Contents
JBoss Keycloak SAML Single Sign-On (SSO) into Joomla
miniOrange Joomla SAML SP SSO plugin helps you to integrate your Joomla site to Keycloak using SAML 2.0 protocol. Our user-friendly plugin simplifies the process of setting up Single Sign-on (SSO) with Keycloak in Joomla, ensuring a secure login experience. This enables users to access various Joomla sites effortlessly using their Keycloak IDP credentials.
Our plugin is designed to be compatible with Joomla 3, 4 as well as 5 and works seamlessly with all SAML 2.0 compliant Identity Providers. For a detailed overview of the comprehensive features offered by the Joomla SAML SP plugin, please visit our page here. Below, we provide a step-by-step guide on configuring SAML SSO login between your Joomla site and Keycloak, with Keycloak serving as the Identity Provider (IDP) and Joomla as the Service Provider (SP).
What is SSO ?
In this context, the system responsible for authenticating users is referred to as the Identity Provider (IDP), while the system relying on the Identity Provider for authentication is known as the Service Provider (SP). When a user initiates a login attempt, the Service Provider sends a SAML request to the Identity Provider. Upon successful IDP authentication, SAML assertions containing user information are transmitted back to the Service Provider. Subsequently, the Service Provider receives the assertion, verifies it based on the Identity Provider configuration, and grants the user access to your Joomla website.
Pre-requisites: Download And Installation
Steps to Integrate Keycloak Single Sign-On (SSO) with Joomla SAML SP
1. Setup Joomla SAML SP plugin
- Download the zip file for the miniOrange SAML SP plugin for Joomla.
- Login into your Joomla site’s Administrator console.
- From left toggle menu, click on System, then under Install section click on Extensions.
- Now click on Or Browse for file button to locate and install the plugin file downloaded earlier.
- Installation of plugin is successful. Now click on Get Started!
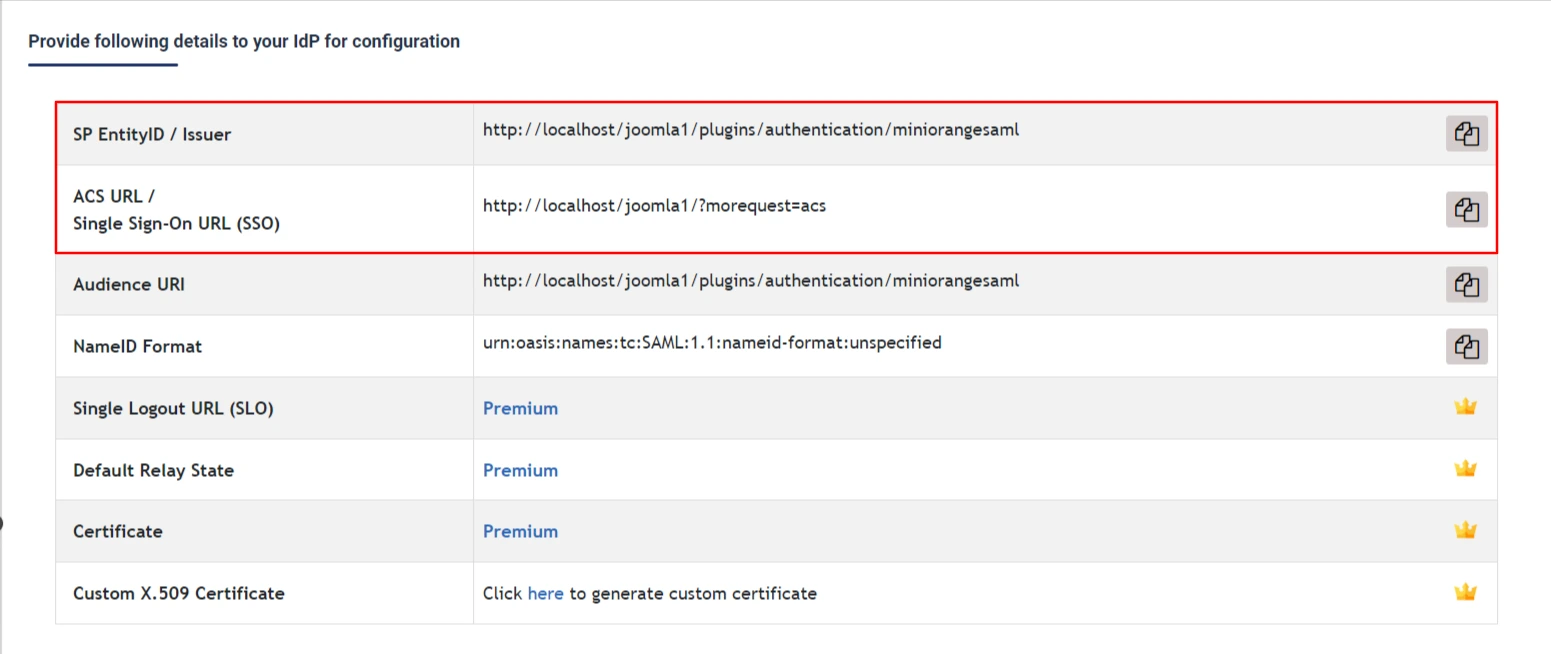
- Go to the Service Provider Metadata tab and scroll down to copy the SP-EntityID and the ACS URL.
2. Configure Jboss Keycloak as IdP
- In your Keycloak admin console, select the realm that you want to use.
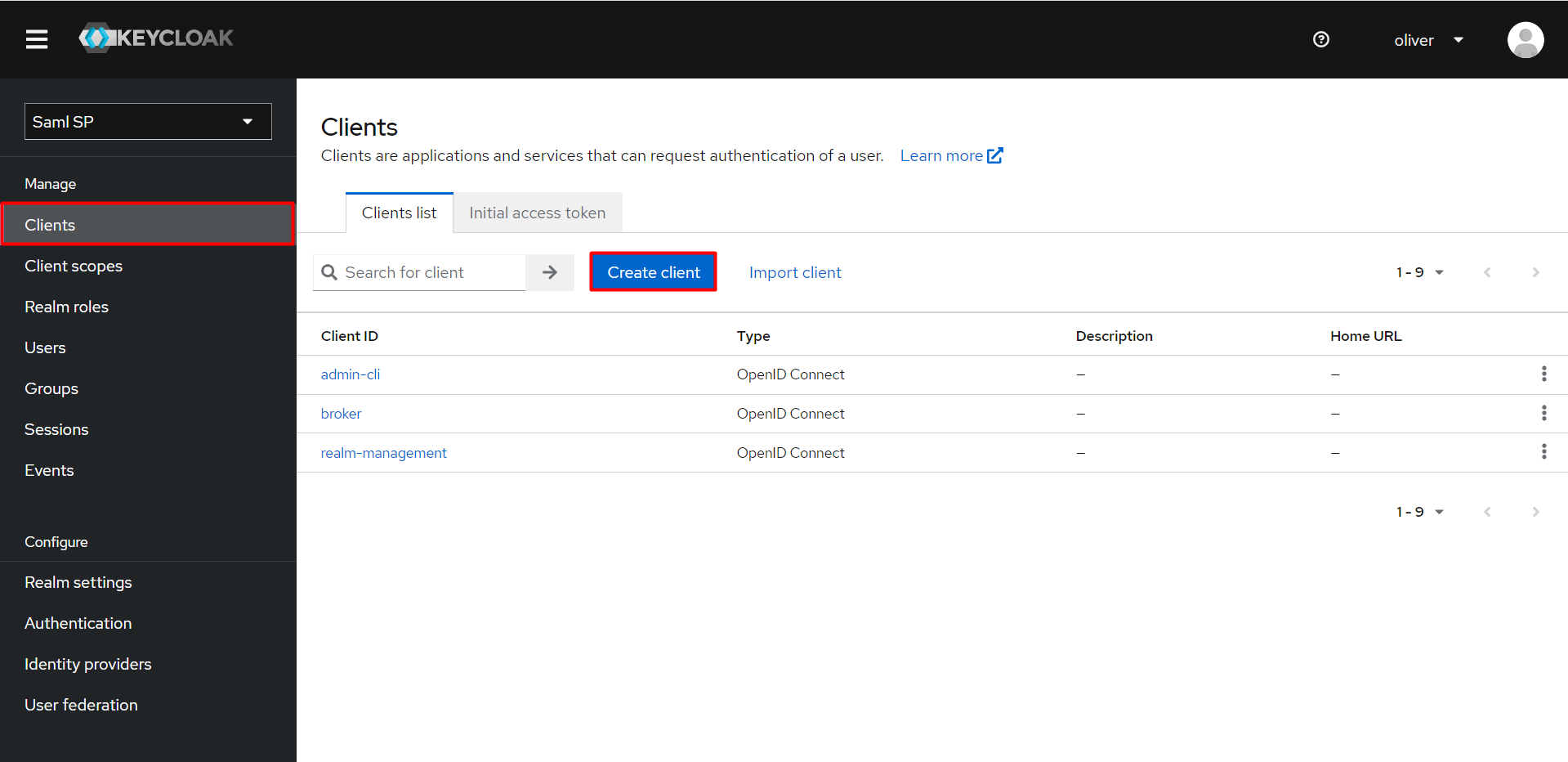
- Click on the Clients from the left navigation bar.
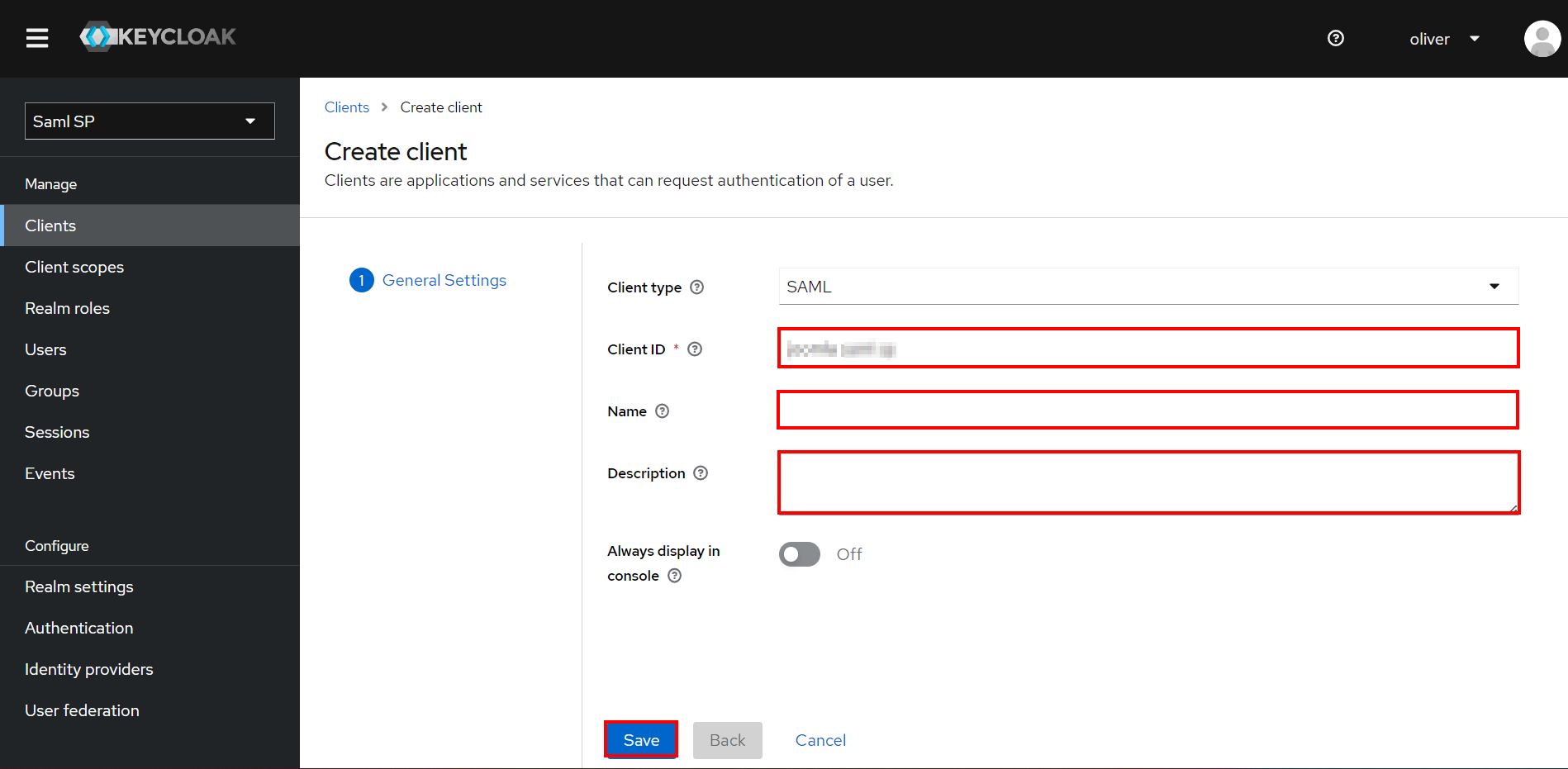
- Click on create client and enter the following values to create a client.
