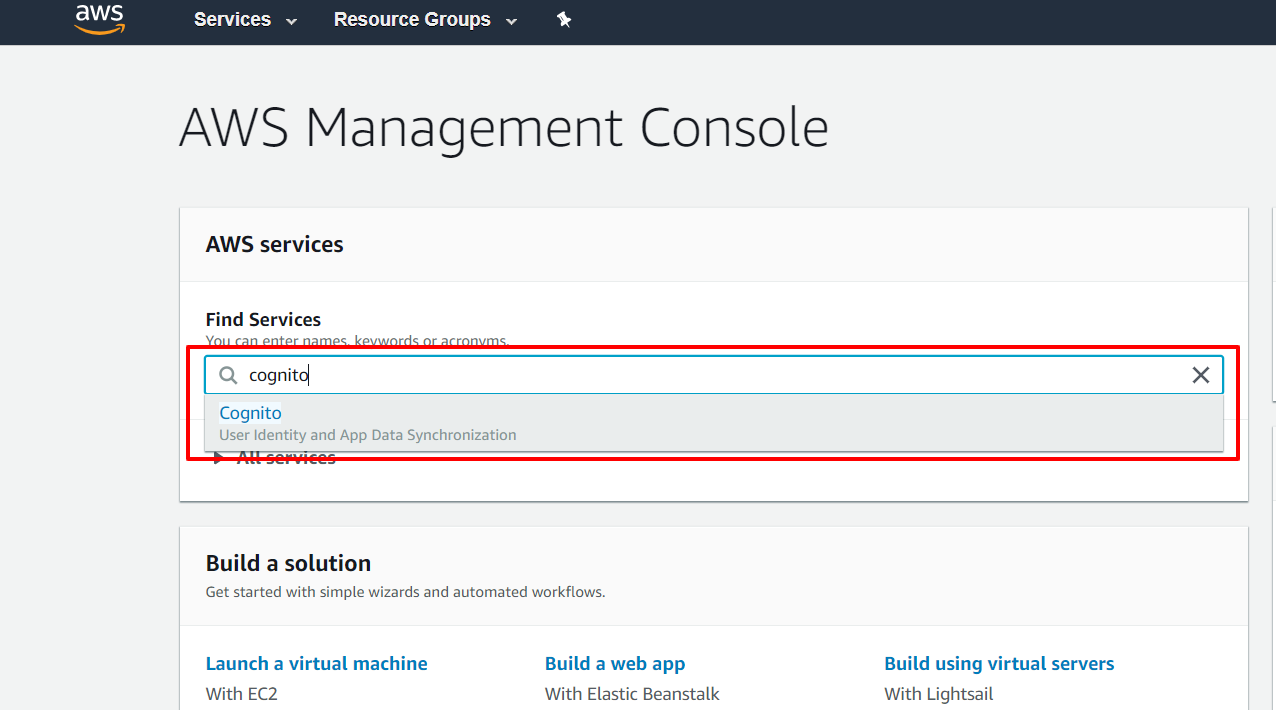
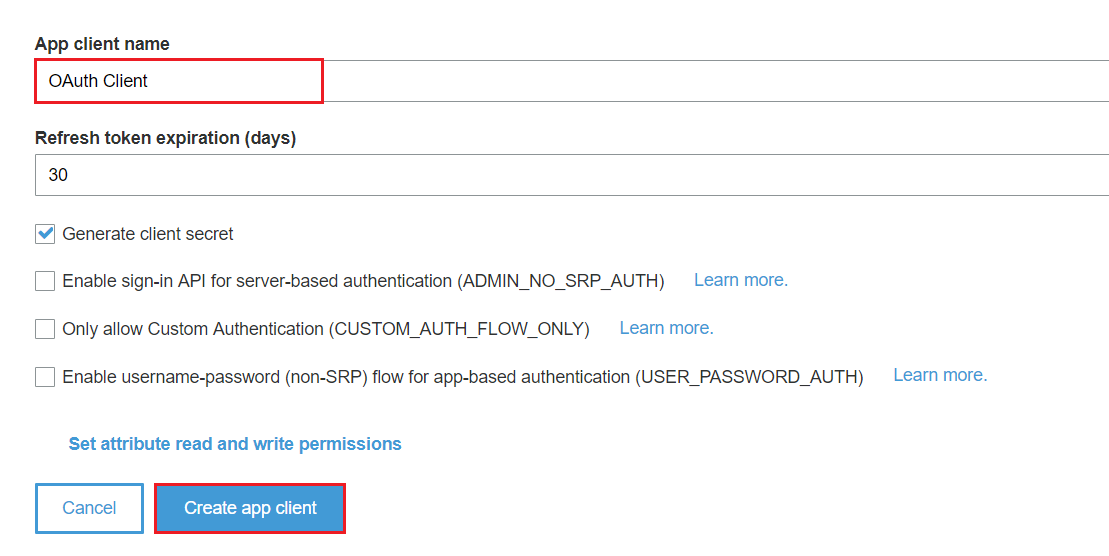
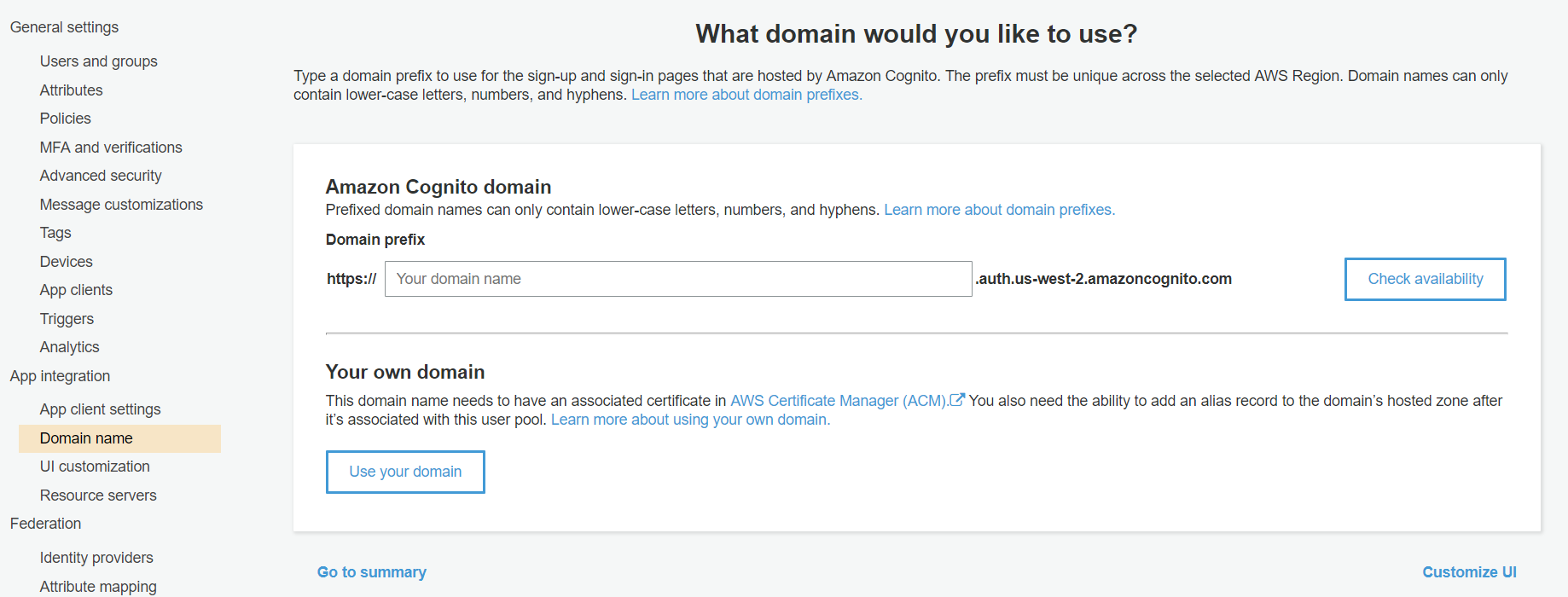
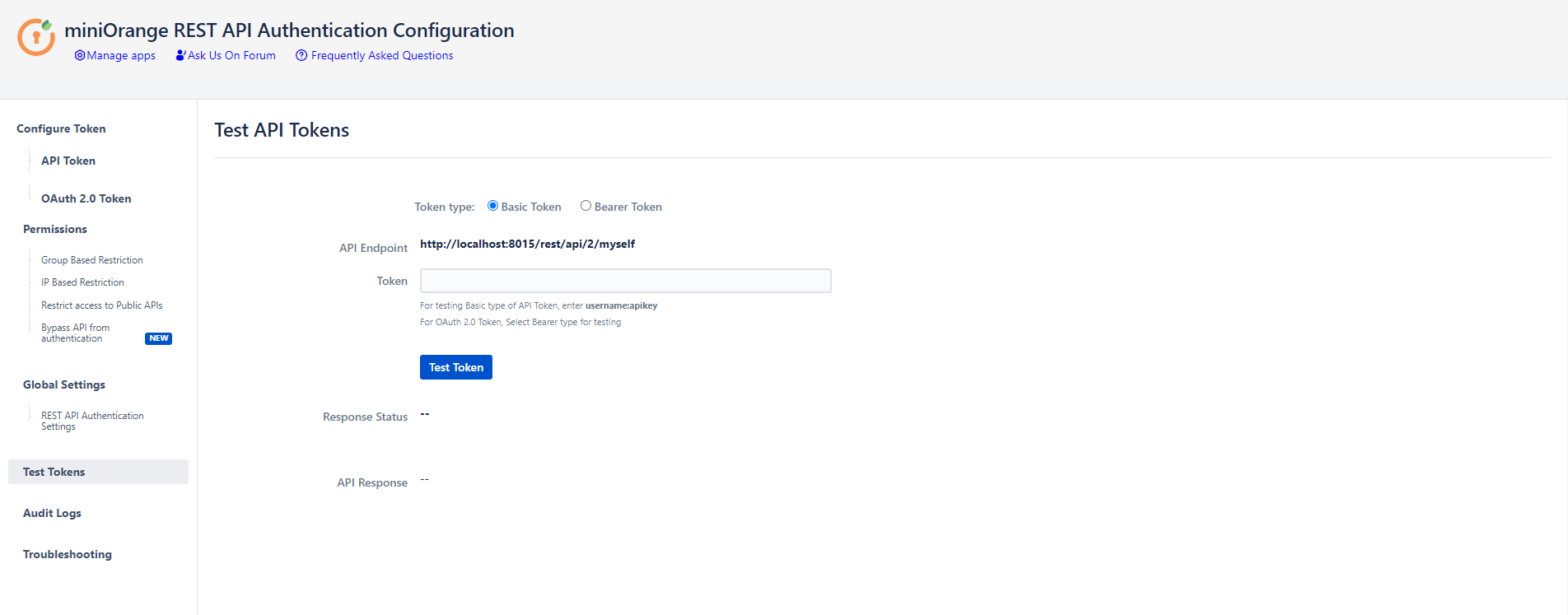
- Open the Postman Application (Here is the link to download Postman Application).
- Go to Authorization tab.
- From the dropdown select type as OAuth 2.0 and click on Get access
token.
- Add the following information from the table below.
- Postman starts the authentication flow and prompts you to use the access token.
- Select Add token to the header.
| Field |
Value |
| Grant type |
Authorization Code or Client Credentials |
| Callback URL |
Enter your application's base URL if you dont have a callback URL |
| Auth URL |
https://{DomainName}/oauth2/authorize |
| Access token URL |
https://{DomainName}/oauth2/token |
| Client ID |
Enter the AWS Cognito Client ID |
| Client secret |
Enter the AWS Cognito Client secret |
| Scope |
Identify |
| Client Authentication |
Send as Basic Auth Header |
- Copy the Access Token or click on Use Token.
A sample access token from
AWS Cognito Provider looks like this.
e8ec210628306b1df26ff61e6b9b3195814a2d79d38a2c7c1dc5836f6ddd7143
Step 3: Fetch Username through AWS Cognito:
- Choose the method type as "GET".
