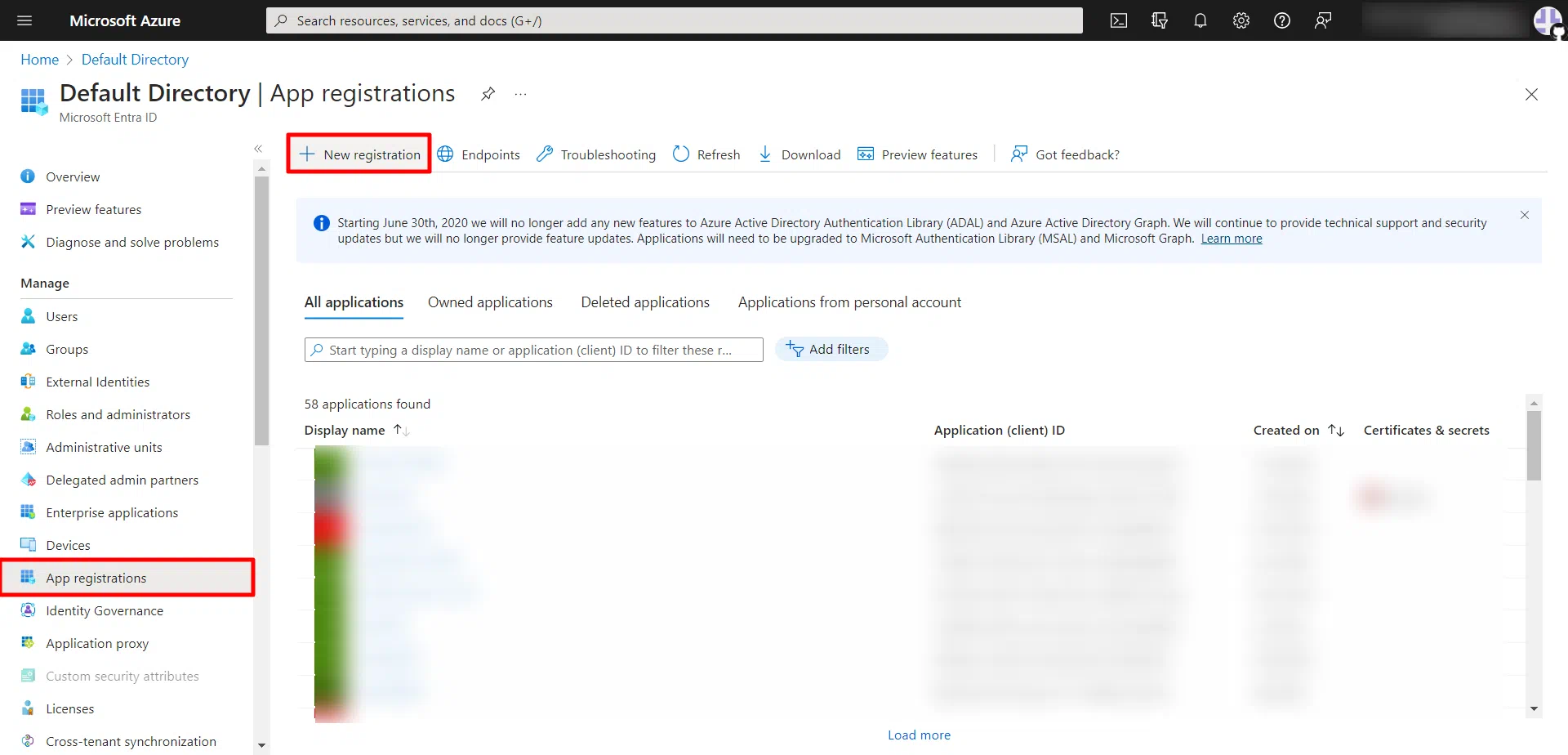
- In the left-hand navigation pane, click the App registrations, and click on New registration.
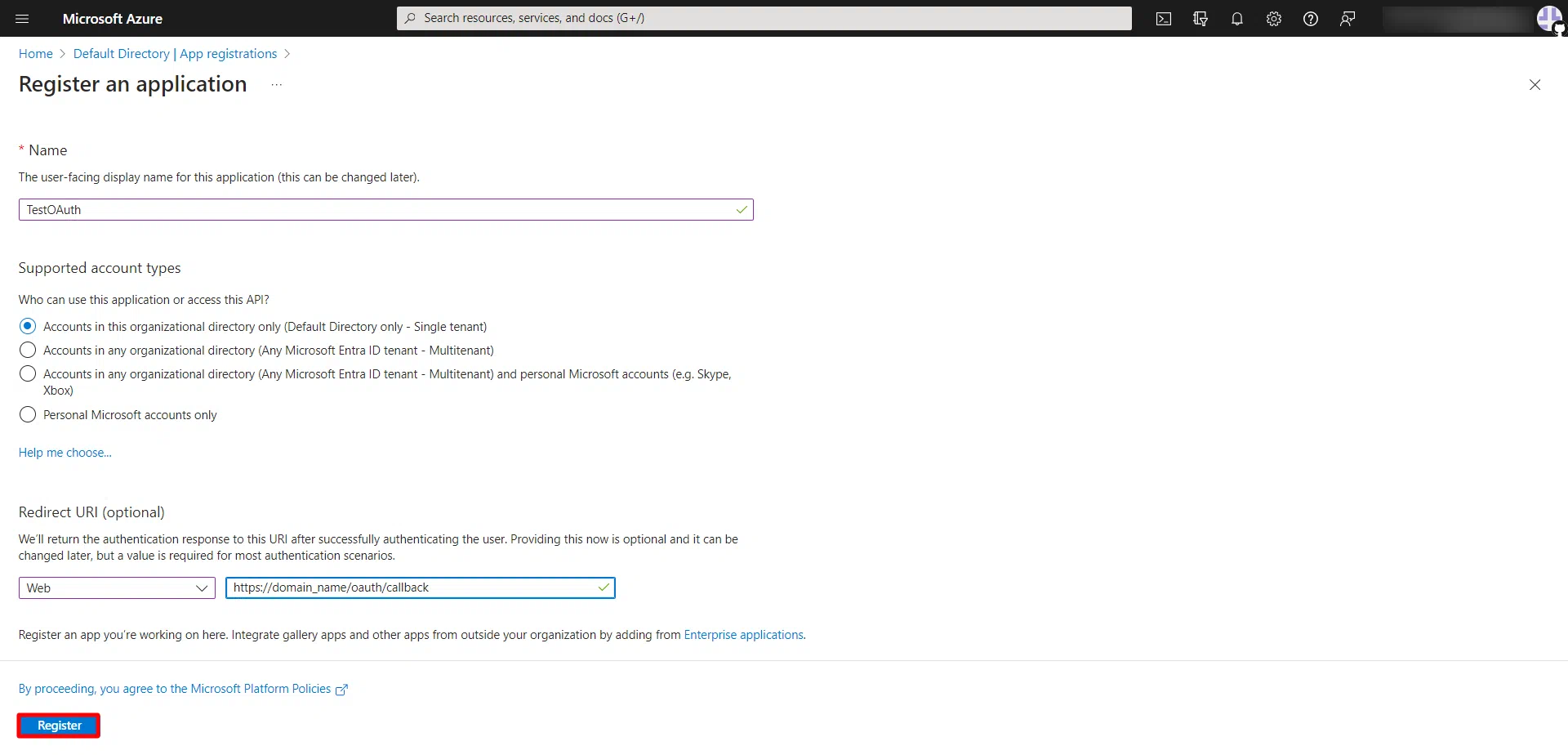
- When the Create page appears, enter your application's registration information:
- Select "Native" for client applications that are installed locally on a device. This setting is used for OAuth public native clients
- Select "Web app / API" for client applications and resource/API applications that are installed on a secure server. This setting is used for OAuth confidential web clients and public user-agent-based clients. The same application can also expose both a client and resource/API.