Client ID SP-EntityID/Issuer from Service Provider Metadata - Click on Save.
- Configure the following:
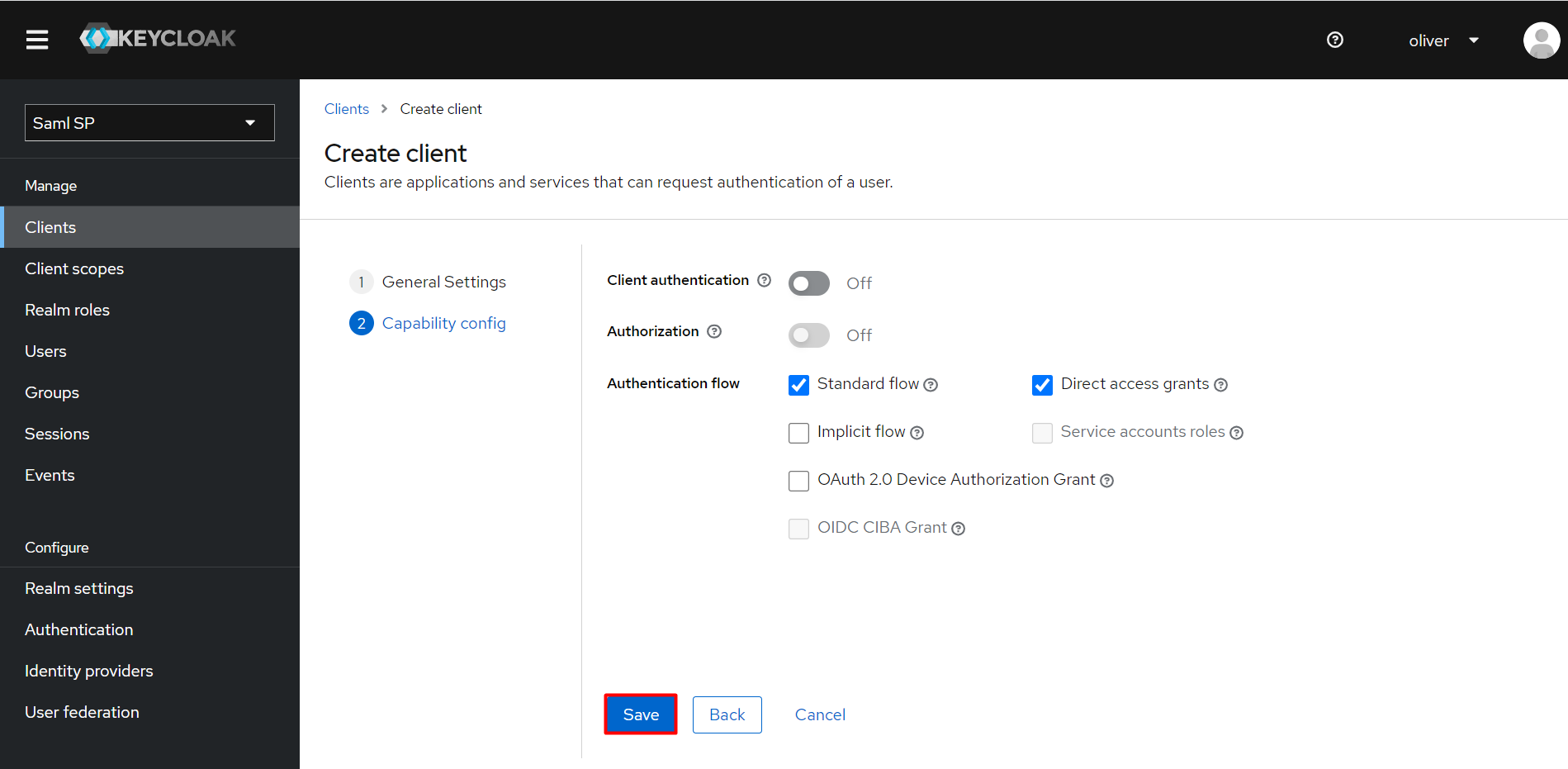
Client ID The SP-EntityID / Issuer from Service Provider Metadata Name Provide a name for this client (Eg. Joomla) Description (optional) Provide a description Enabled ON Consent Required OFF Client Protocol SAML Include AuthnStatement NO Sign Documents NO Optimize Redirect signing key lookup OFF Sign Assertions NO Signature Algorithm RSA_SHA256 Encrypt Assertion OFF Client Signature Required OFF Client Signature Required EXCLUSIVE Force Name ID Format NO Name ID Format Email Root URL Leave empty or Base URL of Service Provider Valid Redirect URIs The ACS (Assertion Consumer Service) URL from Service Provider Metadata - Under Advanced -> Fine Grain SAML Endpoint Configuration, configure the following:
Assertion Consumer Service POST Binding URL The ACS (Assertion Consumer Service) URL from Service Provider Metadata Logout Service Redirect Binding URL The Single Logout URL from Service Provider Metadata 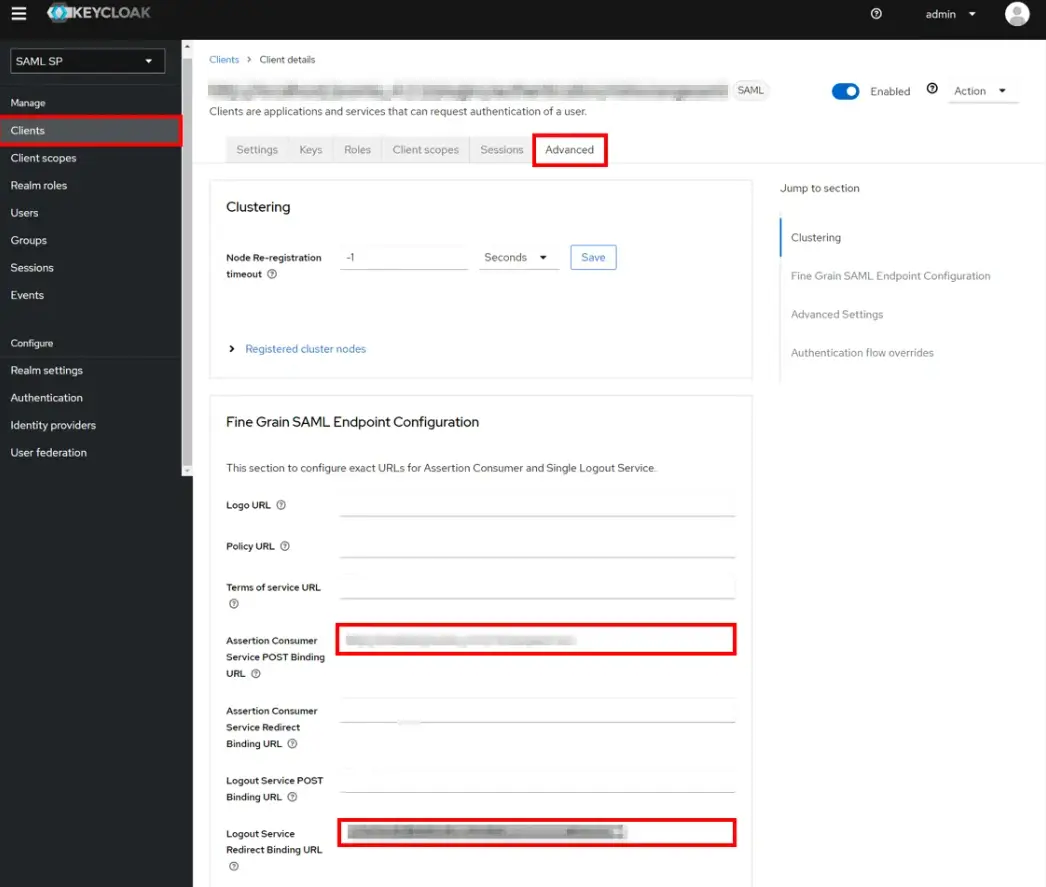
- Click on Save.
 Add Mappers
Add Mappers
- Go to the Mappers tab, and click on Add predefined mapper.
