Contents
SSO Login into Drupal using Microsoft Entra ID as an OAuth / OpenID Connect Provider
Drupal Microsoft Entra ID SSO integration will allow the users to log in to the Drupal site using the Microsoft Entra ID Credentials. This SSO integration is achieved by the miniOrange OAuth Client module which uses the OAuth 2.0 and OpenID Connect (OIDC) Protocol.
In this document, we will help you configure the Single Sign-On login using the OAuth protocol between the Drupal site and the Microsoft Entra ID.
Installation Steps:
- Download the module:
composer require 'drupal/miniorange_oauth_client'
- Navigate to Extend menu on your Drupal admin console and search for miniOrange OAuth Client Configuration using the search box.
- Enable the module by checking the checkbox and click on the Install button.
- You can configure the module at:
{BaseURL}/admin/config/people/miniorange_oauth_client/config_clc
- Install the module:
drush en drupal/miniorange_oauth_client
- Clear the cache:
drush cr
- You can configure the module at:
{BaseURL}/admin/config/people/miniorange_oauth_client/config_clc
- Navigate to Extend menu on your Drupal admin console and click on Install new module.
- Install the Drupal OAuth & OpenID Connect Login - OAuth2 Client SSO Login module either by downloading the zip or from the URL of the package (tar/zip).