- Enter the interoception Endpoint from the plugin to fetch the username in the Request URL. For AWS Cognito it is "https://##domainName##/oauth2/userInfo".
- Go to the Authorization tab select the Bearer Token and enter the access token here.
- Add the header "content-type: application/json" and click on
Send.
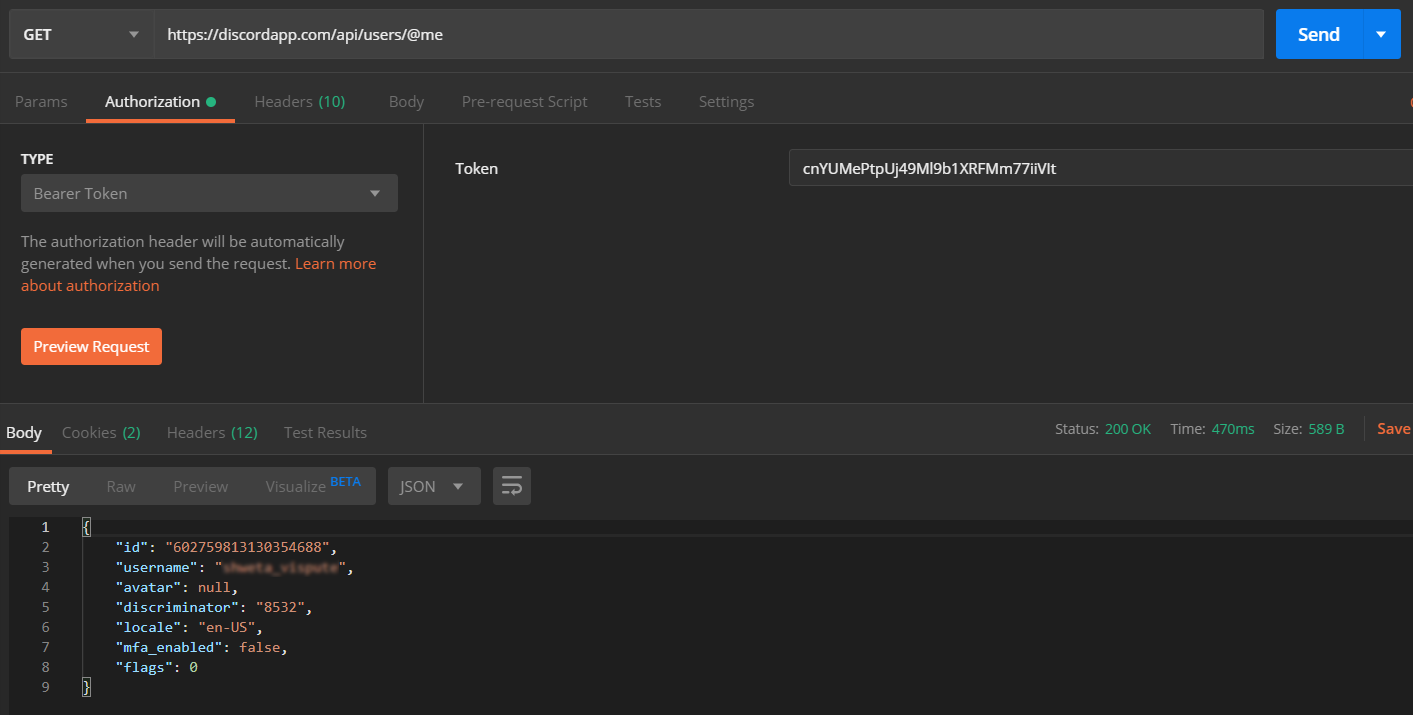 Request:
Request:
curl
-X GET
-H "Authorization: Bearer <Access Token>"
-H "Content-type: application/json"
https://discordapp.com/api/users/@me
Copy the attribute value against the username, you will need to configure it in plugin. In this
example, the value is "username".
Step 4: Configure the Rest API plugin:
1: Enable Rest API Authentication:
- After installing the app, click on Configure to configure plugin.
- Select the Authentication type and navigate to Oauth/OIDC tab, then click on
Configure.