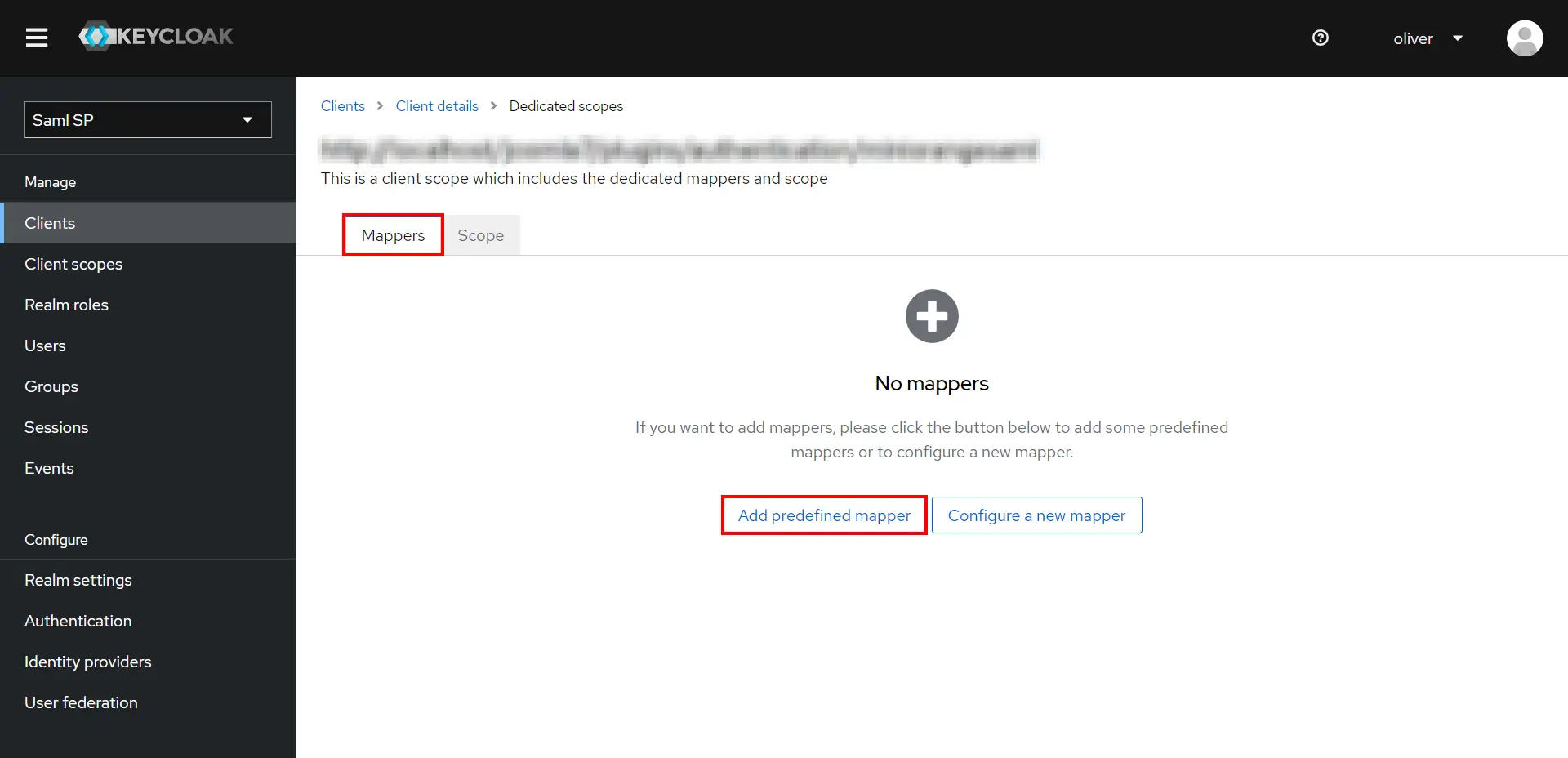
 Add User
Add User
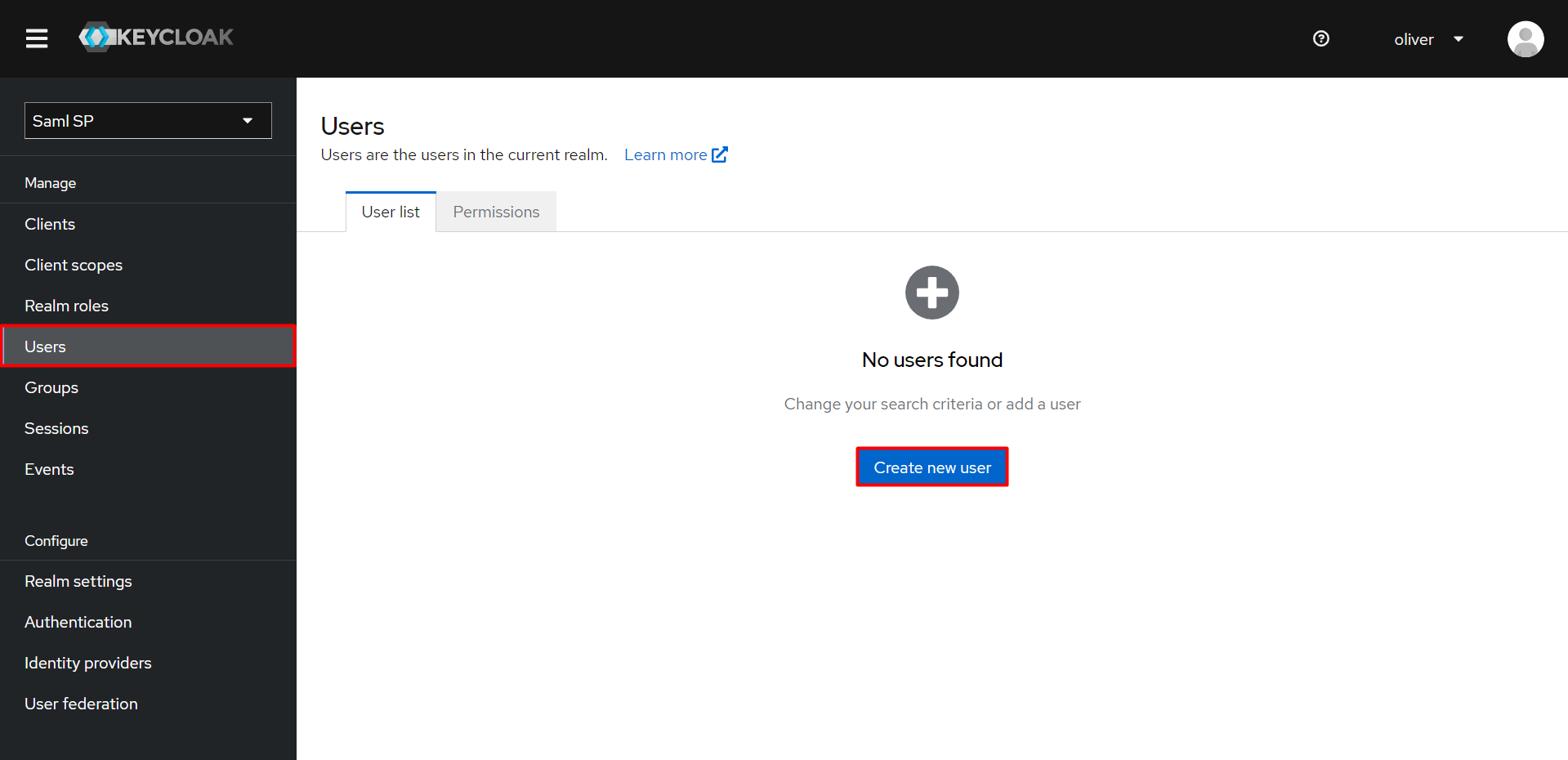
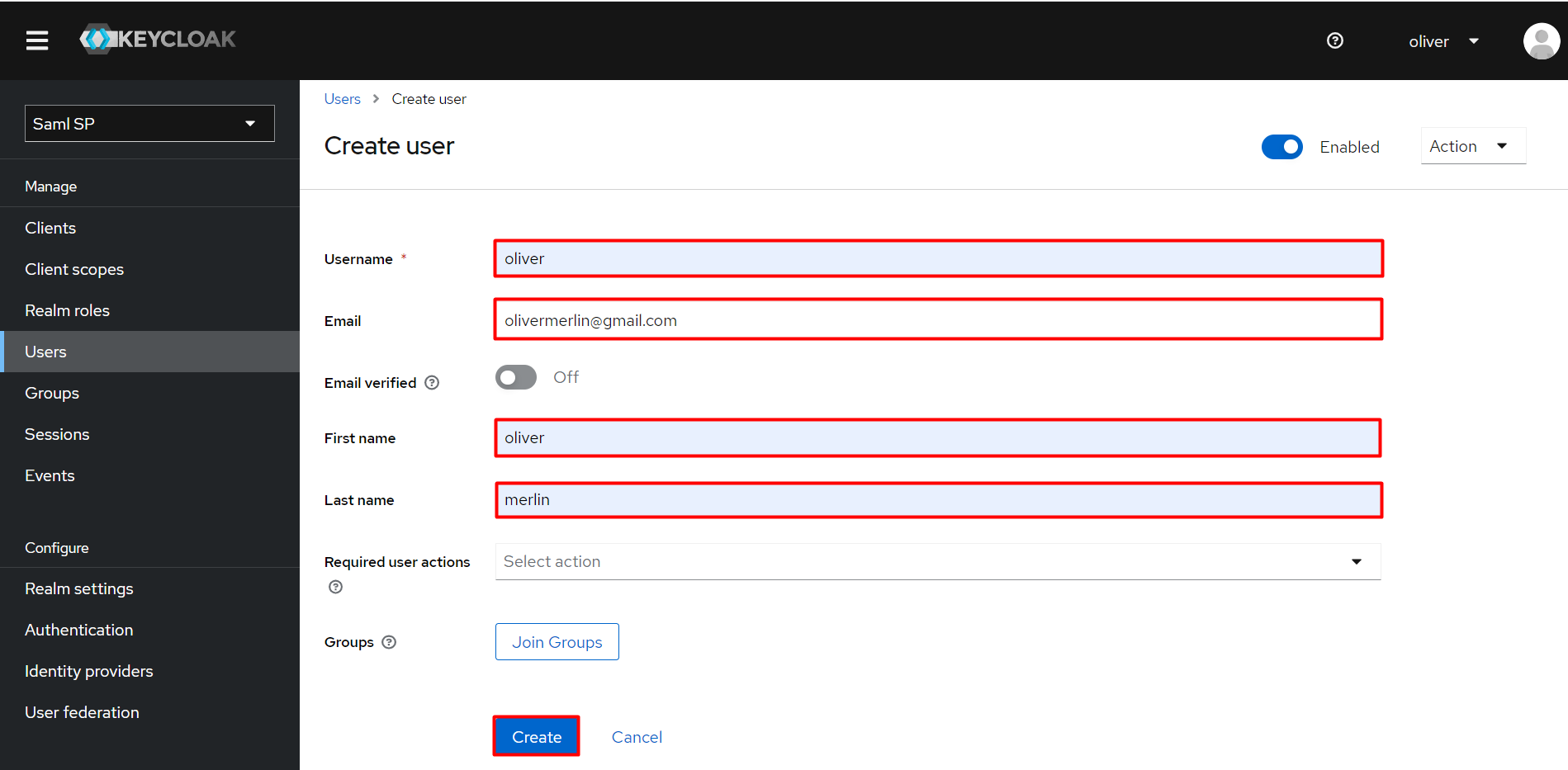
- Click on the Users from the left nav bar.
- Add a crteate New users.
- Enter the username, valid email address and check on User Enabled then enter First name & Last name.
- Click on Create button.
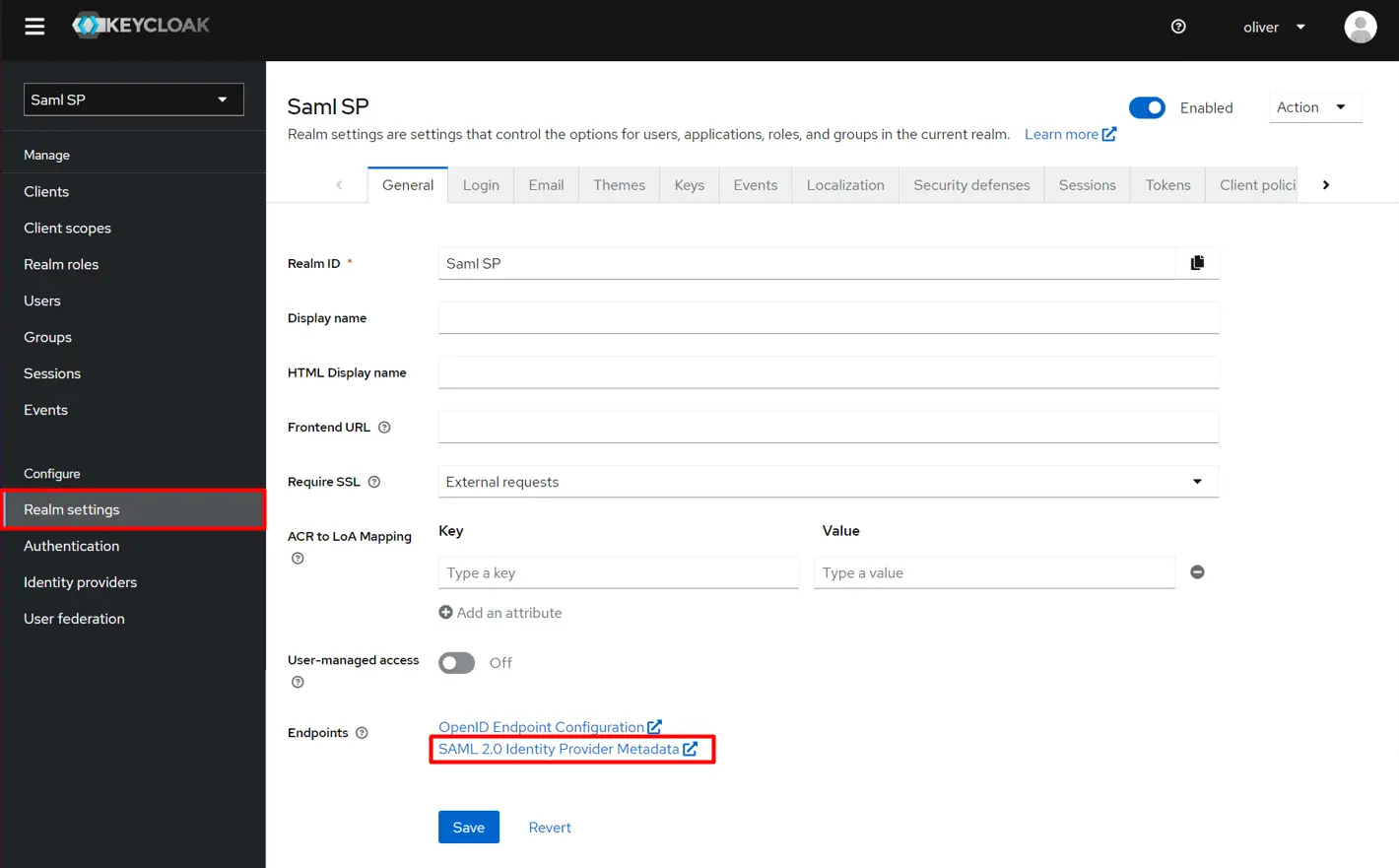
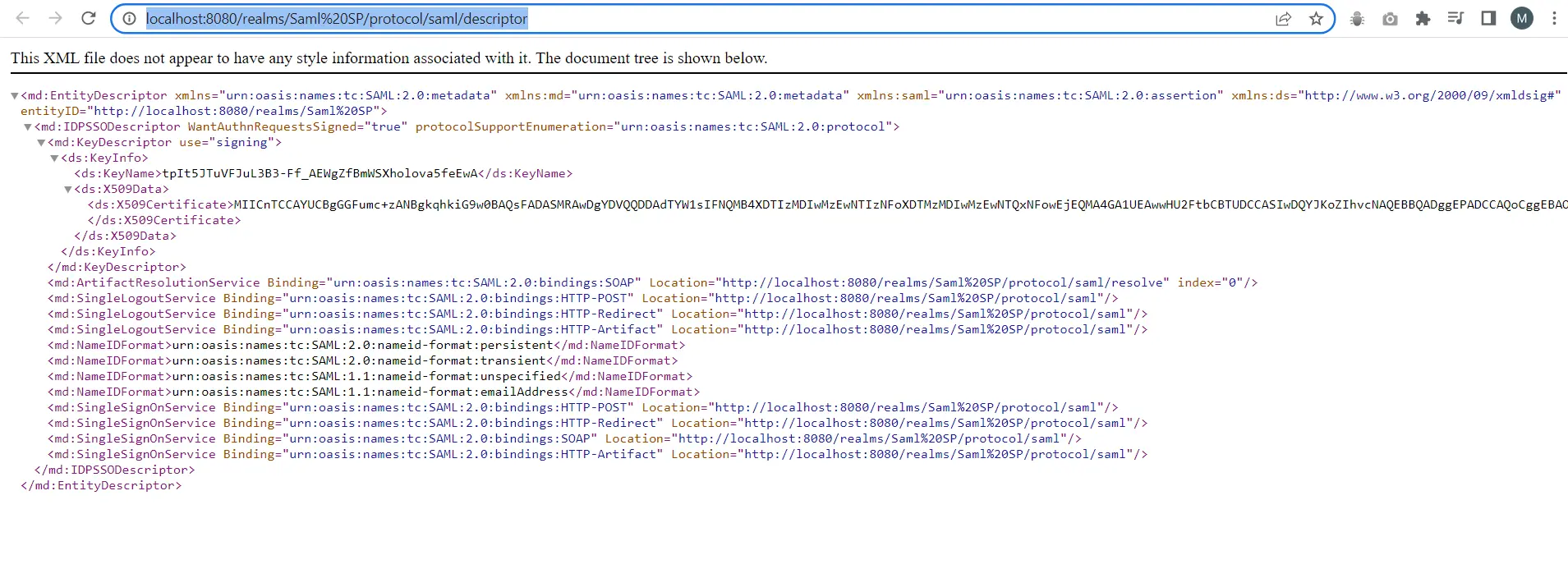
- Click on the Realm Settings from the left nav bar and open SAML 2.0 Identity Provider Metadata.