- Click on Enable newly added modules.
- Enable this module by checking the checkbox and click on install button.
- You can configure the module at:
{BaseURL}/admin/config/people/miniorange_oauth_client/config_clc
Setup Drupal as OAuth Client:
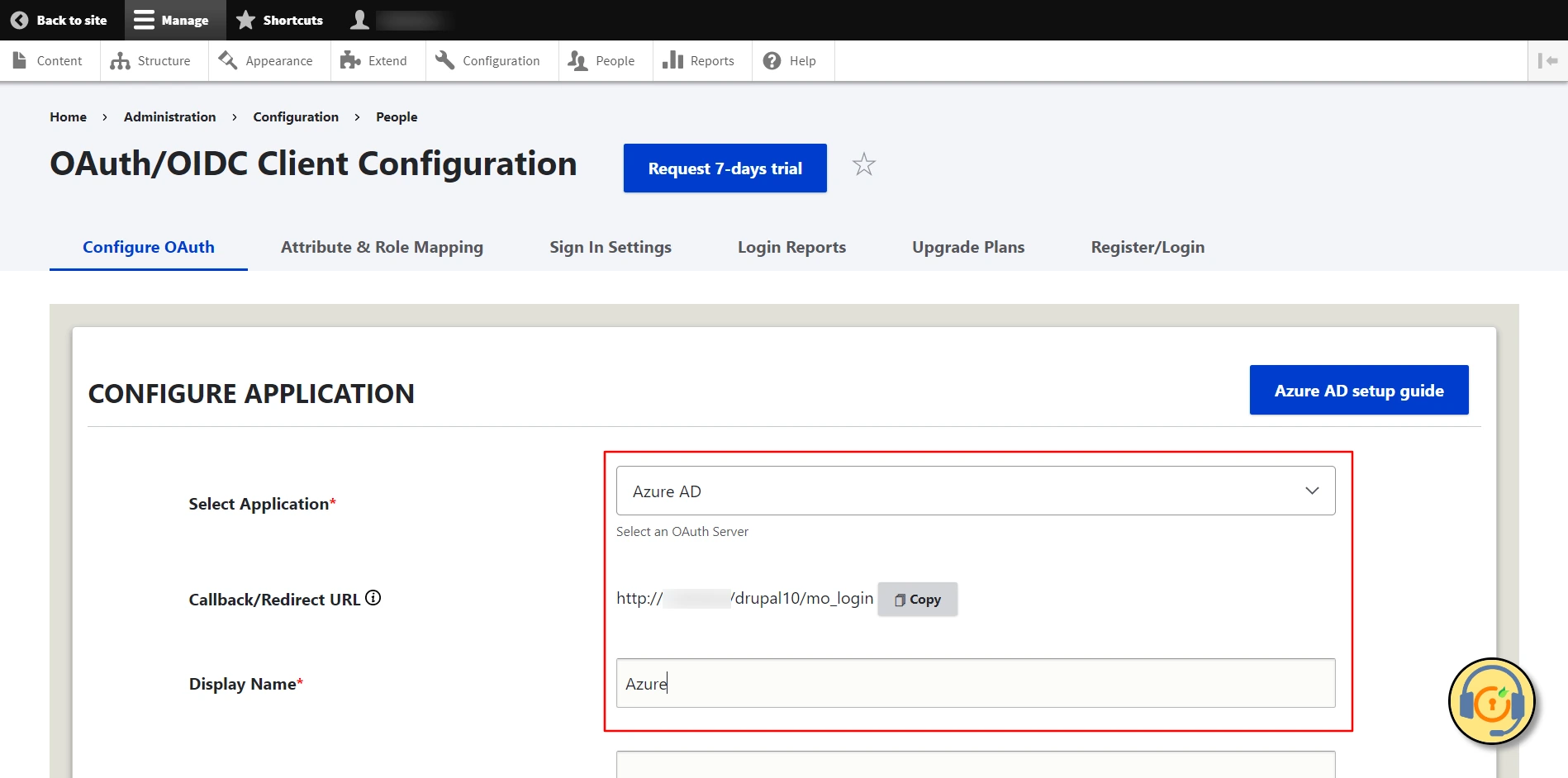
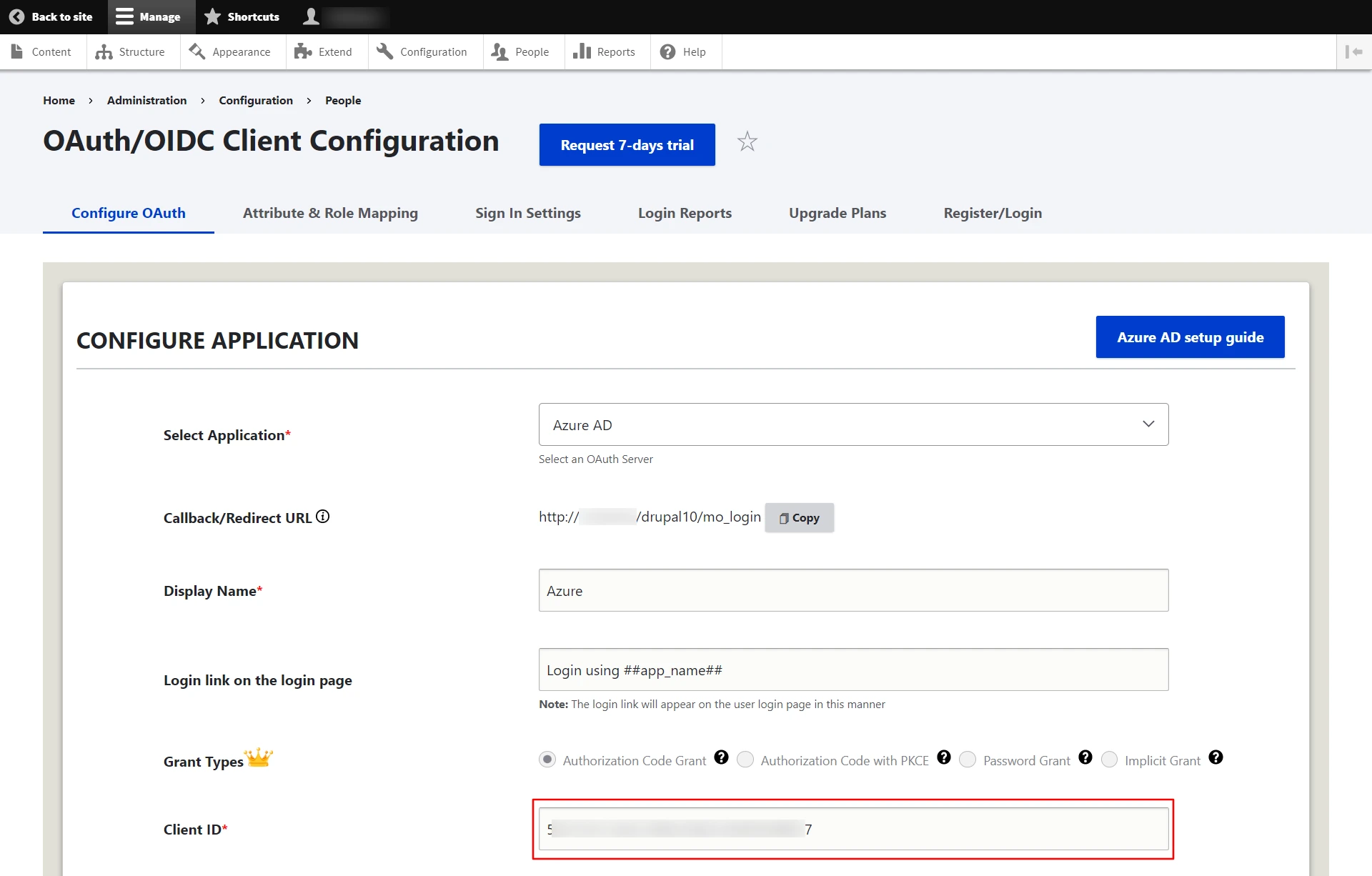
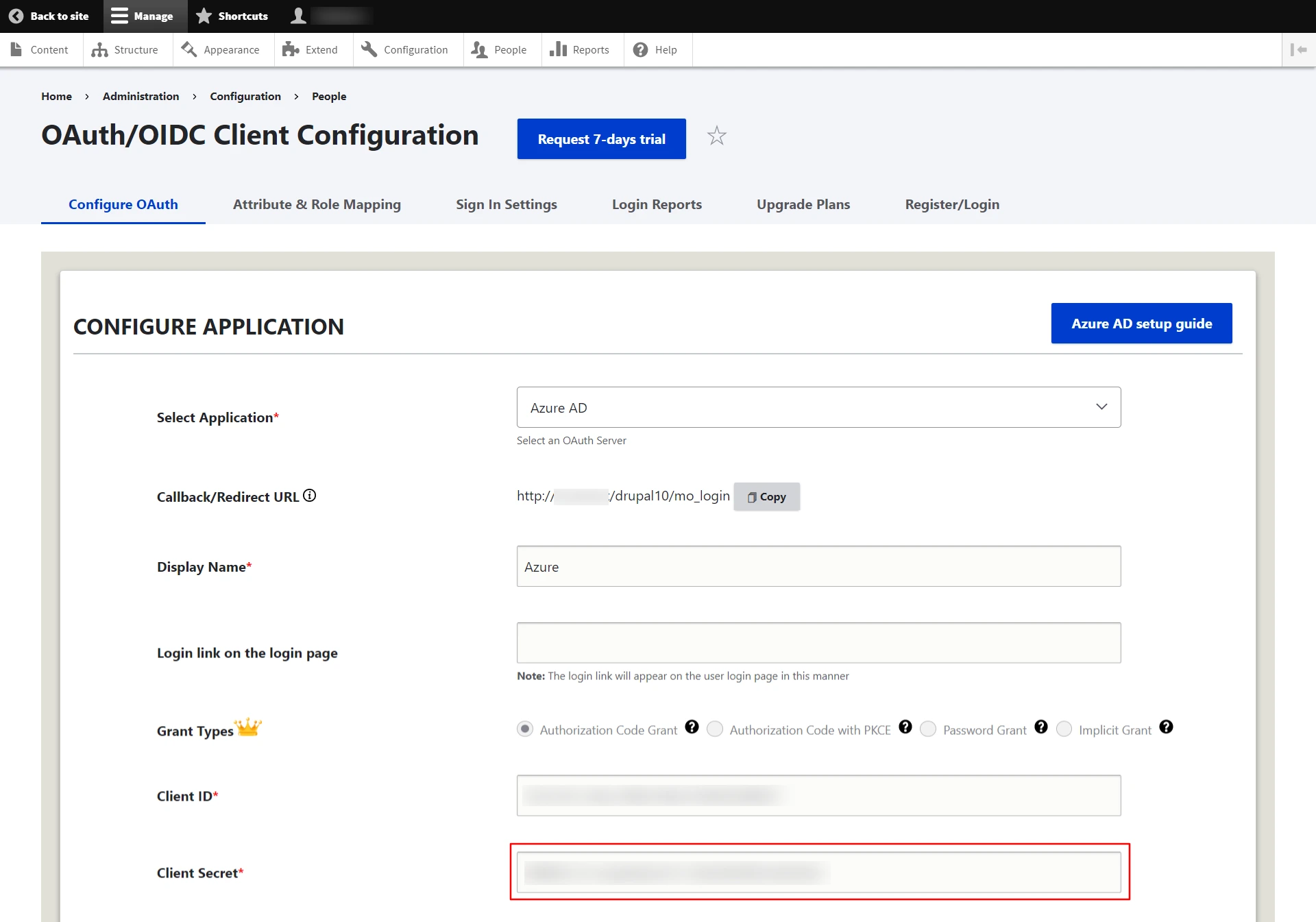
- After installing the module, navigate to the Configuration -> miniOrange OAuth Client Configuration -> Configure OAuth tab and select Microsoft Entra ID - Azure AD from the Select Application dropdown list.