- For "Web app / API" applications, provide the base URL of your app. eg, https://<domain-name>/mo_login might be the URL for a web app running on your local machine. Users would use this URL to sign in to a web client application.
-
For "Native" applications, provide the URI used by Azure AD to return token
responses. Enter a value specific to your application.
eg, https://localhost/joomla - Under Redirect URL, select Web from the dropdown and enter the Callback URL copied earlier in the given field. Then, click on the Register button to register the new application.
| Name: Name of your application. |
|
Application type : |
|
Sign-on URL : |
2. Configure Client ID and Secret
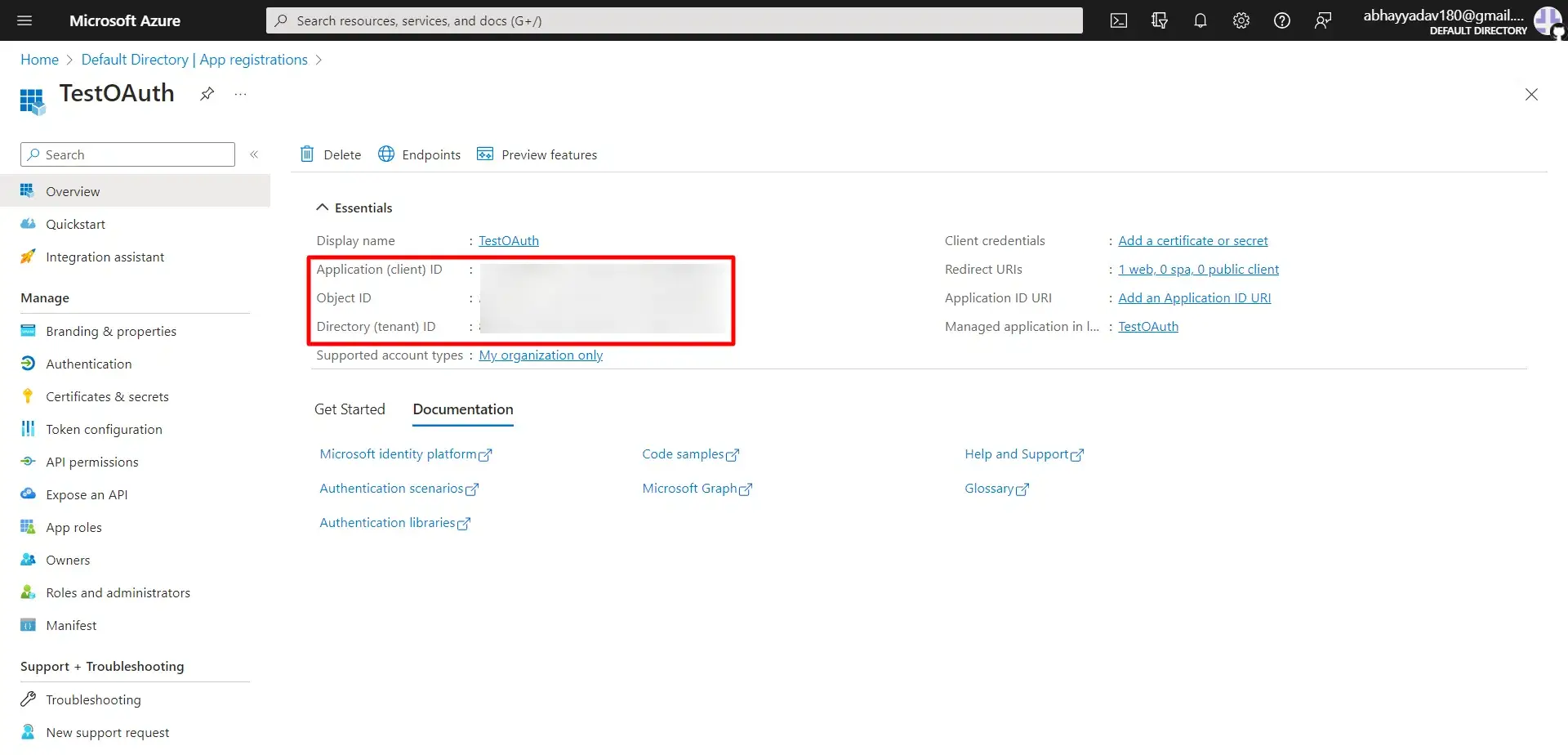
- Now go to the Overview tab of your registered application. Here, copy the Application ID and the Directory ID, this will be your Client ID and Tenant ID respectively.
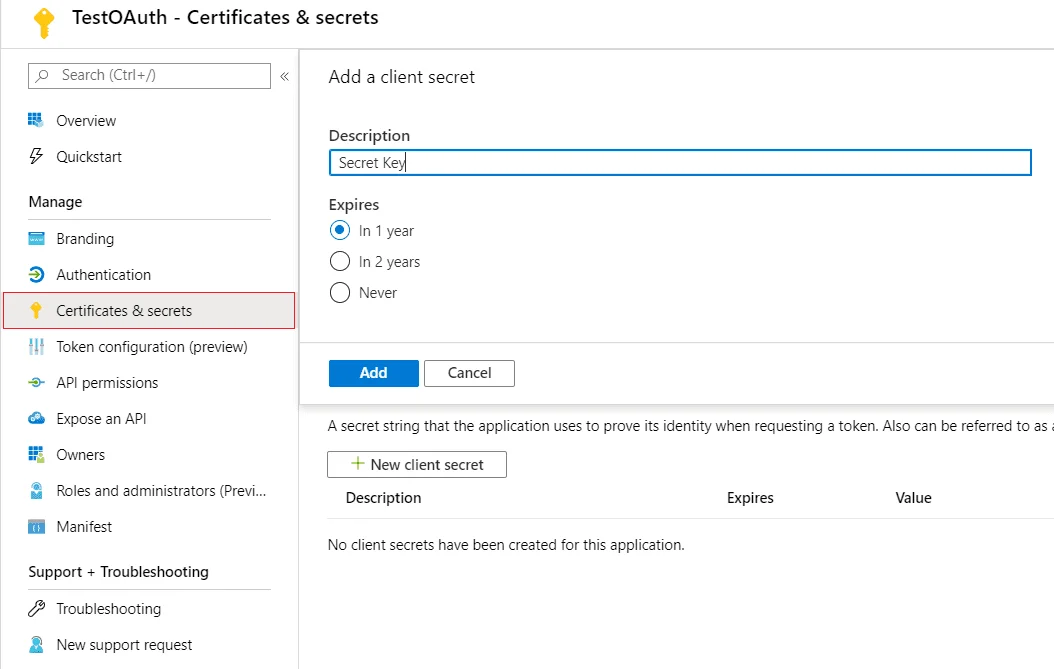
- Go to Certificates and Secrets from the left navigation pane and click on New Client Secret. Enter description and expiration time and click on Add option.