- Go to, https://<YOUR_DOMAIN>/auth/realms/{YOUR_REALM}/protocol/saml/descriptor.These will open an XML in the browser.
- In miniOrange’s Joomla SAML SP plugin, go to Service Provider Setup Tab. Enter the following values:
OR
| Identity Provider Name | Provide an Identity Provider name (For Example: Keycloak). |
| IdP Entity ID or Issuer | Search for the entityID from IDP Metadata.Enter the Value in the Entity ID textbox. |
| SAML Login URL | Search for SingleSignOnService Binding ”urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect” from IDP Metadata.Enter the location value in the SAML Login URL textbox. |
| SAML Logout URL (Optional) | Search for SingleLogoutService Binding”urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect” from IDP Metadata.Enter the location value in the SAML Login URL textbox. |
| X.509 Certificate (Optional) | Search for the X.509 Certificate from IDP Metadata.Enter the tag value in Certificate textbox. |
| Enable login with SAML | Checked |
| Signed SSO and SLO Requests | Unchecked |
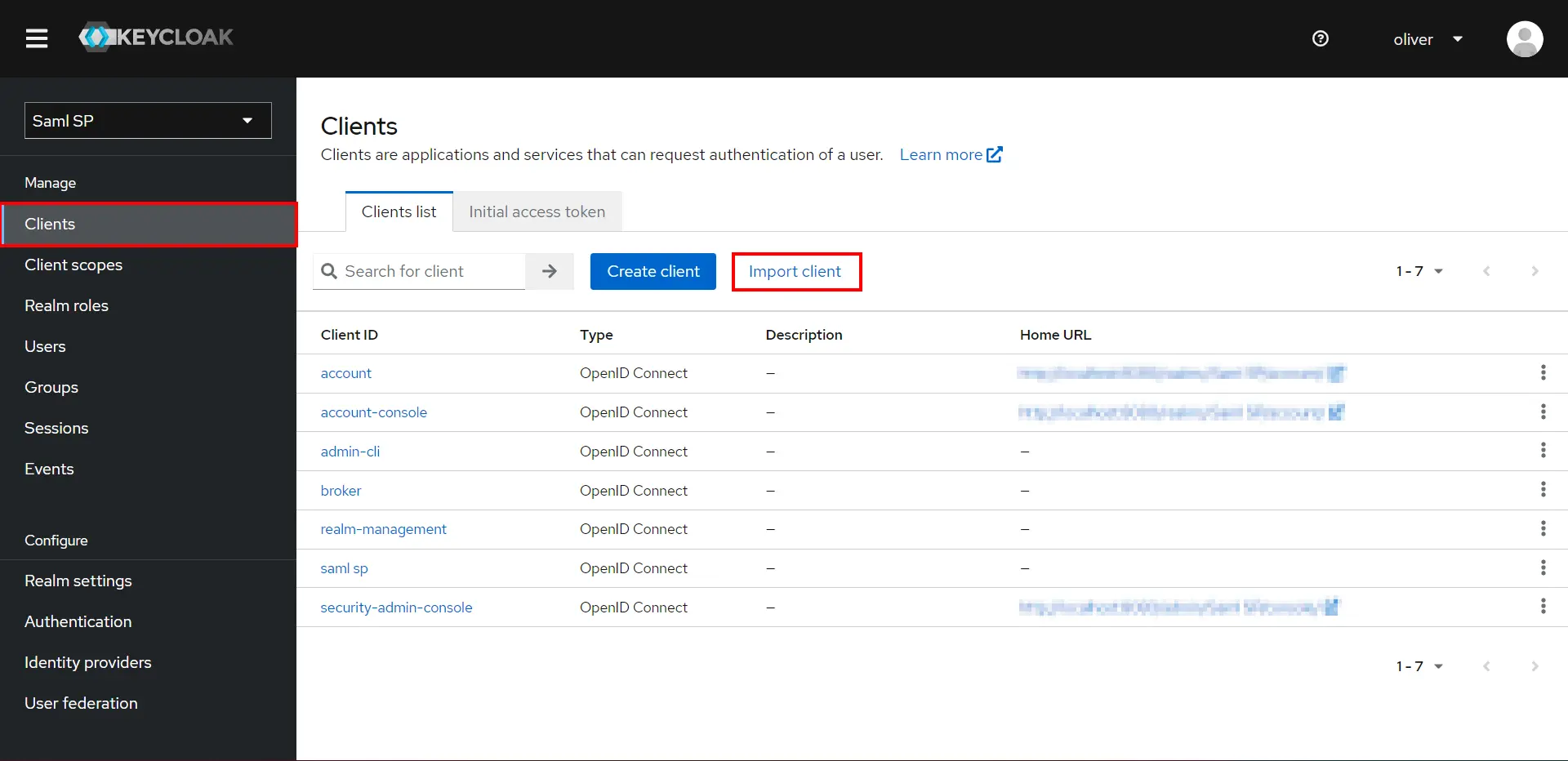
- In your Keycloak admin console, select the realm that you want to use.
- Click on Clients from the left menu and then click on Import client .
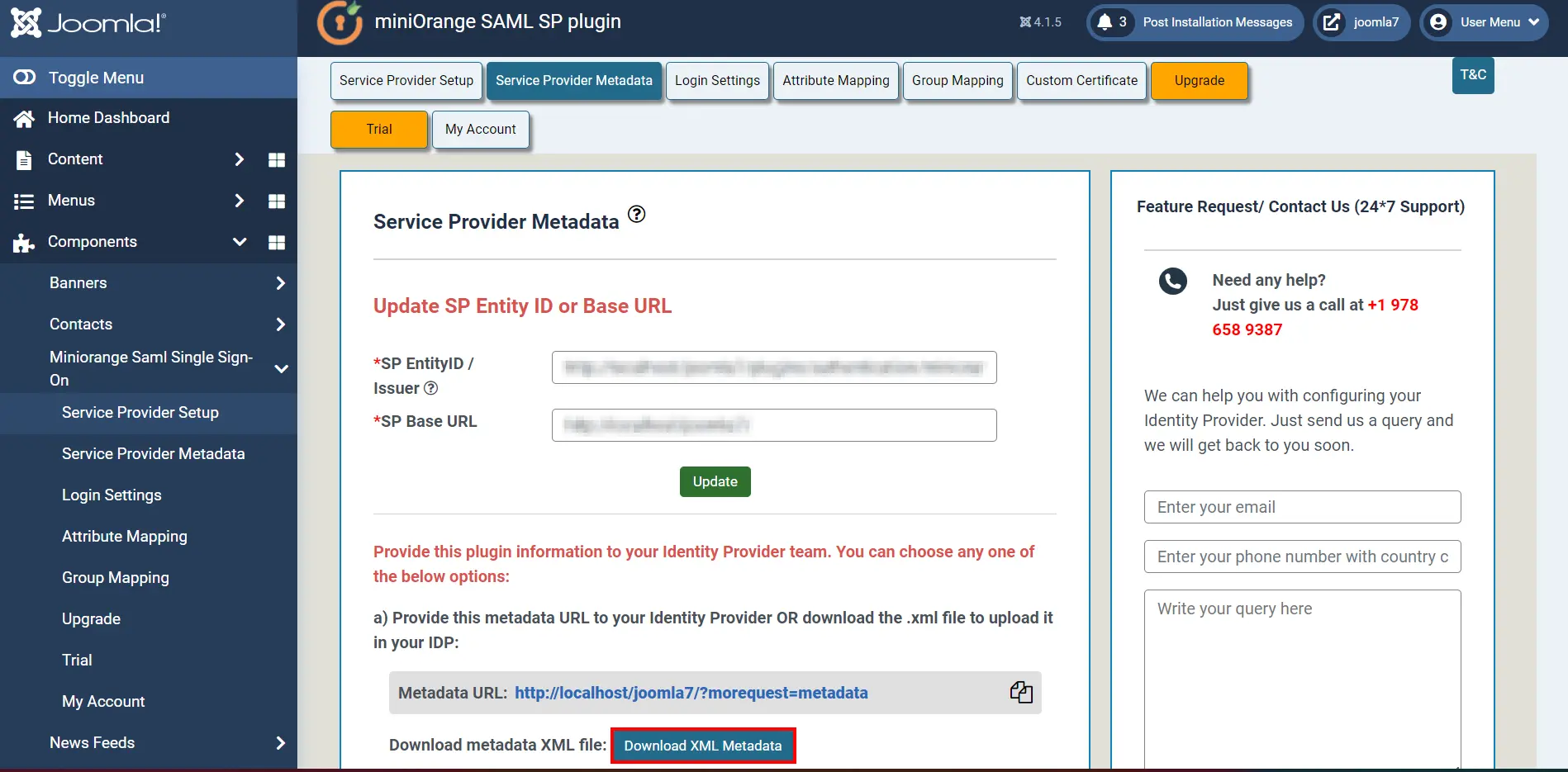
- Go to service provider Metadata tab and Download the XML File.