- From the drop down select AWS Cognito as OAuth Provider.
- Enter the Domain Name from AWS Cognito.
- Enter the attribute value against which we received the username in the Postman response.
- Save the settings.
- Now navigate to the Global Settings tab.
- Here you will have to Enable the Authentication through Enable REST API
Authentication and click on Save.
- To configure the username attribute, click on Get username/email Attribute button.
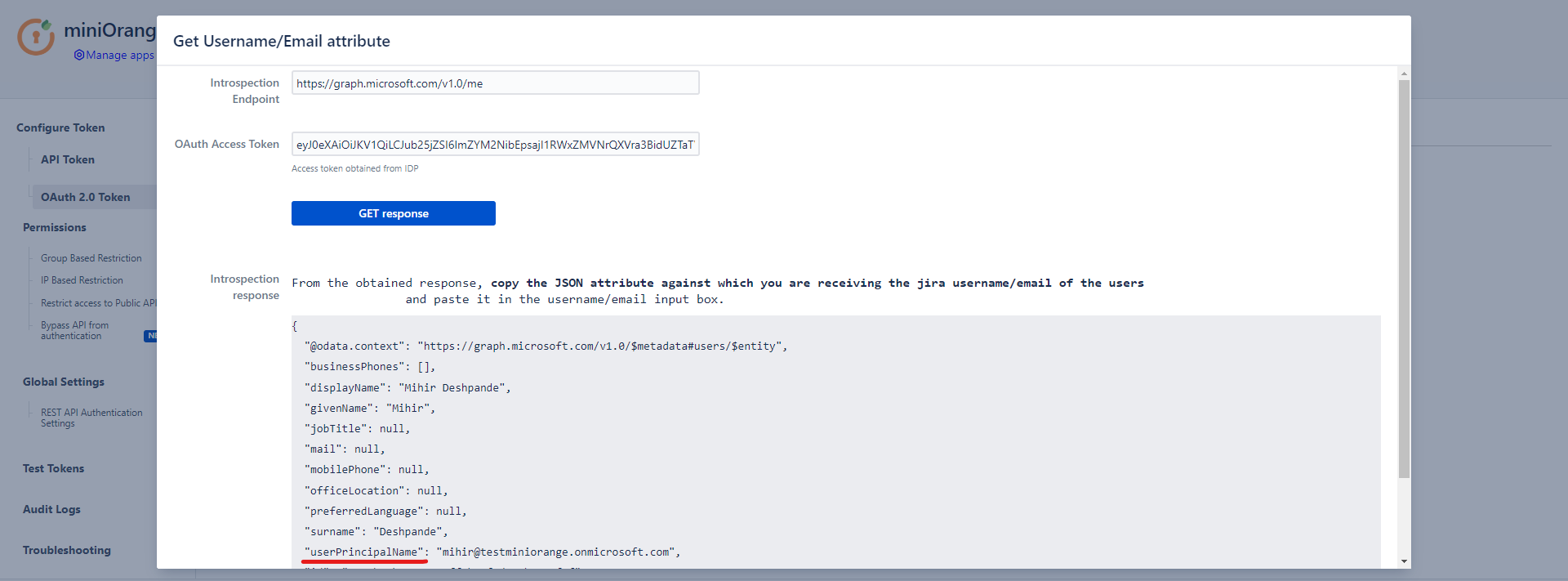
- Paste the OAuth 2.0 Access token obtained from the OAuth provider and click on Get response.
- In the received response, copy the JSON attribute against which you are receiving the username/email of the user in the local directory and paste it into the Username/Email Attribute input field, and click on Save.
Step 5: Test REST API using access token:
API keys and Tokens can be tested with the Test tokens feature. Select the type - Basic/Bearer, paste the token and click on Test token button.
Click here to get a FREE TRIAL of Bitbucket REST API Plugin
- Call Confluence REST API endpoint. Include the access token in the Authorization header. Here’s an example of fetching content from Confluence.