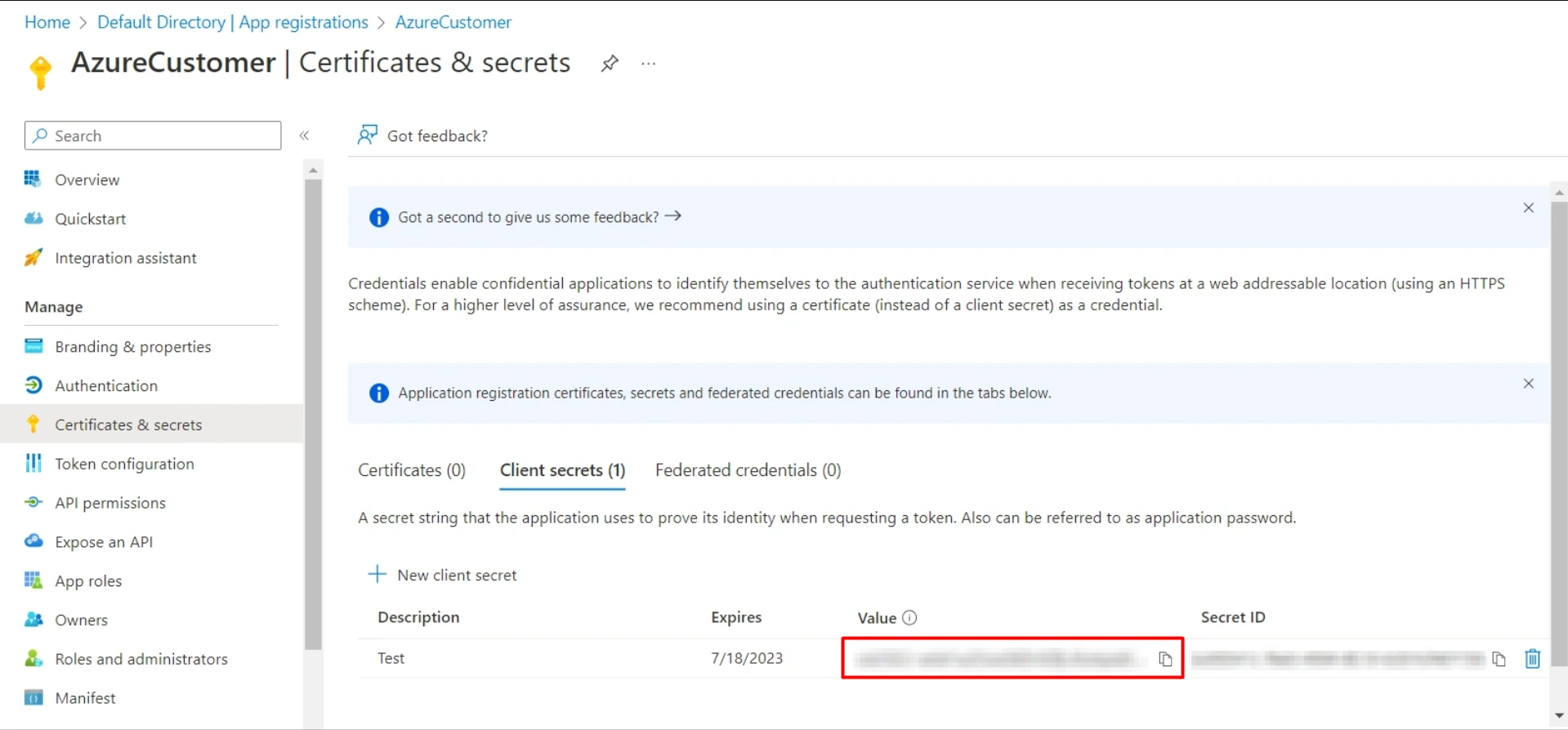
- Copy value. This will be your Client Secret.
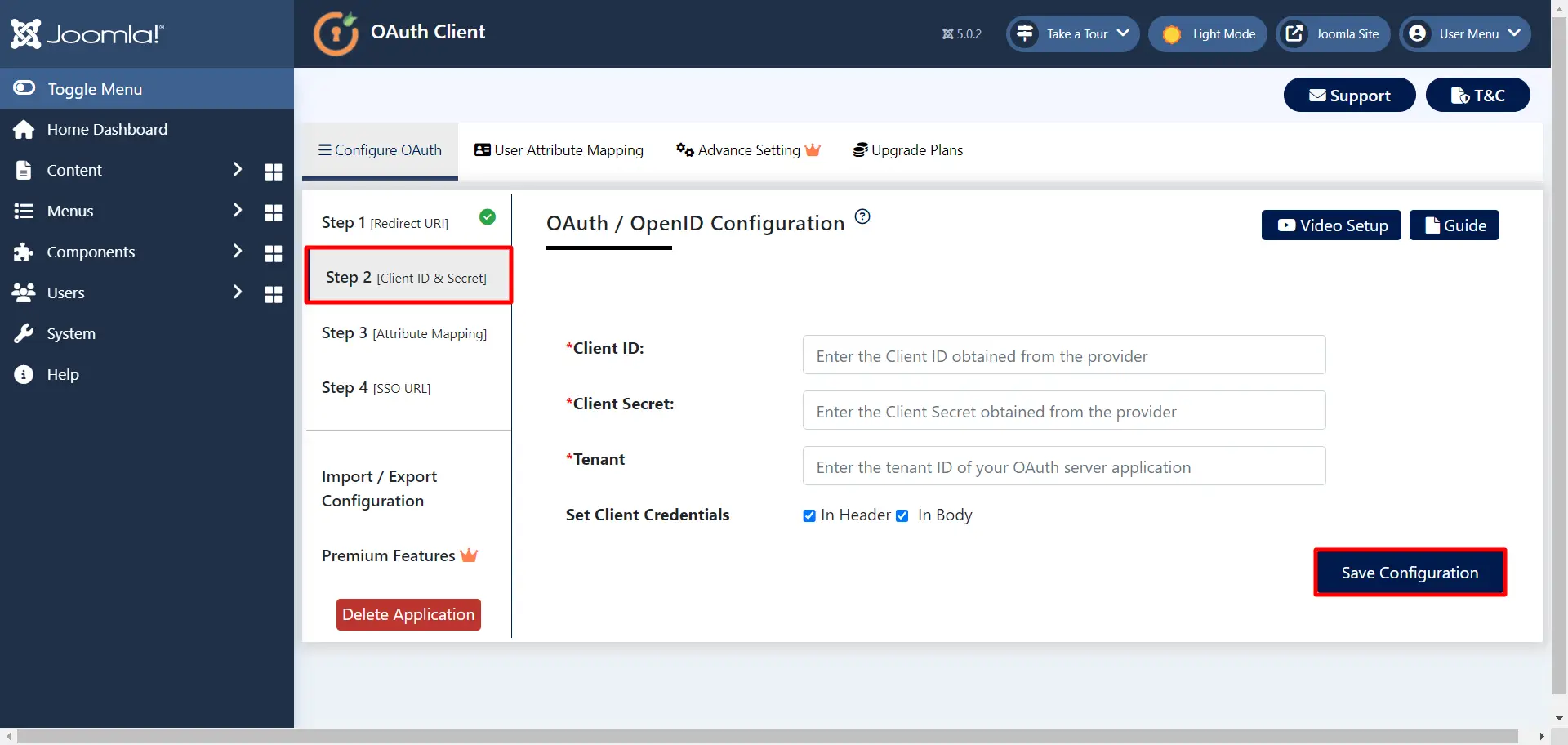
- Go to the Step 2 [Client ID & Secret] tab of the Joomla OAuth Client plugin, here paste the Client ID, Client Secret and Tenant. Click on the Save Configuration button.
