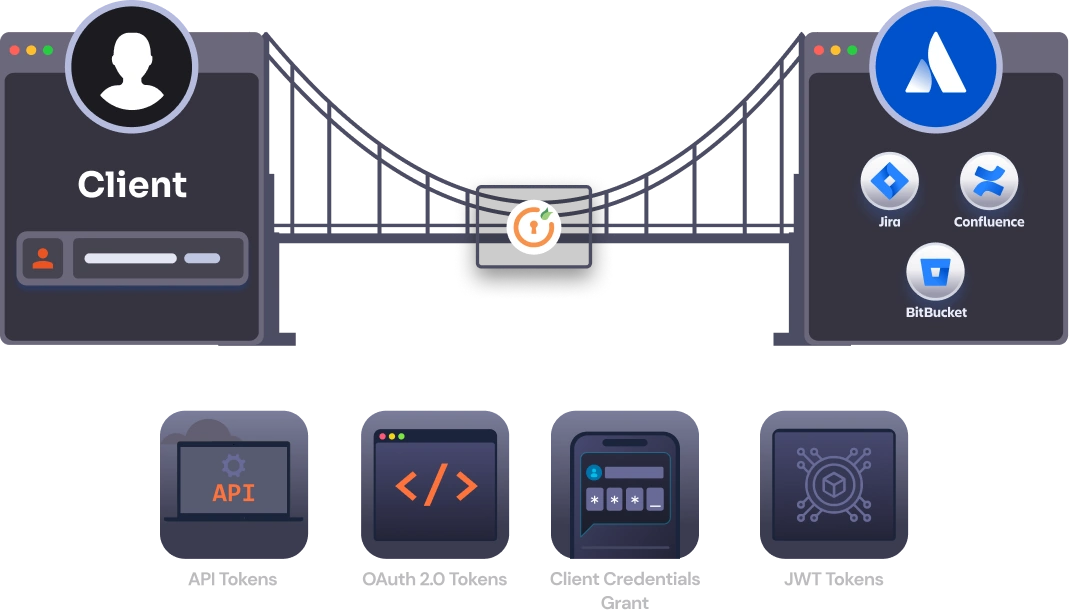
Why Choose miniOrange Over Atlassian Personal Access Tokens(PAT)?
Features
Enhanced OAuth integration with robust PKCE support
Restrict users from generating tokens
IP-based restrictions for limiting access outside your network
Enhance control with group-based restrictions
Prevent overload with token based rate limiting
Prevent unauthorized modification by enabling read-only access
Try Out Our Rest API Authentication Solutions From

Client Success Stories
Finance

IT Services
Benefits That Make Life Easier for You!
Precise Access Control
Restrict API-based access within the Atlassian ecosystem, allowing granular control over resource accessibility and safeguarding sensitive data from unauthorized access or breaches.
Effortless Integration
Confidently integrate external services into your Atlassian ecosystem, fostering efficient collaboration while upholding rigorous security standards.
Centralized Authentication
Streamline authentication processes for REST API calls, centralizing management and ensuring uniformity across your Atlassian ecosystem with third-party applications.
Discover Our App Features

Access Control Restrictions
Restrict API access based on local groups or IP addresses, enabling granular control over resource accessibility and enhancing security measures.

Token-Based Authentication
Integrate services and scripts within an SSO-enabled environment using token-based authentication, ensuring robust authentication mechanisms.

Third-Party OAuth/OIDC Authentication
Authenticate API requests seamlessly using a third-party OAuth/OIDC provider for enhanced security and ease of integration.

API Token Management
Create or revoke individual API tokens for users, providing flexibility and control over API access permissions.

Script Integration
Generate API tokens via REST endpoints, facilitating easy integration with scripts and automating authentication processes.
Hear It From Our Satisfied Customers
At our core, we prioritize our customers above all else. Every decision we make is in your best interest. Your feedback guides our efforts to continually elevate our products and services


Support has been fantastic and fast
Purchased the API App and it was very easy to use out of the gate. Support has been fantastic and fast. Keep up the great work.

The product is easy to install, works great
It was good to see the flexibility in the product to allow the choice of a custom IdP.

It works great
We have Buy this Api Plug In and it works great. It´s easy to create an API token. Great Job.
One-Stop-Shop to Your Bundle of Security
Our product suite offers tailored solutions designed specifically for Atlassian environments, ensuring seamless compatibility and integration.