- Copy the Callback/Redirect URL and keep it handy.
Note: If your provider only supports HTTPS Callback/Redirect URLs and you have an HTTP site, please make sure to enable the 'Enforce HTTPS Callback URL' checkbox at the bottom of the tab.
- Enter the application name in the Display Name text field. For example, Azure.
Create SSO Application in Microsoft Entra ID:
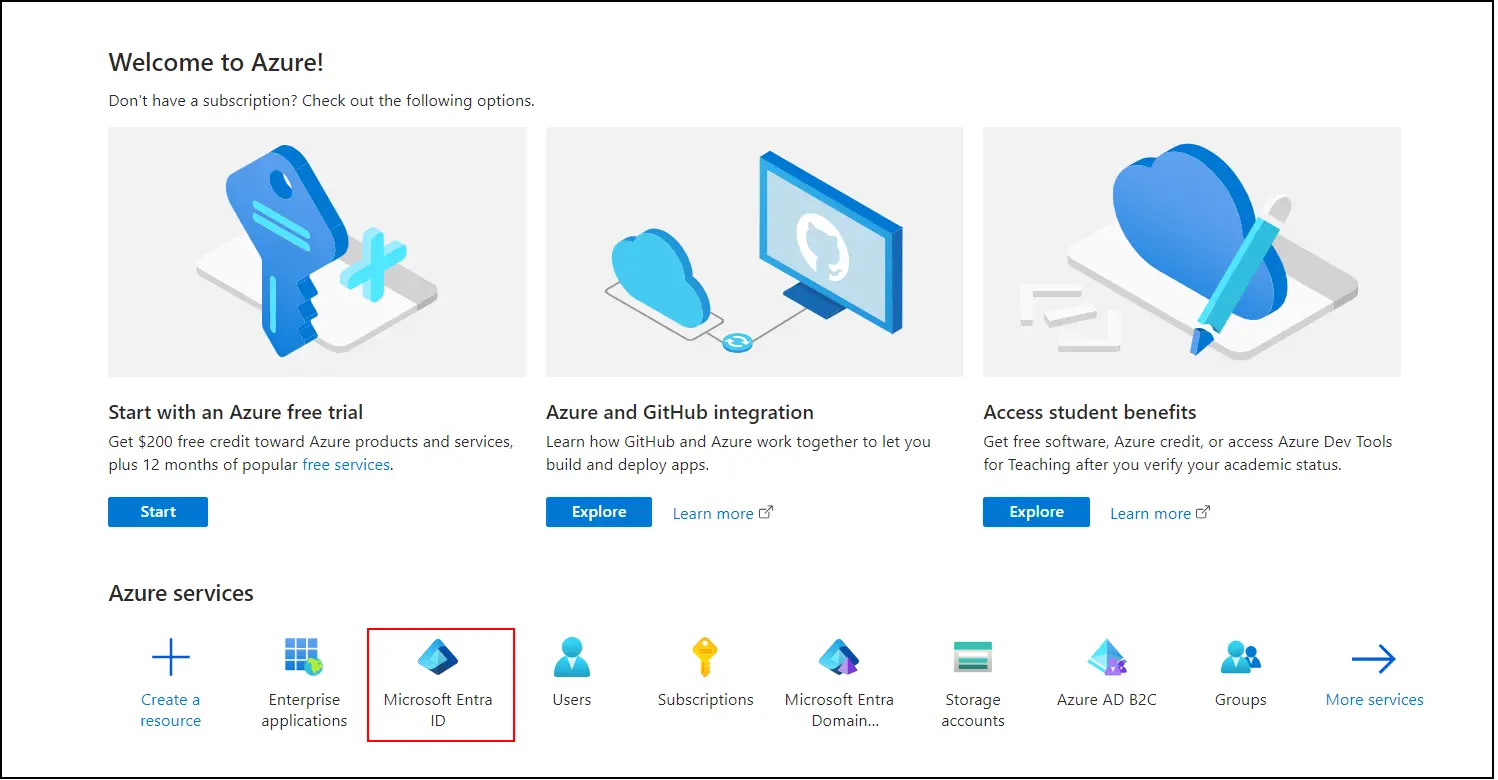
- Log in to the Microsoft Azure portal.