2.1. Scope & Endpoints
- If you want to enable scopes, you can follow the following steps:
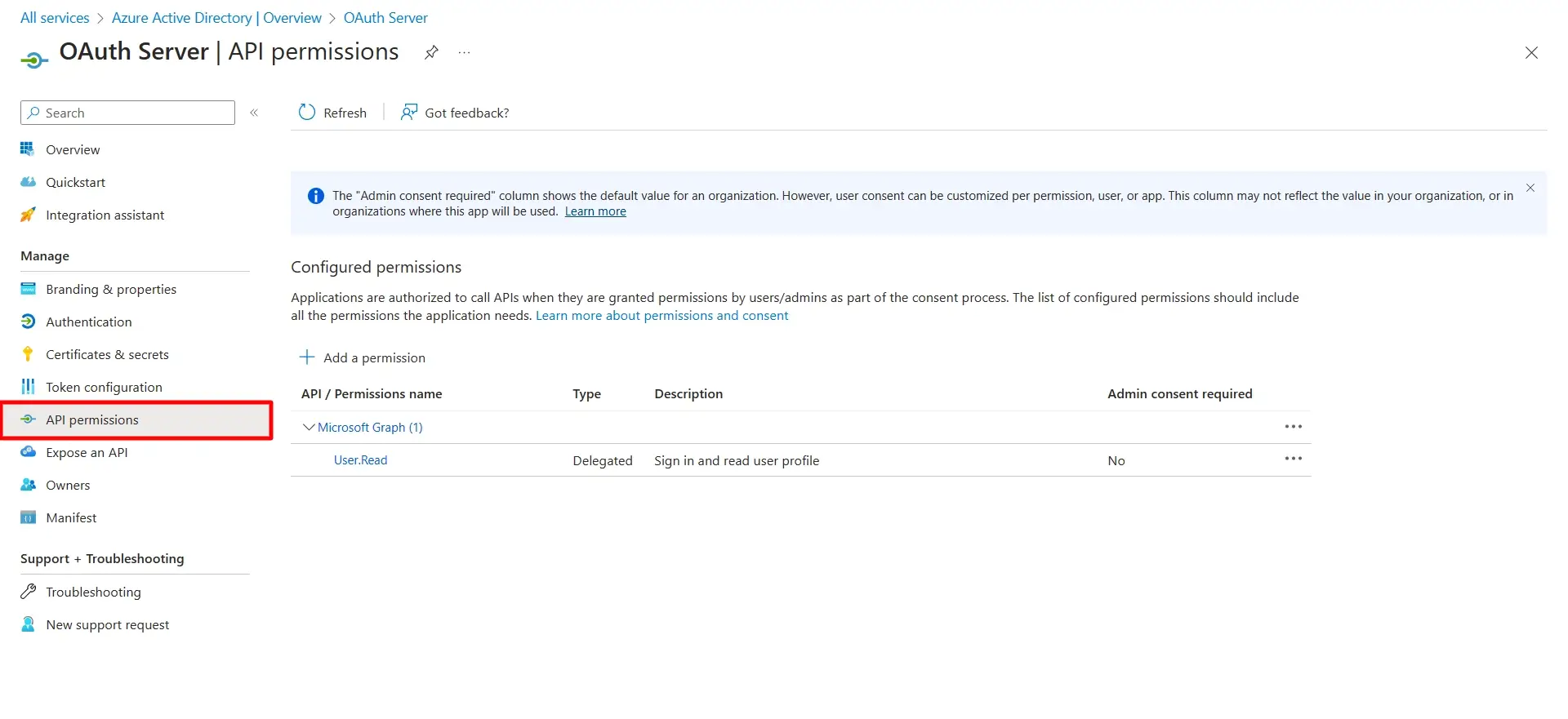
- Go to Application -> Select the application where you want to enable scopes. Now, Go to the API Permissions tab.
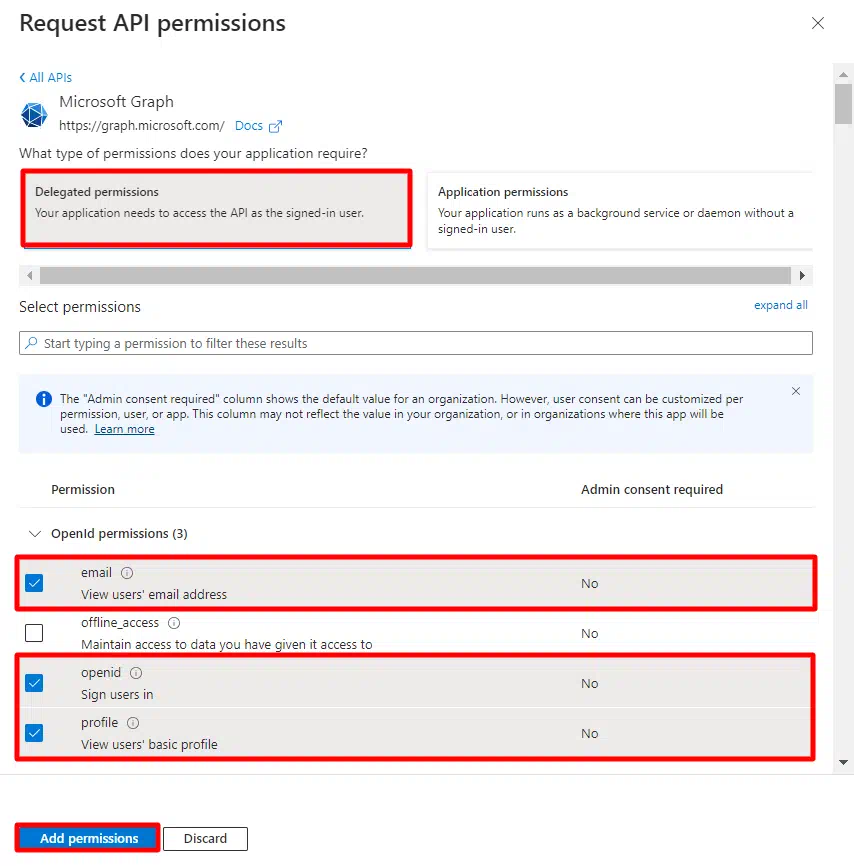
- Click on the Add permission button, and then Microsoft Graph API -> Delegated Permissions and select openid, Profile scope and click on the Add Permissions button.
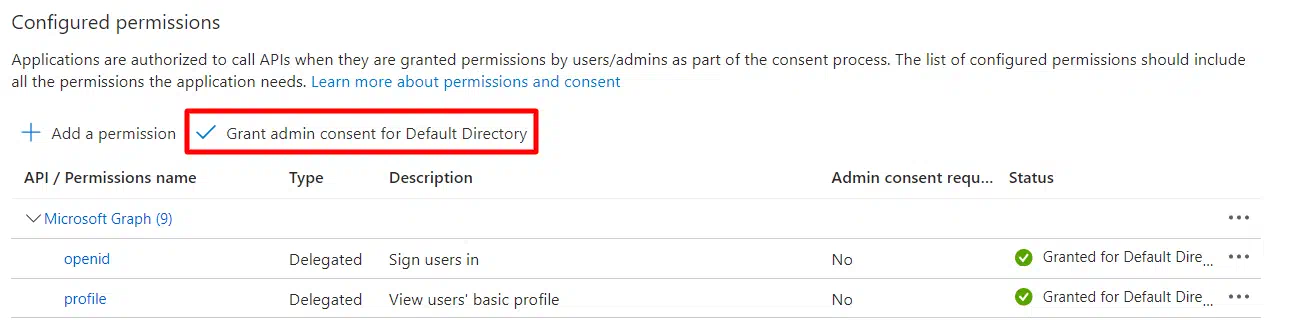
- Click on the Grant admin consent for default directory for Demo button.