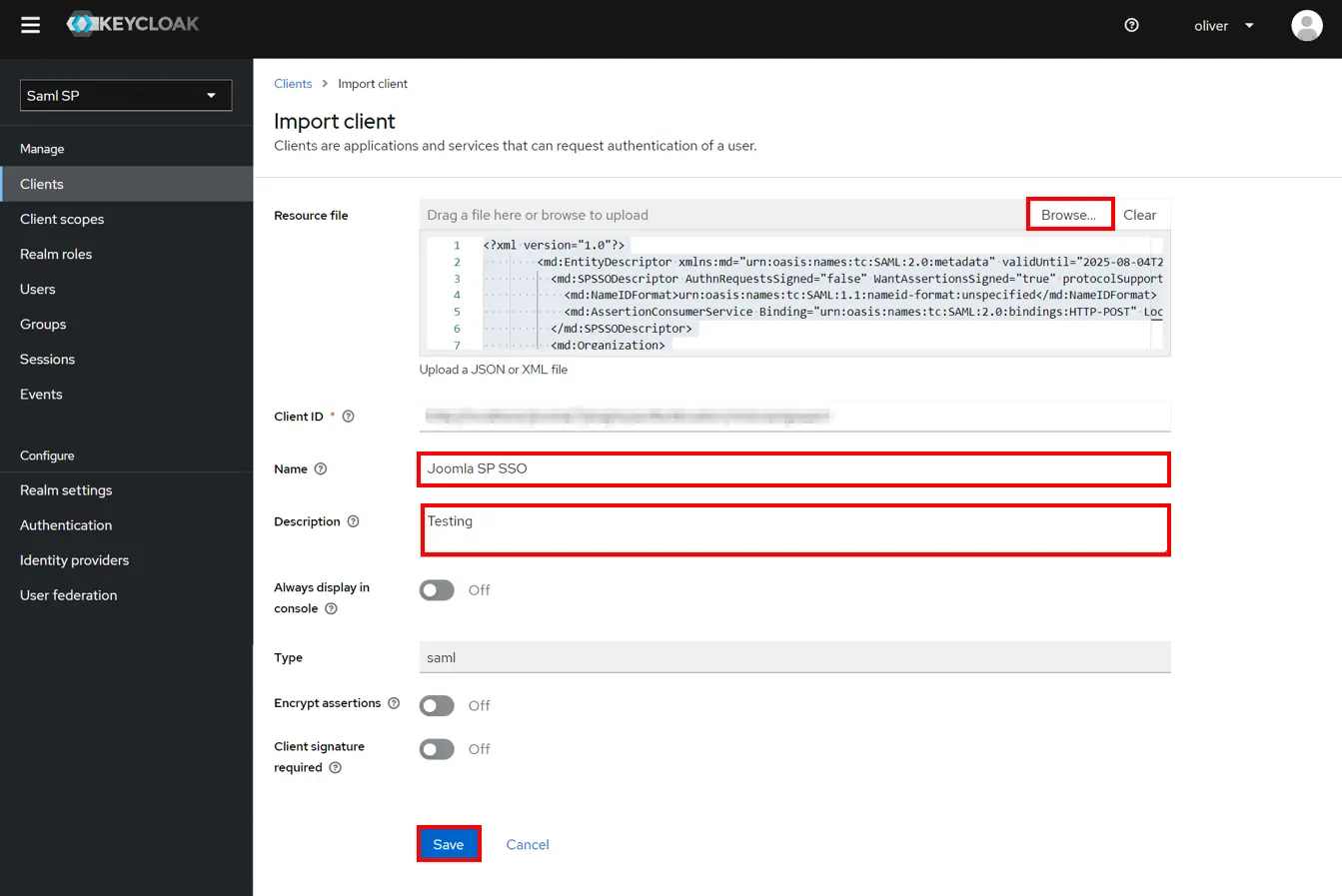
- Click on Browse tab,then Enter Name description (as per your choice)then click on save button.
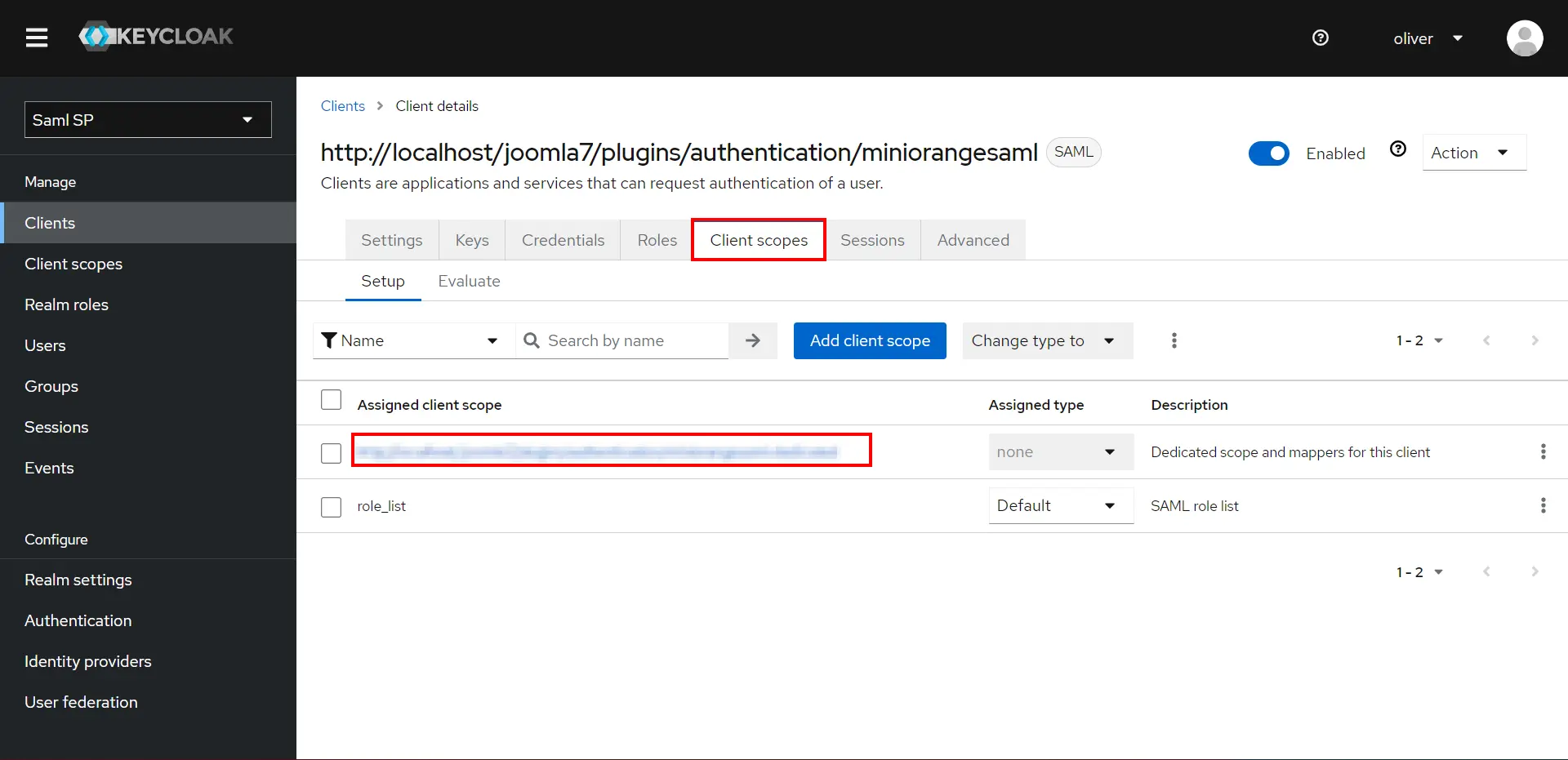
- Go to Client scope and recently added Client scope .
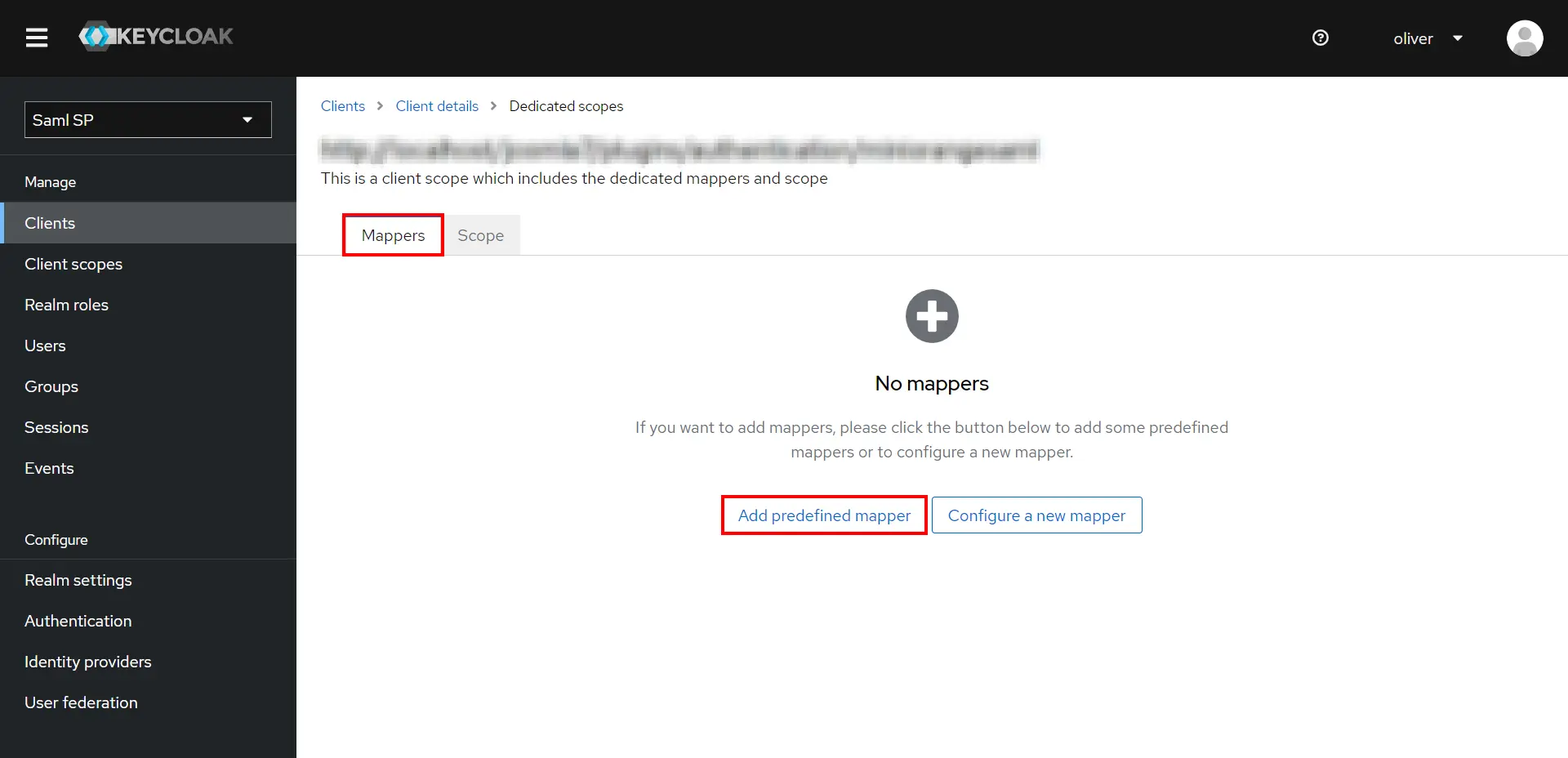
- Go to the Mappers tab, and click on Add predefined mapper.
