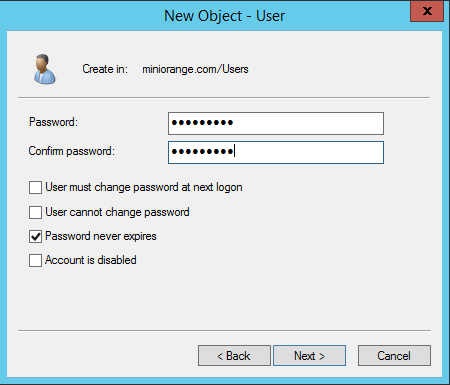
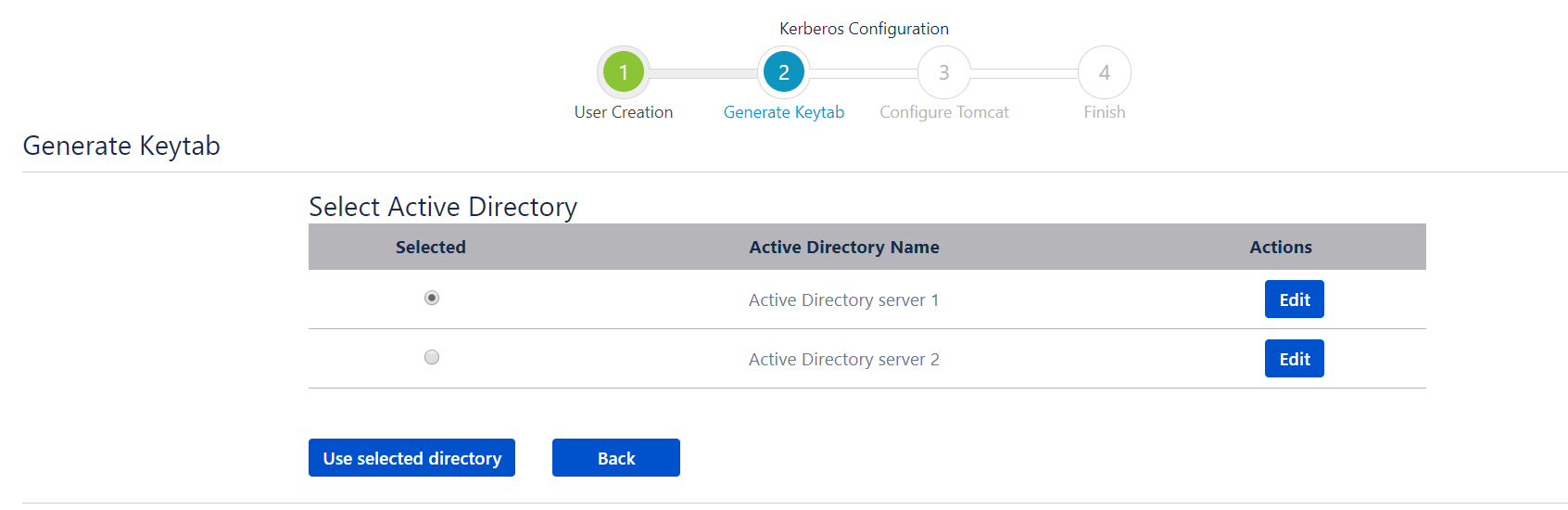
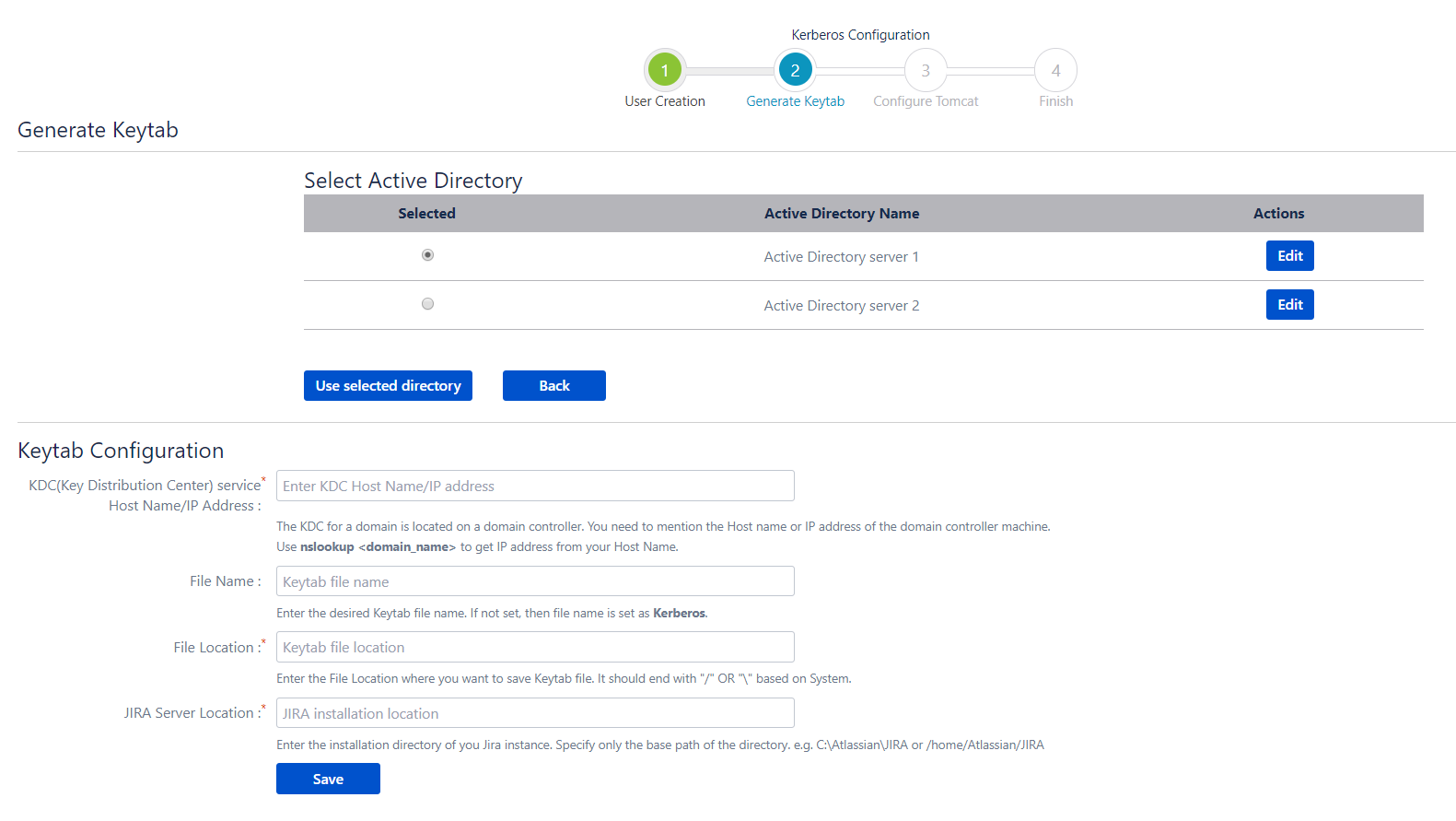
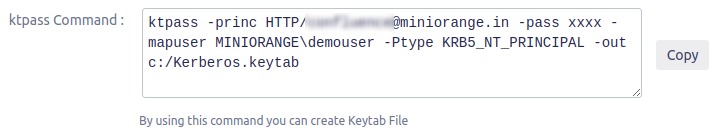
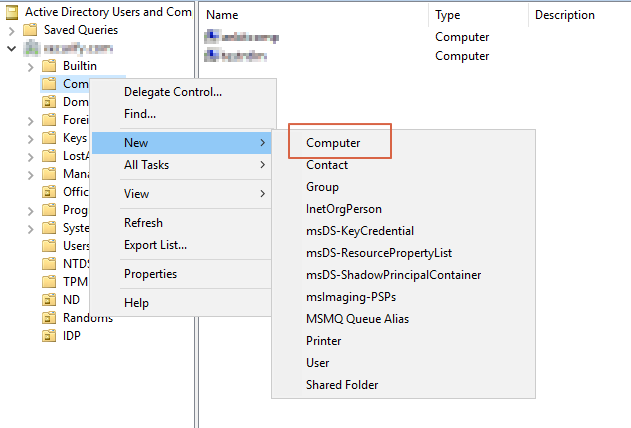
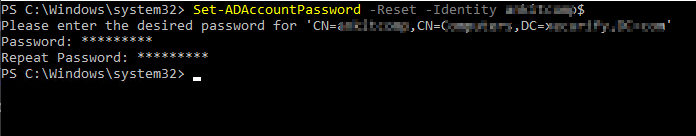
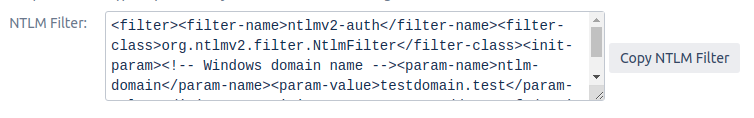
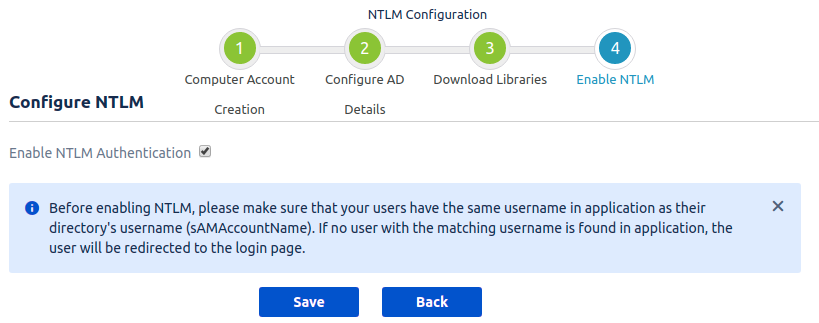
Kerberos Authentication / Integrated Windows Authentication (IWA) gives the end-user access to Jira without entering username or password. Kerberos requires client machines to have access to a Key Distribution Center (KDC), which in the Windows world generally means Active Directory. For security reasons, AD is generally not reachable outside the local network/corporate intranet, making Kerberos mainly applicable within a company.
Download And Installation
- Log into your atlassian instance as admin.
- Navigate to the settings menu and Click Manage Apps.
- Click Find new apps or Find new add-ons from the left-hand side of the page.
- Locate Kerberos/NTLM/Windows SSO for Jira app.
- Click Try free to begin a new trial or Buy now to purchase a license.
- Enter your information and click Generate license when redirected to MyAtlassian.
- Click Apply license.