- Azure AD Endpoints and Scope:
|
Scope:
openid email profile
|
|
Authorize Endpoint:
https://login.microsoftonline.com/[tenant-id]/oauth2/v2.0/authorize
|
|
Access Token Endpoint:
https://login.microsoftonline.com/[tenant-id]/oauth2/v2.0/token
|
|
Get User Info Endpoint:
https://graph.microsoft.com/beta/me
|
|
Set Client Credentials:
In Both (In Header and In Body)
|
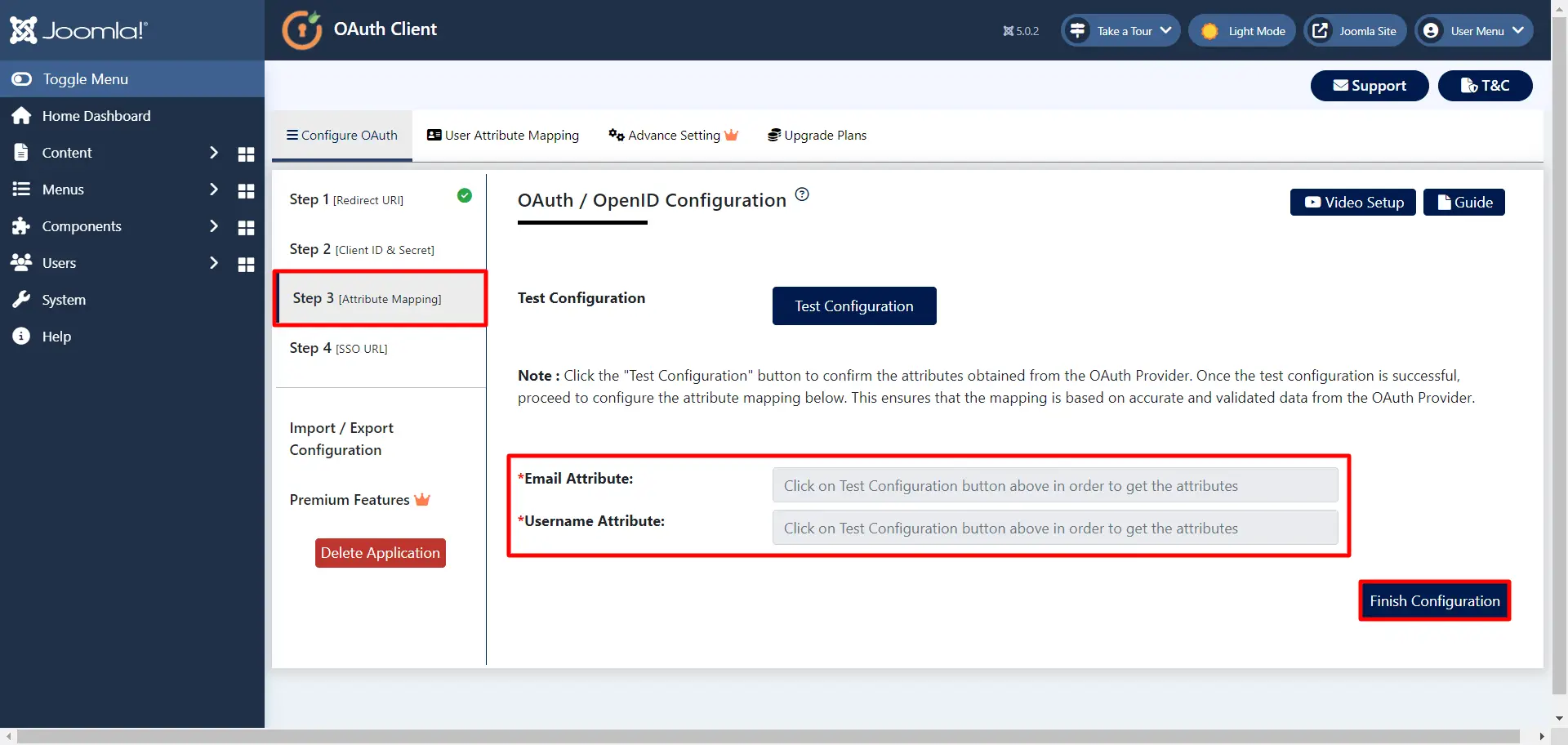
3. Configure Attribute Mapping
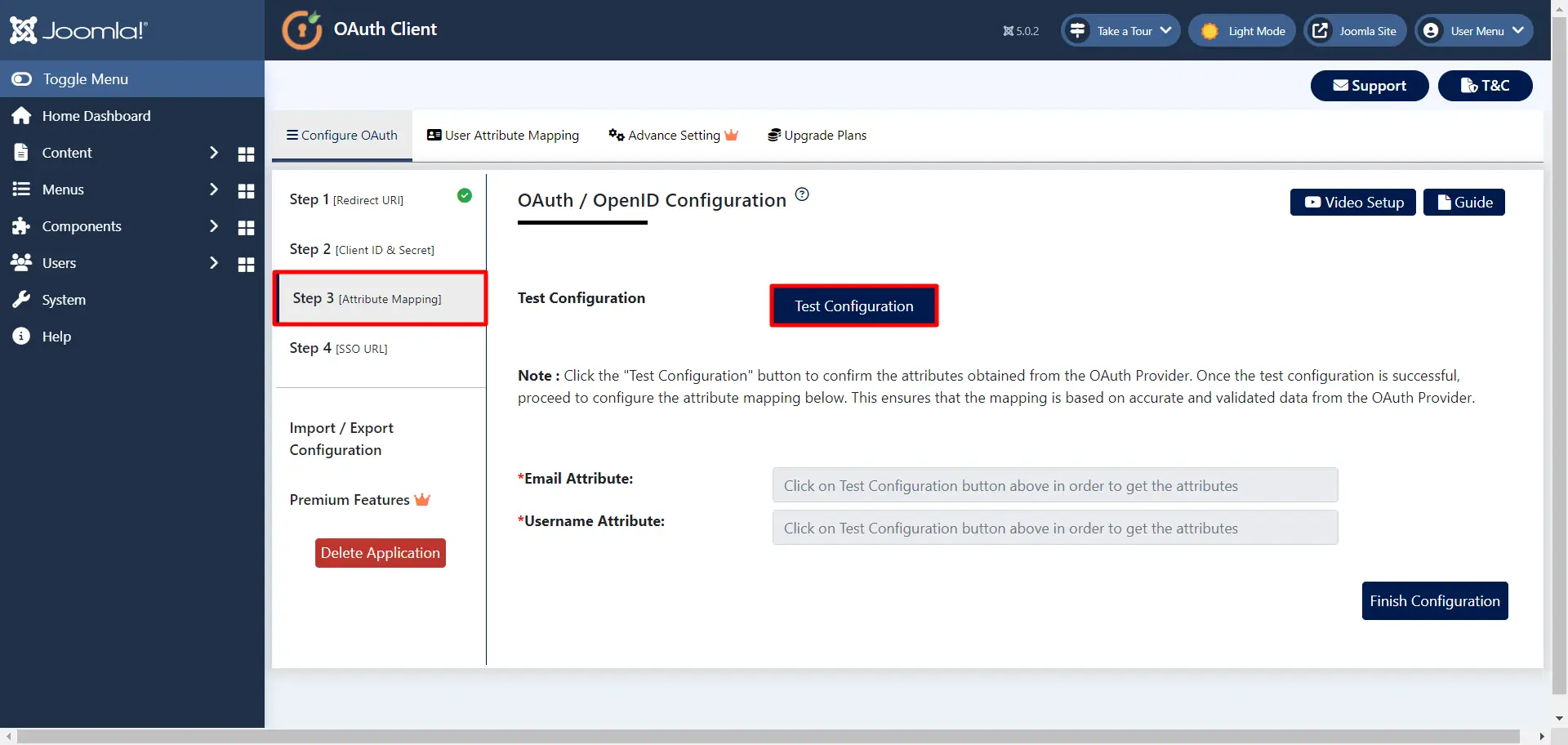
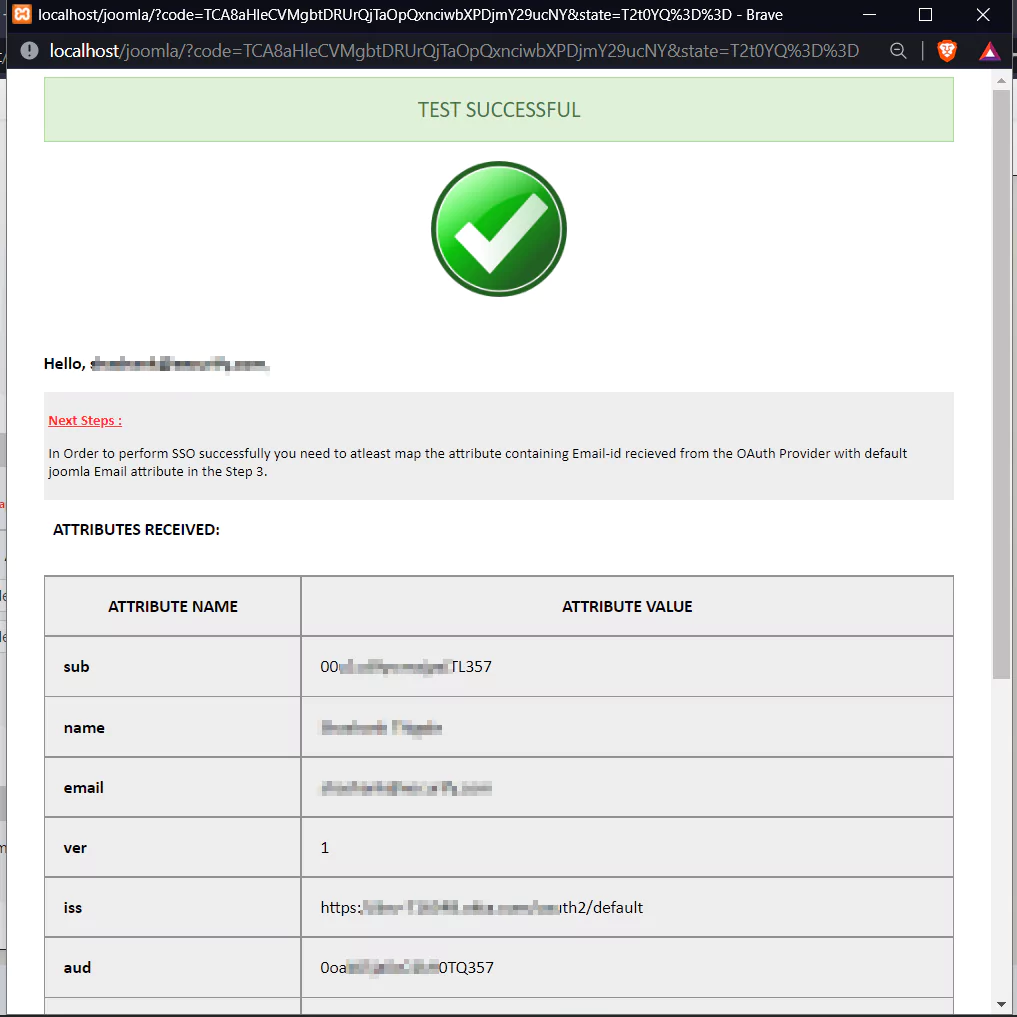
- Go to Step 3 [Attribute Mapping] tab and click on Test Configuration button.