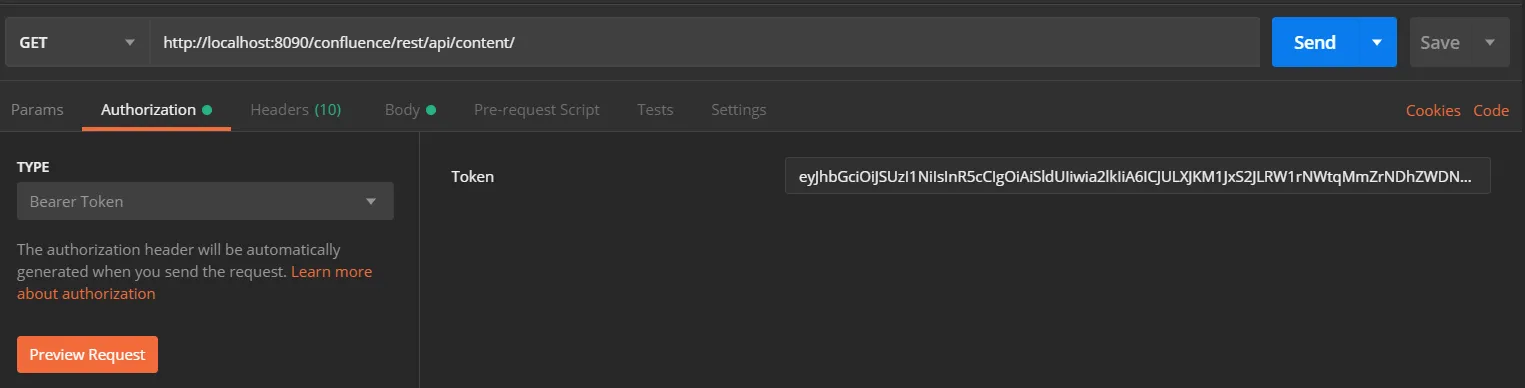
- Go to the Postman application select method type as GET and enter the Request URL. For eg. http://{Confluence_Base_URL}/confluence/rest/api/content/
- In the Authorization tab select type as Bearer Token.
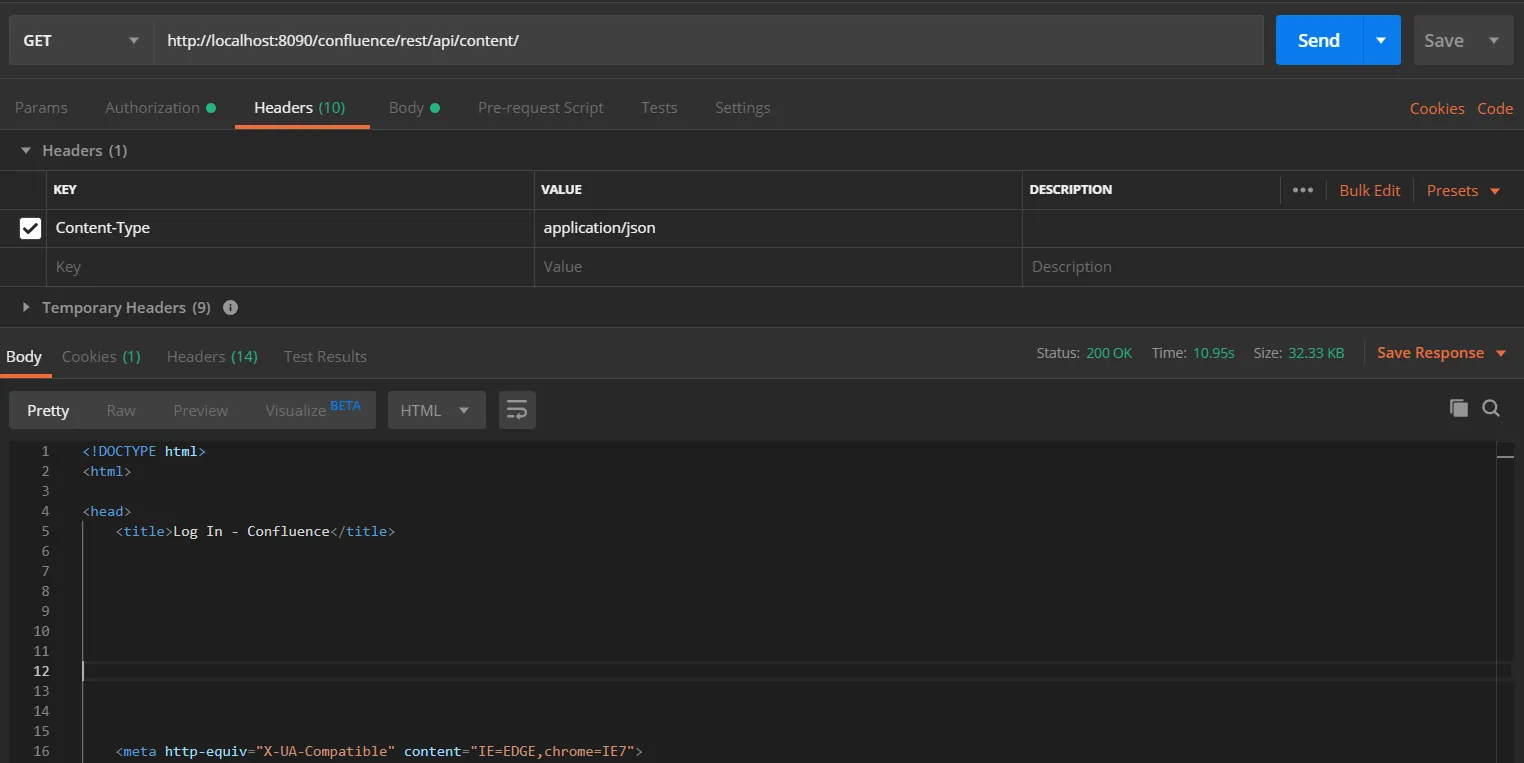
- In the Header tab add the header “content-type: application/json and send the request.
 Request:
Request:
curl
-X GET
-H "Authorization: Bearer <Access Token>"
-H "Content-type: application/json"
http://{confluence_base_url}/confluence/rest/api/content/
- This will show the content in Confluence and will return the status 200.