- Select Microsoft Entra ID from the Azure services section.
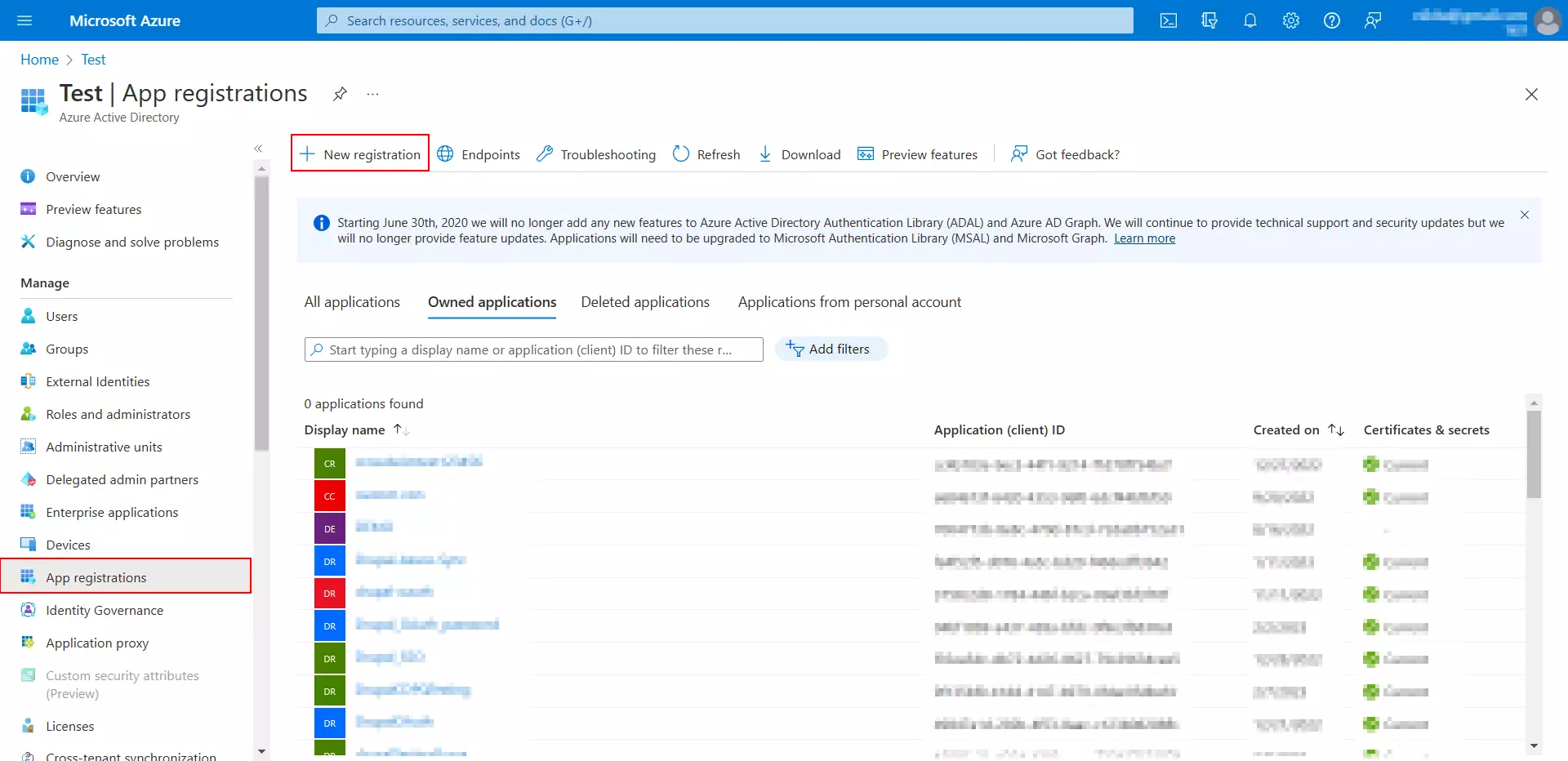
- To create a new Microsoft Entra ID application, navigate to App registrations in the left-hand navigation panel and click on the New registration button.