- You will be able to see the attributes in the Test Configuration output as follows.
- Now go to the Step 3 [Attribute Mapping] tab and Select the attribute name for Email and Username from dropdown. Then click on Finish Configuration button.
User Attribute Mapping is mandatory for enabling users to successfully login into Joomla. We will be setting up user profile attributes for Joomla using below settings.
4. Setup Login/SSO URL
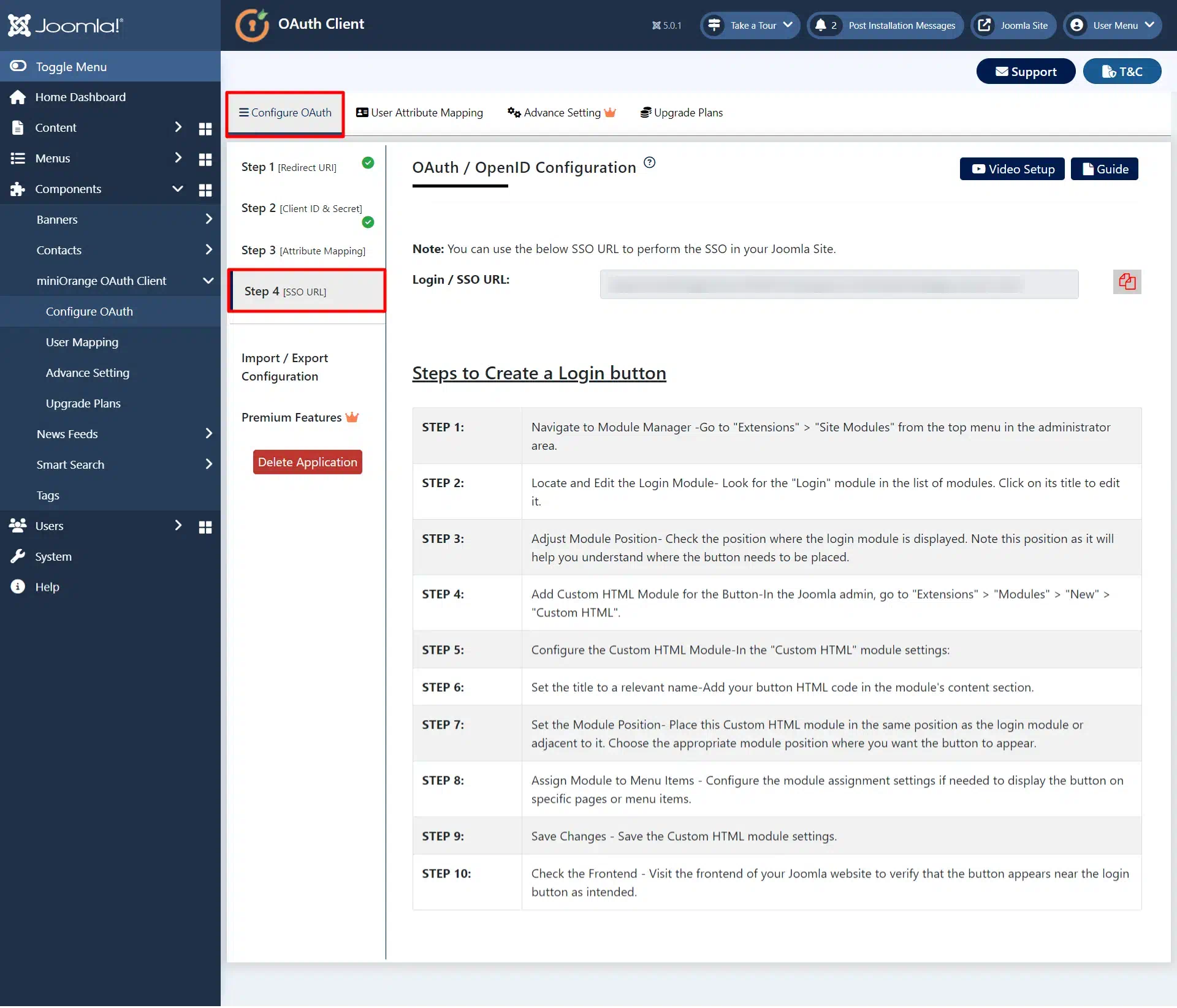
- Now go to Step 4 [SSO URL] tab, here copy the Login/SSO URL and add it to your Site by following the given steps.