- If the token is invalid or missing, the call will return a 401 Unauthorized response
Click here to get a FREE TRIAL of Bitbucket REST API Plugin
- Call Bitbucket REST API endpoint. Include the access token in the Authorization header. Here’s an example of fetching content from Bitbucket.
- Go to the Postman application select method type as GET and enter the Request URL. For eg. http://{Bitbucket_Base_URL}/rest/api/1.0/dashboard/pull-requests
- In the Authorization tab select type as Bearer Token.
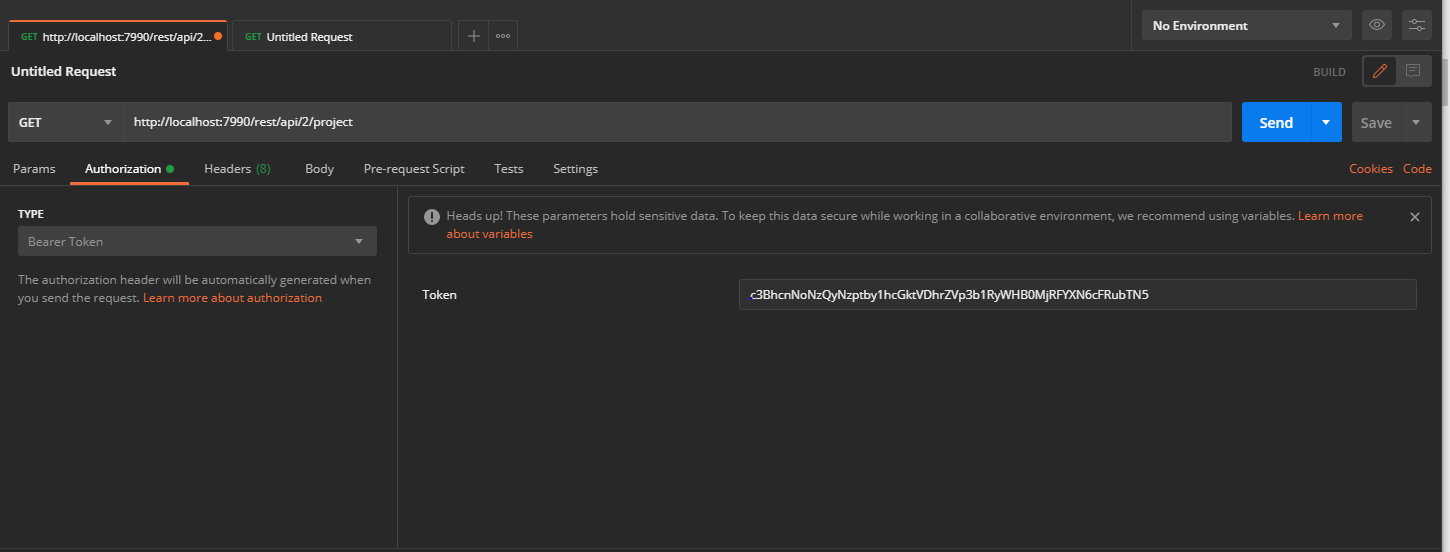
- In the Header tab add the header “content-type: application/json and send the request.