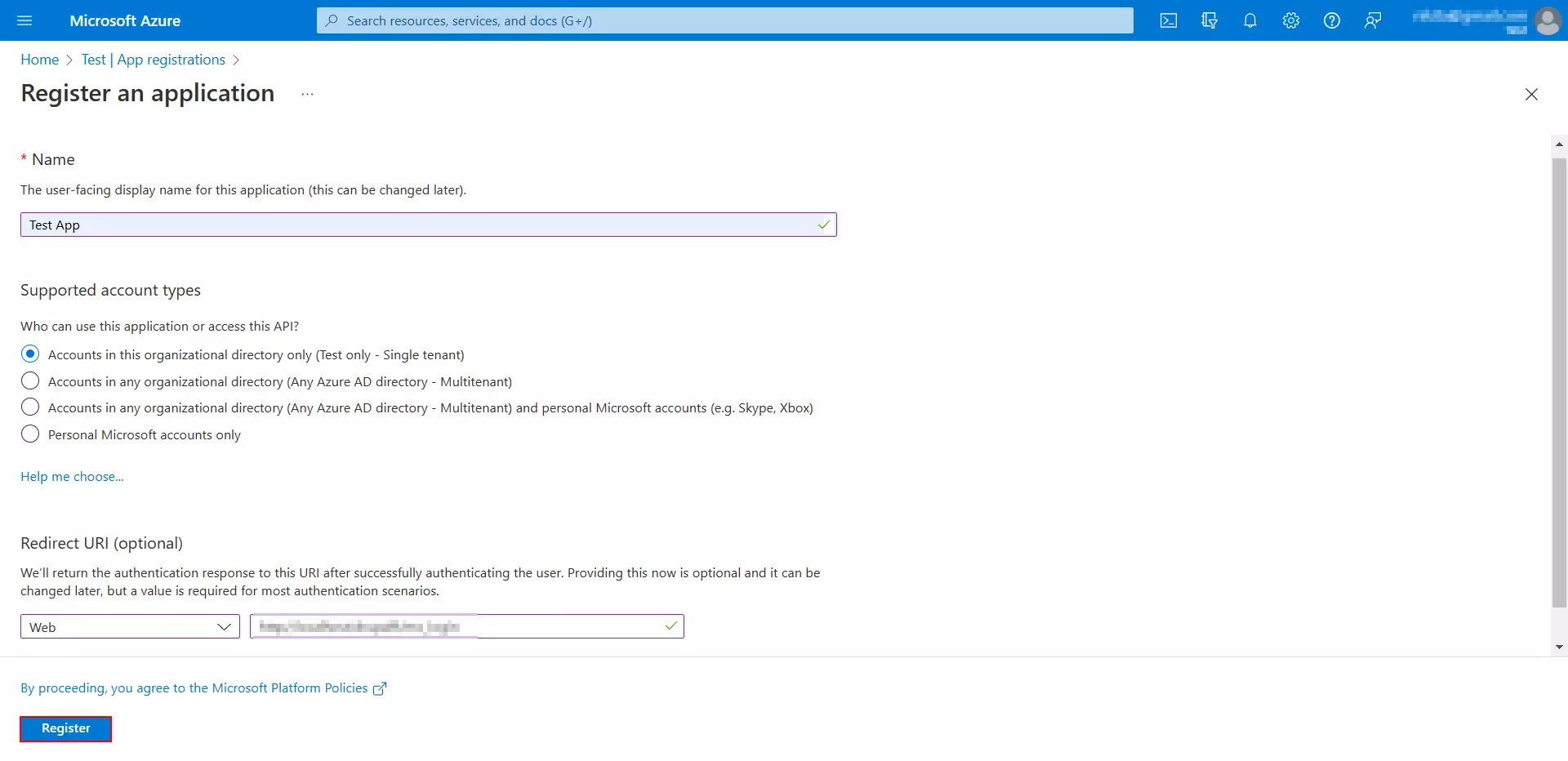
- In the Register an application window, enter the following information:
- Name: Enter the Application name.
- Supported account types: Select the 1st option, Accounts in this organizational directory only (Test only - Single tenant). You can refer the Help me choose link.