- Now logout and go to your Joomla site's pages where you have added this link. You will see a login link where you placed that button. Click on this button to perform SSO.
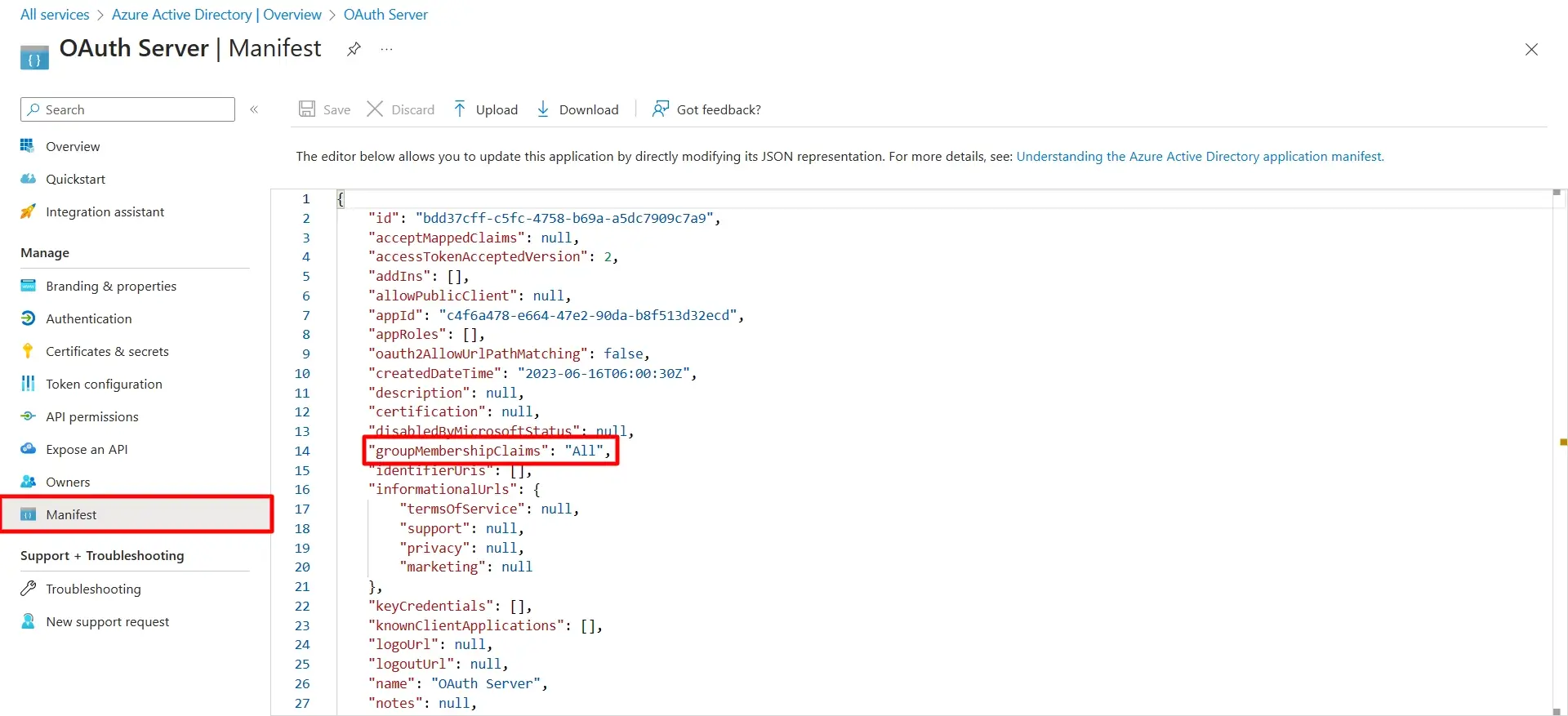
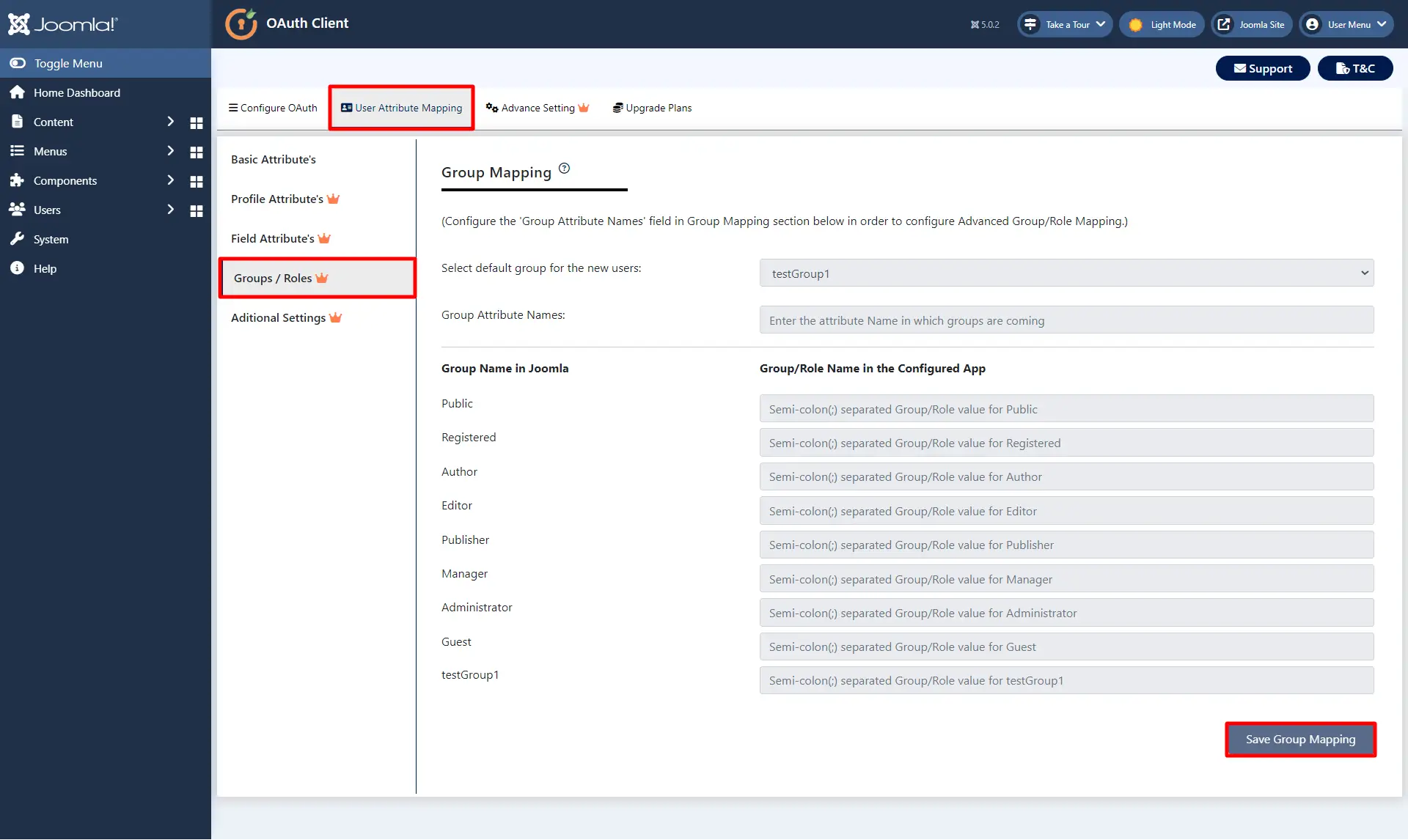
5. Configure Group/Role Mapping
- Go to Manifest tab and find groupMembershipClaims and changes it’s value to "All" and click on the save button.