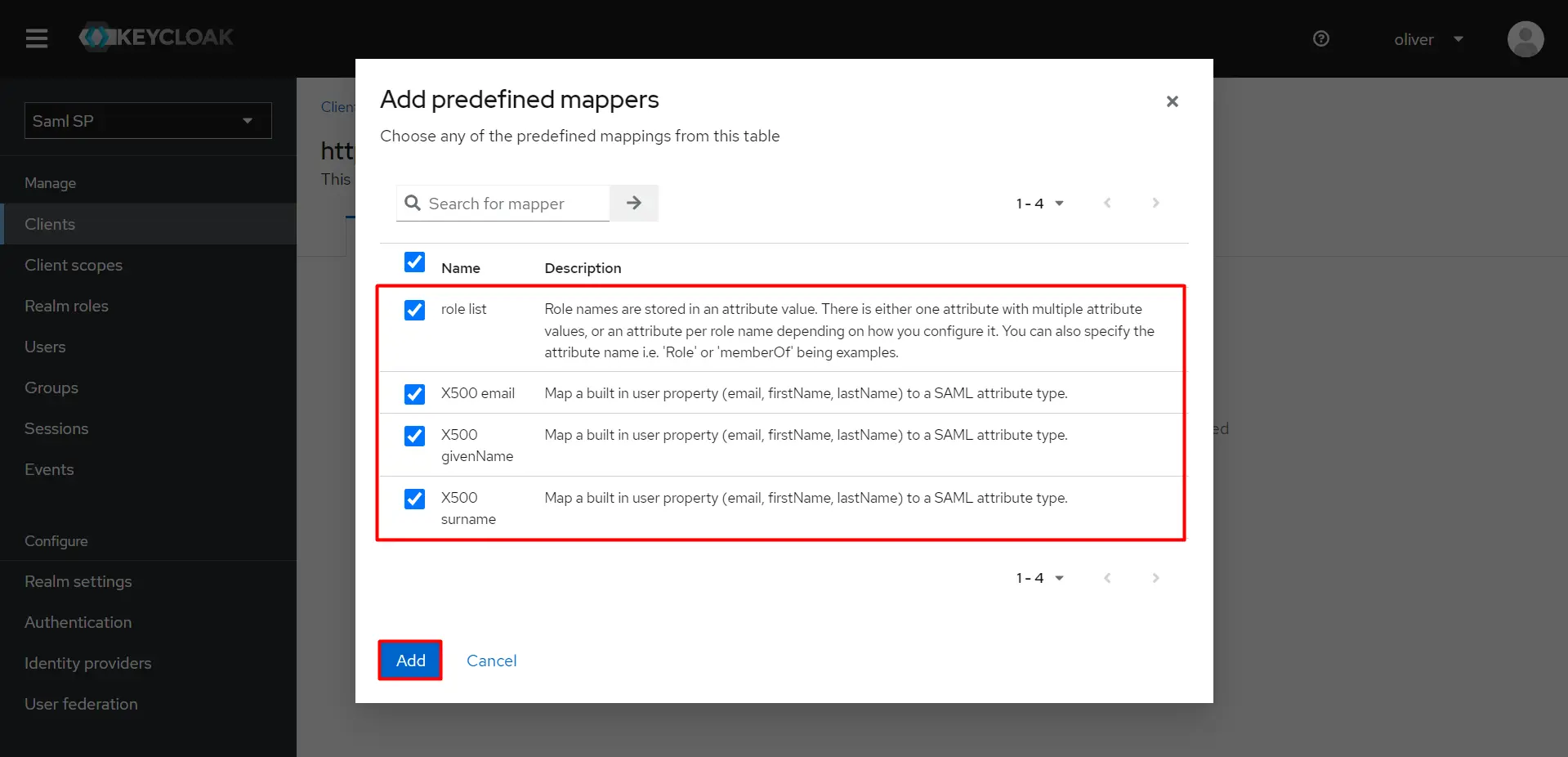
- Click the mappers as shown in click on Add Button.
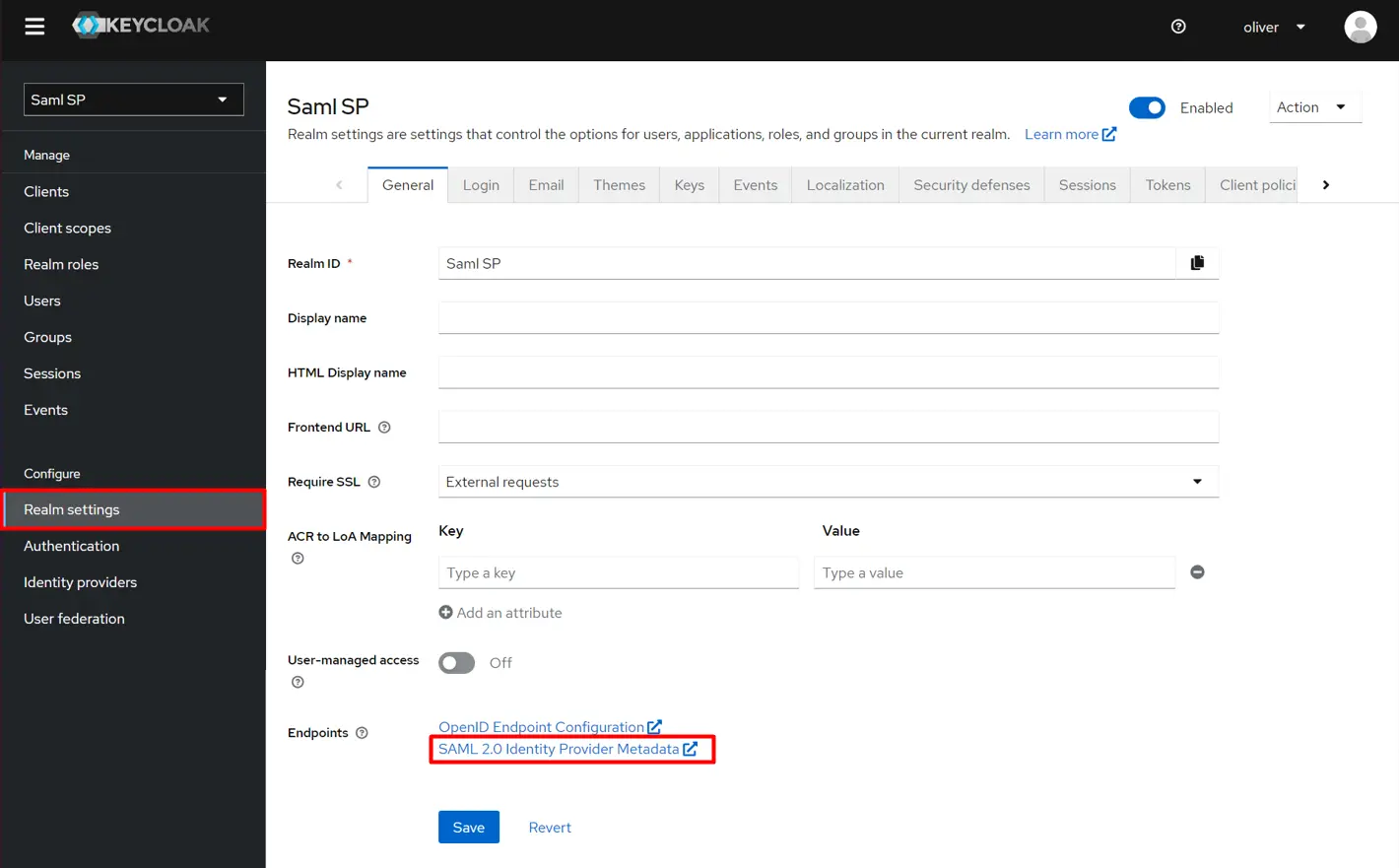
- Click on Realm setting from the left menu and then click on Saml 2.0 Identity Provider Metadata.
- Copy The URL,and Navigate back to miniorange SAML Plugin and go to service Provider setup tab,then click on Upload Metadata file and paste on enter metadata Url and Click on Fetch Metadata.


3. Configure Joomla as Service Provider
In Joomla SAML plugin, go to Service Provider Setup tab. There are three ways to configure the plugin:
 By Uploading Metadata File:
By Uploading Metadata File:
- In Joomla SAML plugin, go to Service Provider Setup tab, then click on Upload IDP metadata.
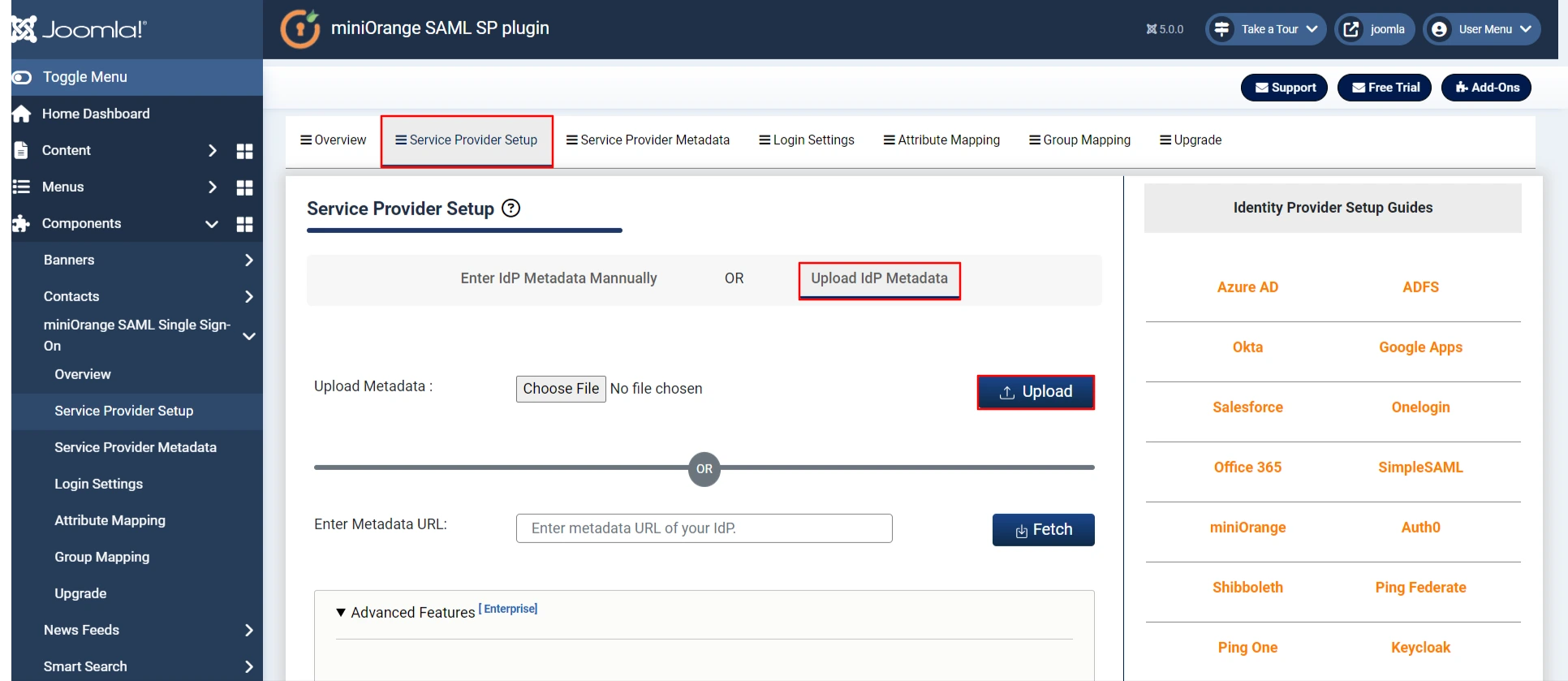
 By Metadata URL:
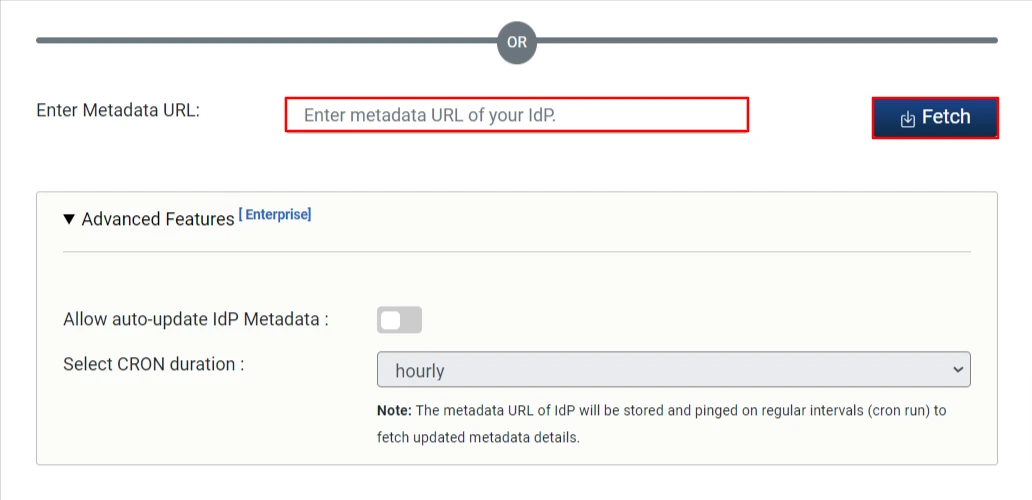
By Metadata URL:
- Enter Metadata URL (Copy from IDP app) and click on Fetch Metadata.