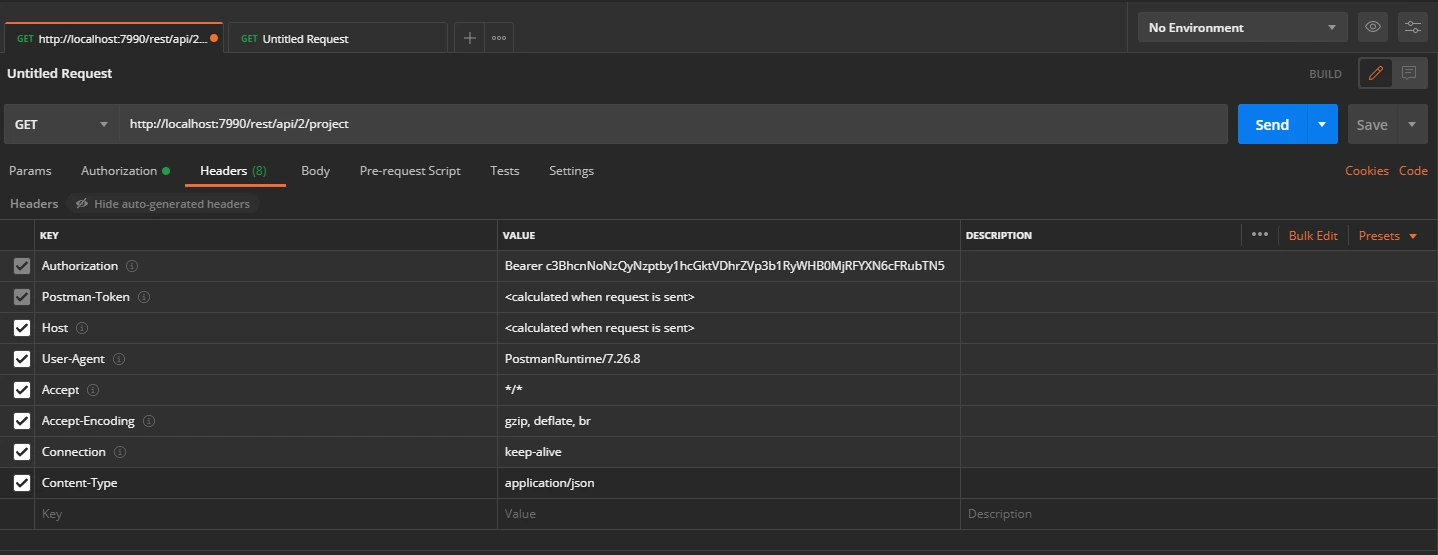 Request:
Request:
curl
-X GET
-H "Authorization: Bearer <Access Token>"
-H "Content-type: application/json"
http://{bitbucket_base_url}/rest/api/1.0/dashboard/pull-requests/
- This will Retrieve a page of pull requests where the current authenticated user status 200.
- If the token is invalid or missing, the call will return a 401 Unauthorized response