- Now go to the User Attribute Mapping tab in Joomla OAuth CLient plugin, and click on Group/Roles tab from the left hand bar. Here, you can configure the 'Group Attribute Names' field in order to configure Advanced Group/Role Mapping. Then click on the Save Group Mapping button.
In this guide, you have successfully configured Joomla Azure AD Single Sign-On (SSO) by configuring Azure AD as OAuth Provider and Joomla as OAuth Client using our Joomla OAuth Client plugin.This solution ensures that you are ready to roll out secure access to your Joomla site using Azure AD login credentials within minutes.
Frequently Asked Questions
How does Azure AD OAuth Single Sign-On (SSO) enhance security for Joomla applications?
Azure AD OAuth SSO enhances security by allowing apps to access resources without needing user credentials. It ensures proper authentication and authorization, reducing the risk of exposing user passwords and enhancing control over access.
What is the difference between authentication and authorization in the context of Azure AD OAuth SSO?
Authentication verifies the identity of a user, while authorization determines what actions a user or application is allowed to perform. Azure AD OAuth handles both aspects: it authenticates the user and grants the app appropriate permissions.
Can I use Azure AD OAuth SSO to grant different levels of access to my application?
Yes, you can define different scopes (permissions) that determine the level of access an application has to user resources. Users can grant consent for specific scopes during the OAuth flow.
What are the different OAuth flows supported by Azure AD?
Azure AD supports several OAuth flows, including the Authorization Code Flow, Implicit Flow, Client Credentials Flow, Device Code Flow, and Resource Owner Password Credentials (ROPC) Flow.
When should I use the Authorization Code Flow?
The Authorization Code Flow is recommended for server-side applications that can securely store a client secret. It involves redirecting the user to Azure AD for authentication and authorization, and then exchanging the authorization code for an access token.
What is the Implicit Flow and when is it appropriate to use?
The Implicit Flow is suitable for single-page applications (SPAs) and JavaScript-based applications. It returns the access token directly to the client after user authentication.
How do I define custom scopes for my Azure AD OAuth-enabled application?
Custom scopes can be defined in the application registration's "Expose an API" section. You can then request these custom scopes in your OAuth requests.
Can scopes be dynamically requested during the OAuth flow?
Yes, some OAuth flows, such as the Authorization Code Flow, allow for dynamic scope selection based on user consent. This helps ensure users grant only the necessary permissions.
Why am I repeatedly prompted for consent when trying to use an app?
Consent prompts might occur if the app's permissions haven't been properly configured in Azure AD. Make sure the app's required permissions are granted by the admin, and the app's redirect URIs are accurate.
What does the "invalid_grant" error mean during token exchange? [May occur during test configuration?]
This error indicates that the authorization code or refresh token being used is invalid, expired, or has been used before. Make sure you're using the correct tokens and following the proper OAuth flow.
Why am I getting a "redirect_uri_mismatch" error?
This error occurs when the redirect URI used in the authorization request doesn't match the one registered in Azure AD. Verify that the URIs match exactly, including the protocol and domain. [You can mention where to get the correct redirect URL]
Why do my access tokens keep expiring?
Access tokens have a limited validity period for security reasons. To mitigate this, consider using refresh tokens to obtain new access tokens without requiring user interaction.
Why can't I authorize the app in my Azure AD tenant?
Check if your Azure AD tenant settings are correctly configured for OAuth. If you're not the admin, contact your organization's admin for assistance.
Why does my app require admin approval in some tenants?
Some permissions might require admin consent. Users should contact their admin for approval if needed.
Why can't I connect to the Azure AD tenant for OAuth?
Check your internet connection and ensure you have proper access to the Azure AD portal.
Why does the app require different configurations for each tenant?
Each tenant operates independently, and Azure AD enforces strict separation. This is to ensure the security and privacy of each organization's data.
Joomla Azure Integrator
Additional Resources
- What is OAuth 2.0?
- Frequently Asked Questions (FAQs)
- How to configure OAuth / OpenID Connect SSO with Salesforce
- How to configure OAuth / OpenID Connect SSO with AWS Cognito
- How to configure OAuth / OpenID Connect SSO with Discord
- How to configure OAuth / OpenID Connect SSO with Facebook
- How to configure OAuth / OpenID Connect SSO with Google Apps
- How to configure OAuth / OpenID Connect SSO with Instagram
- How to configure OAuth / OpenID Connect SSO with Keycloak
Mail us on joomlasupport@xecurify.com for quick guidance(via email/meeting) on your requirement and our team will help you to select the best suitable solution/plan as per your requirement.
Need Help? We are right here!

Thanks for your inquiry.
If you dont hear from us within 24 hours, please feel free to send a follow up email to info@xecurify.com
Cookie Preferences
Cookie Consent
This privacy statement applies to miniorange websites describing how we handle the personal information. When you visit any website, it may store or retrieve the information on your browser, mostly in the form of the cookies. This information might be about you, your preferences or your device and is mostly used to make the site work as you expect it to. The information does not directly identify you, but it can give you a more personalized web experience. Click on the category headings to check how we handle the cookies. For the privacy statement of our solutions you can refer to the privacy policy.
Strictly Necessary Cookies
Always Active
Necessary cookies help make a website fully usable by enabling the basic functions like site navigation, logging in, filling forms, etc. The cookies used for the functionality do not store any personal identifiable information. However, some parts of the website will not work properly without the cookies.
Performance Cookies
Always Active
These cookies only collect aggregated information about the traffic of the website including - visitors, sources, page clicks and views, etc. This allows us to know more about our most and least popular pages along with users' interaction on the actionable elements and hence letting us improve the performance of our website as well as our services.