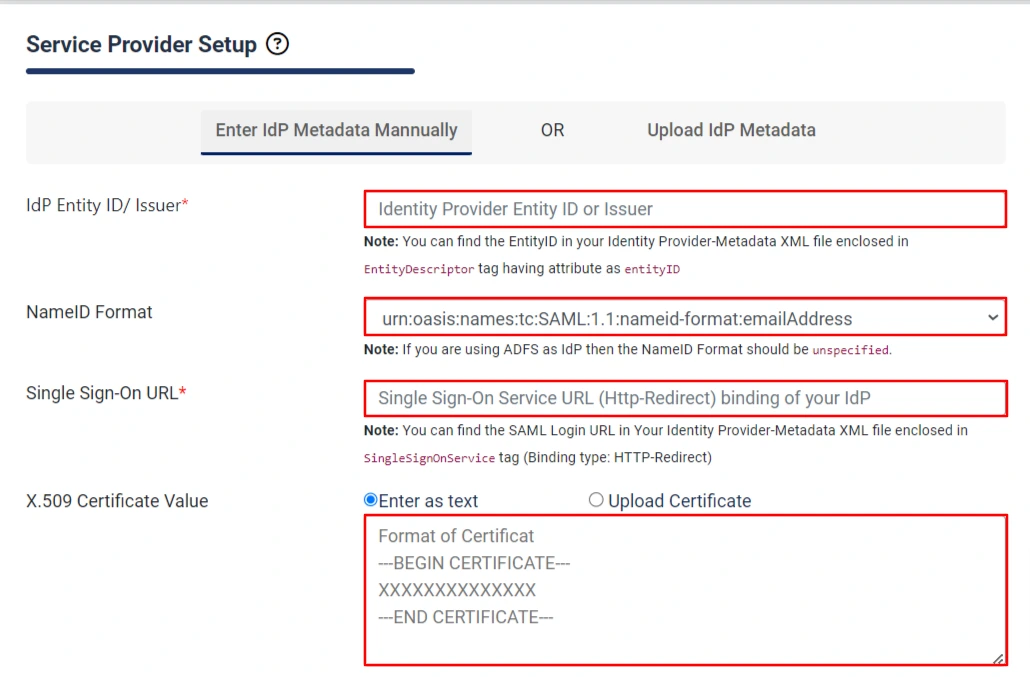
 Manual Configuration:
Manual Configuration:
- Copy SAML Entity ID, SAML Single-Sign-On Endpoint URL and X.509 certificate from
Federation Metadata document and paste it in Idp Entity ID or Issuer, Single Sign-on URL, X.509 Certificate
fields respectively in the plugin.
|
IdP Entity ID or Issuer
SAML Entity ID in the Federation Metadata document
|
|
Single Sign-On URL
SAML Single-Sign-On Endpoint URL in the Federation Metadata document
|
|
X.509 Certificate Value
X.509 Certificate in the Federation Metadata document
|
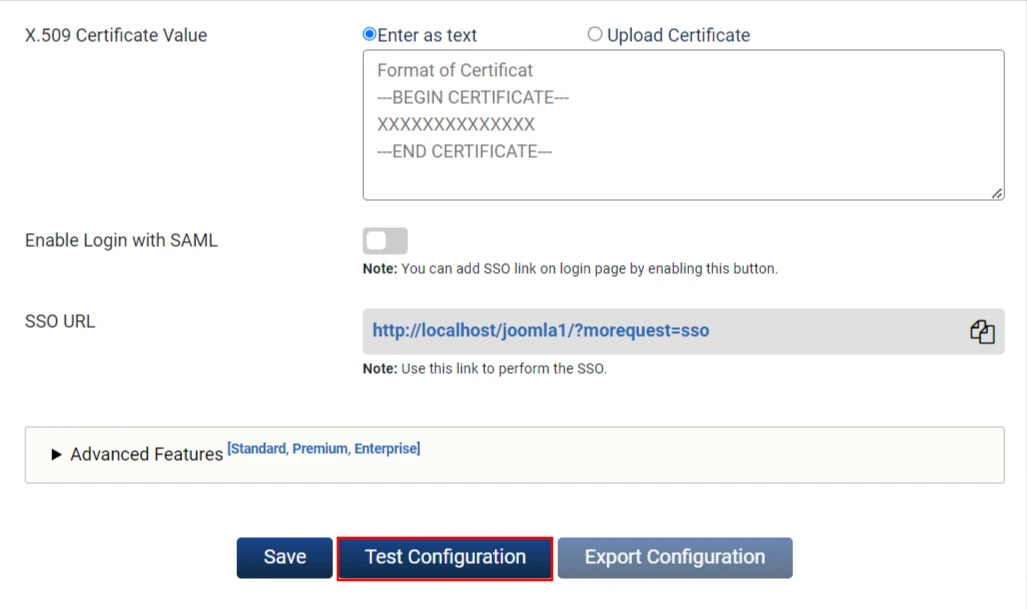
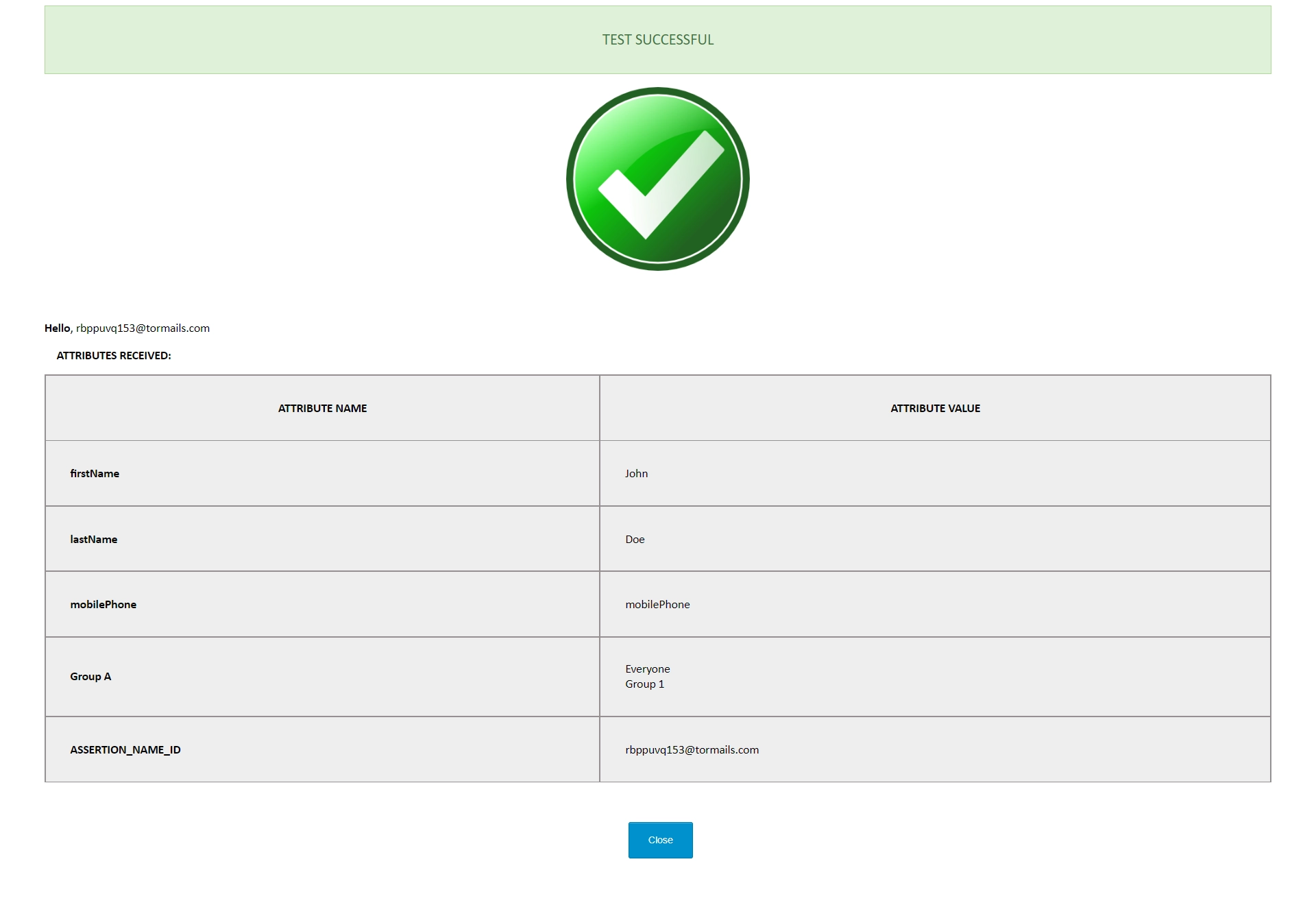
- Click on Save button and then Test Configuration button.
- Once the test configuration is successful you will get the following window.
- Congratulations we have successfully configured Joomla SAML Service Provider.
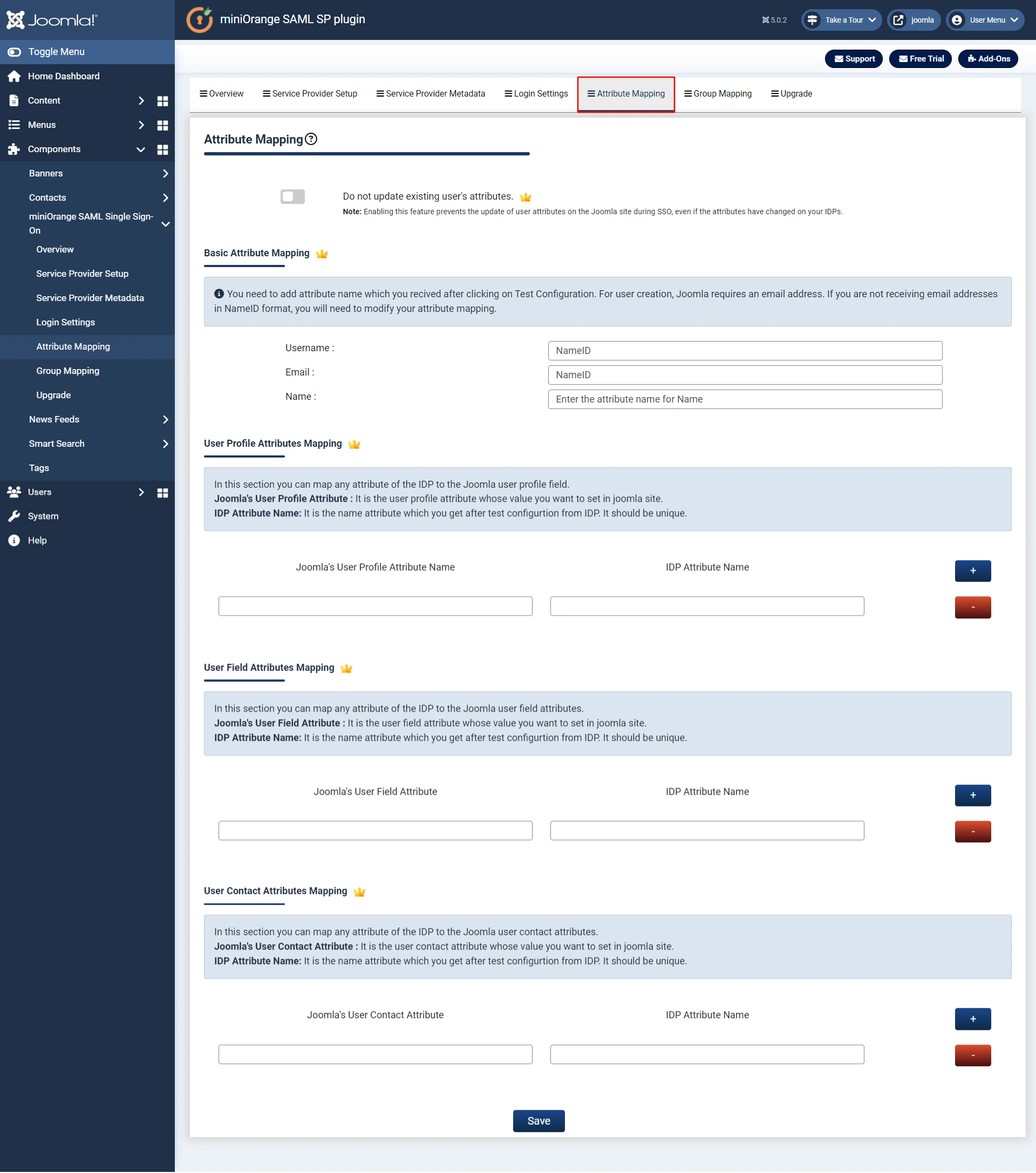
4. Attribute Mapping - This is Premium feature.
- Attributes are user details that are stored in your Identity Provider.
- Attribute Mapping helps you to get user attributes from your Identity Provider (IDP) and map them to Joomla user attributes like firstname, lastname, address, phone etc.
- While auto registering the users in your Joomla site these attributes will automatically get mapped to your Joomla user details.
- Go to Attribute Mapping tab and fill in all the fields.
- You can check the Test Configuration Results under Service Provider Setup tab to get a better idea of which values to map here.
|
Username:
Name of the username attribute from IdP (Keep NameID by default)
|
|
Email:
Name of the email attribute from IdP (Keep NameID by default)
|
|
Name:
Name of the name attribute from IdP
|
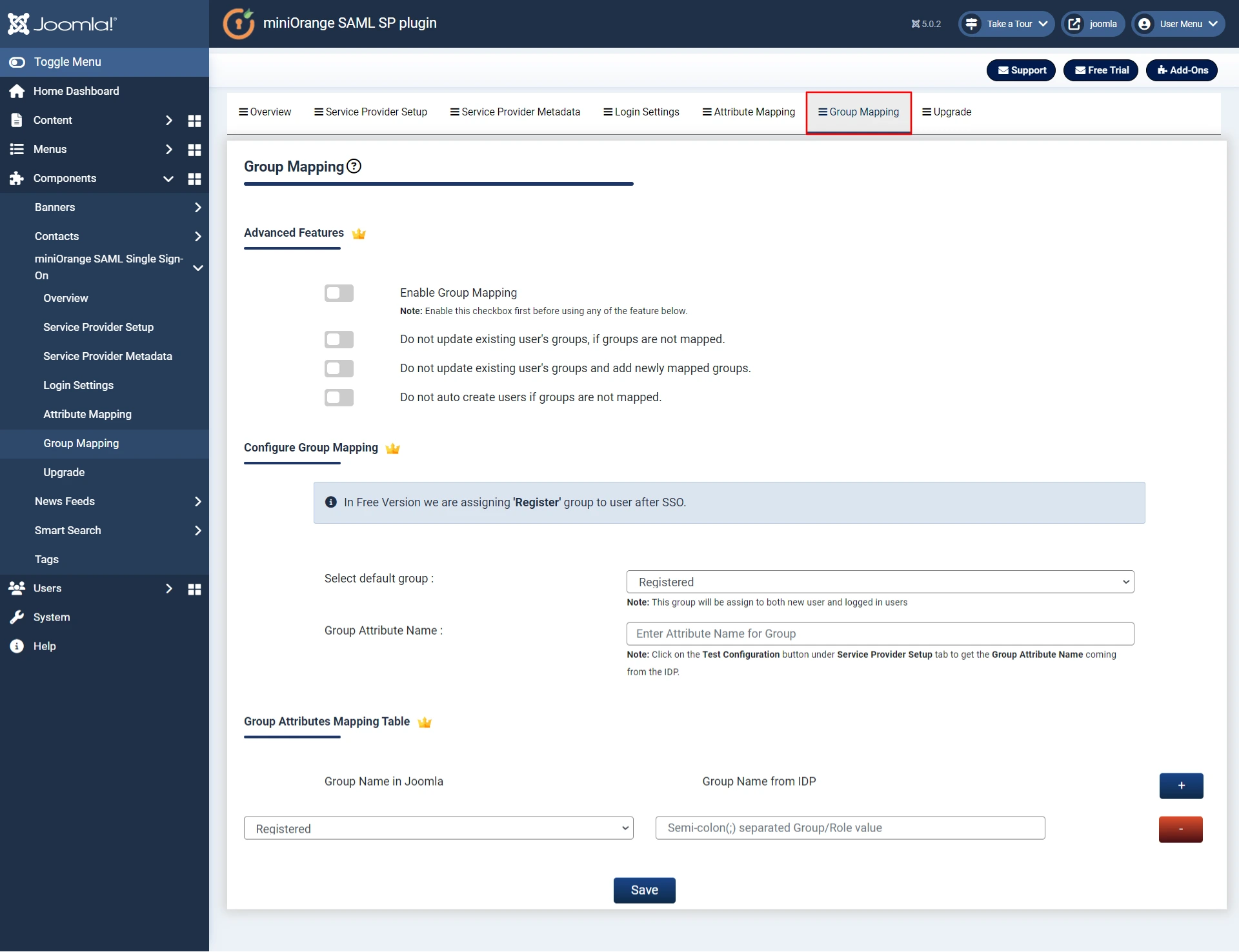
Step 5. Group Mapping - This is Premium feature.
- Group/Role mapping helps you to assign specific roles to users of a certain group in your Identity Provider (IdP).
- While auto registering, the users are assigned roles based on the group they are mapped to.
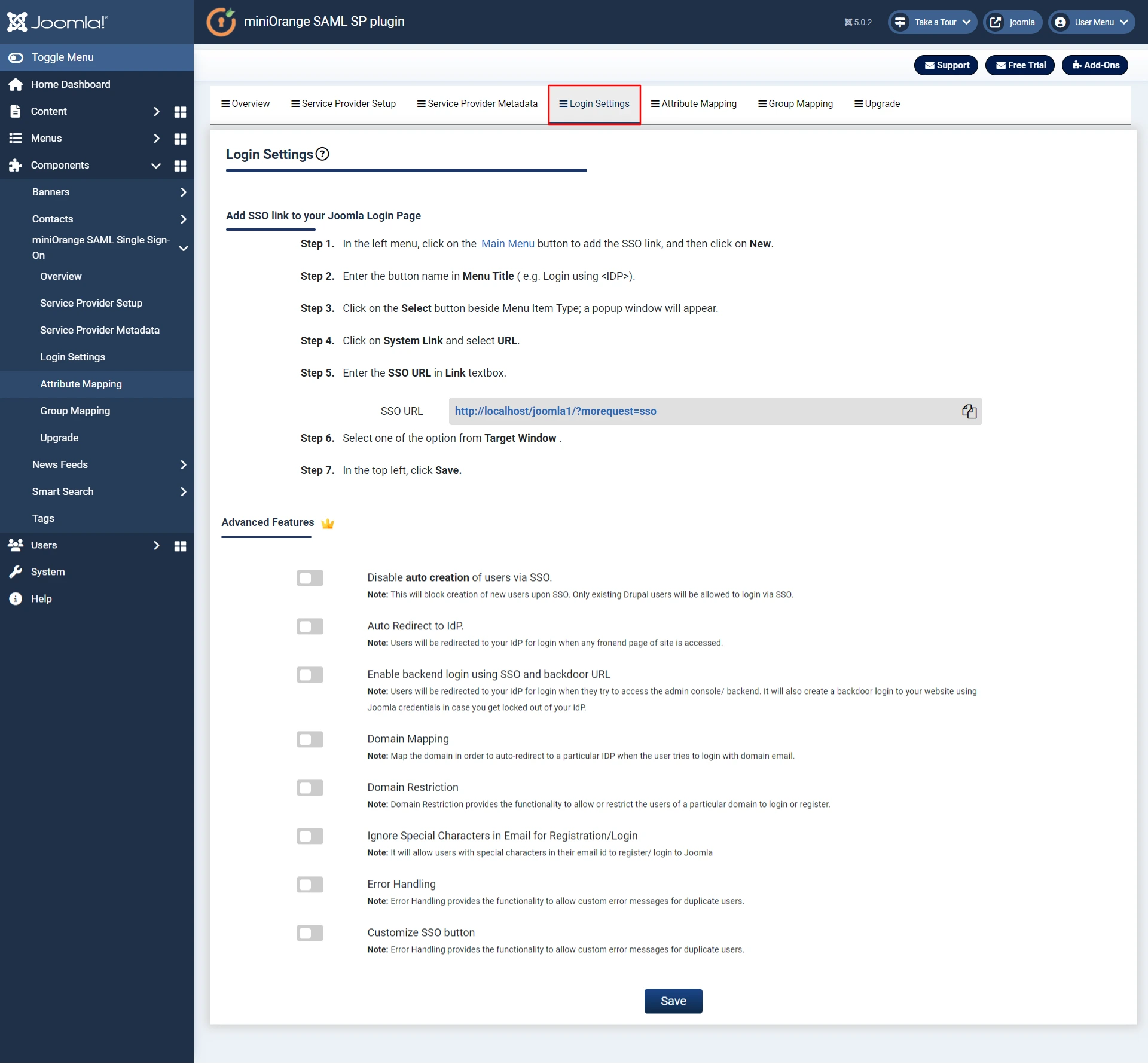
Step 6. Redirection & SSO Links.
- Go to Login Settings tab. You can add login Url to Perform SAML SSO in your Joomla site by following the steps below.
- There are multiple features availabe in this tab like Auto redirect the user to Identity Provider and Enable Backend Login for Super Users. To use these features, click on the respective checkboxes.
- Click on the Upgrade Plans tab to check out our complete list of features and various licensing plans. OR you can click here to check features and licensing plans.
- If you want to purchase any of the paid version of the plugin, you have to register/login with us in Account Setup tab. OR you can register/login here.
- In case, you are facing some issue or have any question in mind, you can reach out to us by sending us your query through the Support button in the plugin or by sending us a mail at joomlasupport@xecurify.com.


Additional Resources.
- What is Single Sign-On (SSO)
- Frequently Asked Questions (FAQs)
- How to configure SSO with Azure AD Identity Provider
- How to configure SSO with ADFS
- How to configure SSO with Salesforce
- How to configure SSO with Okta
- How to configure SSO with Google Apps
Business Trial
If you want Business Trial for FREE click Here
If you don't find what you are looking for, please contact us at joomlasupport@xecurify.com or call us at +1 978 658 9387.
Need Help? We are right here!

Thanks for your inquiry.
If you dont hear from us within 24 hours, please feel free to send a follow up email to info@xecurify.com
Cookie Preferences
Cookie Consent
This privacy statement applies to miniorange websites describing how we handle the personal information. When you visit any website, it may store or retrieve the information on your browser, mostly in the form of the cookies. This information might be about you, your preferences or your device and is mostly used to make the site work as you expect it to. The information does not directly identify you, but it can give you a more personalized web experience. Click on the category headings to check how we handle the cookies. For the privacy statement of our solutions you can refer to the privacy policy.
Strictly Necessary Cookies
Always Active
Necessary cookies help make a website fully usable by enabling the basic functions like site navigation, logging in, filling forms, etc. The cookies used for the functionality do not store any personal identifiable information. However, some parts of the website will not work properly without the cookies.
Performance Cookies
Always Active
These cookies only collect aggregated information about the traffic of the website including - visitors, sources, page clicks and views, etc. This allows us to know more about our most and least popular pages along with users' interaction on the actionable elements and hence letting us improve the performance of our website as well as our services.