- Redirect URI (optional): Select Web from the Select a platform dropdown list. Then, in the text field, paste the previously copied Callback/Redirect URL.
- Click on the Register button.
Integrating Drupal with Microsoft Entra ID
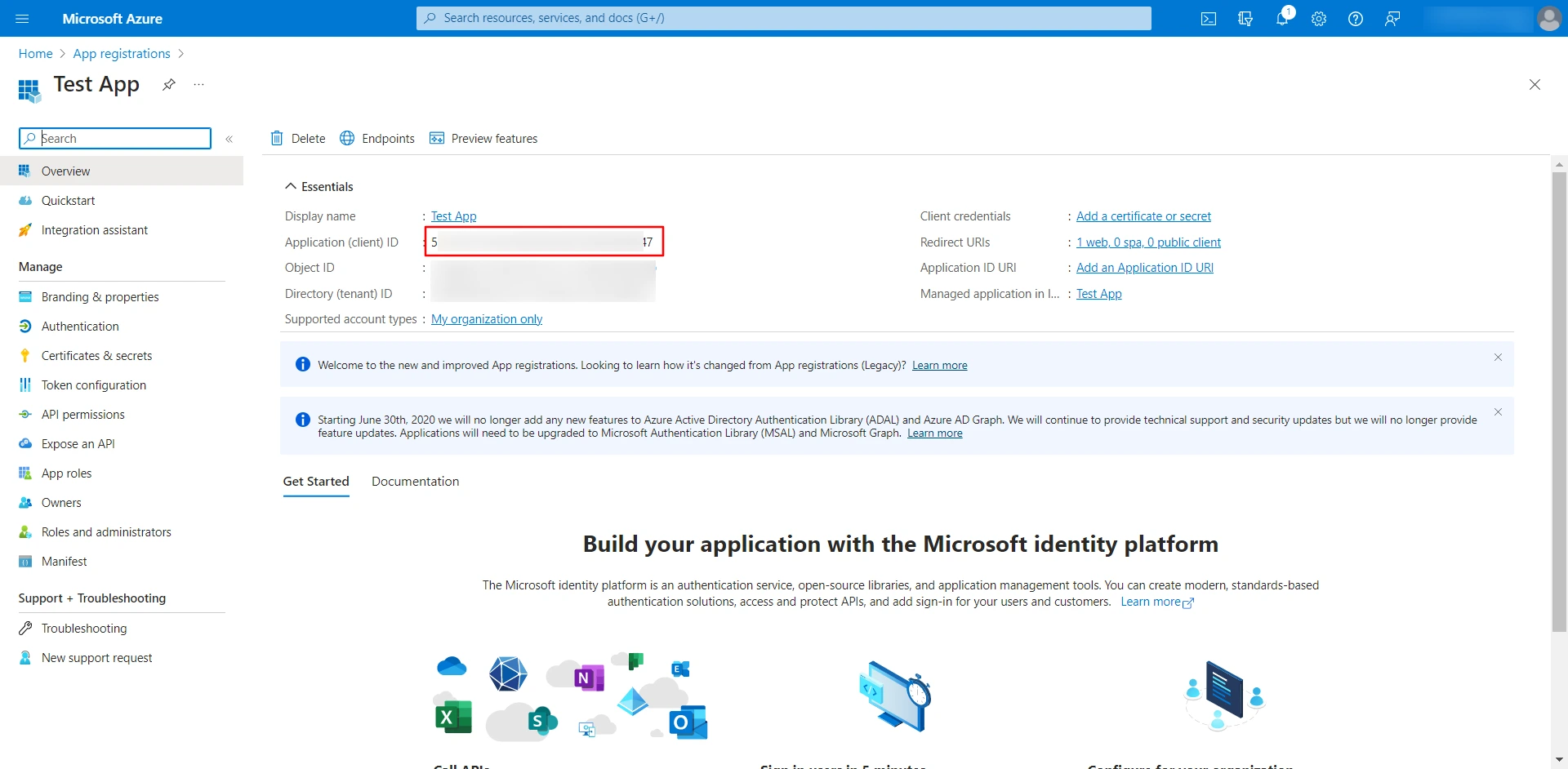
- Microsoft Entra ID assign a unique Application ID to your application. Copy the Application (client) ID. This is your Client ID.
- Paste the copied Application (client) ID into the Client ID text field in the Drupal's Configure OAuth tab.
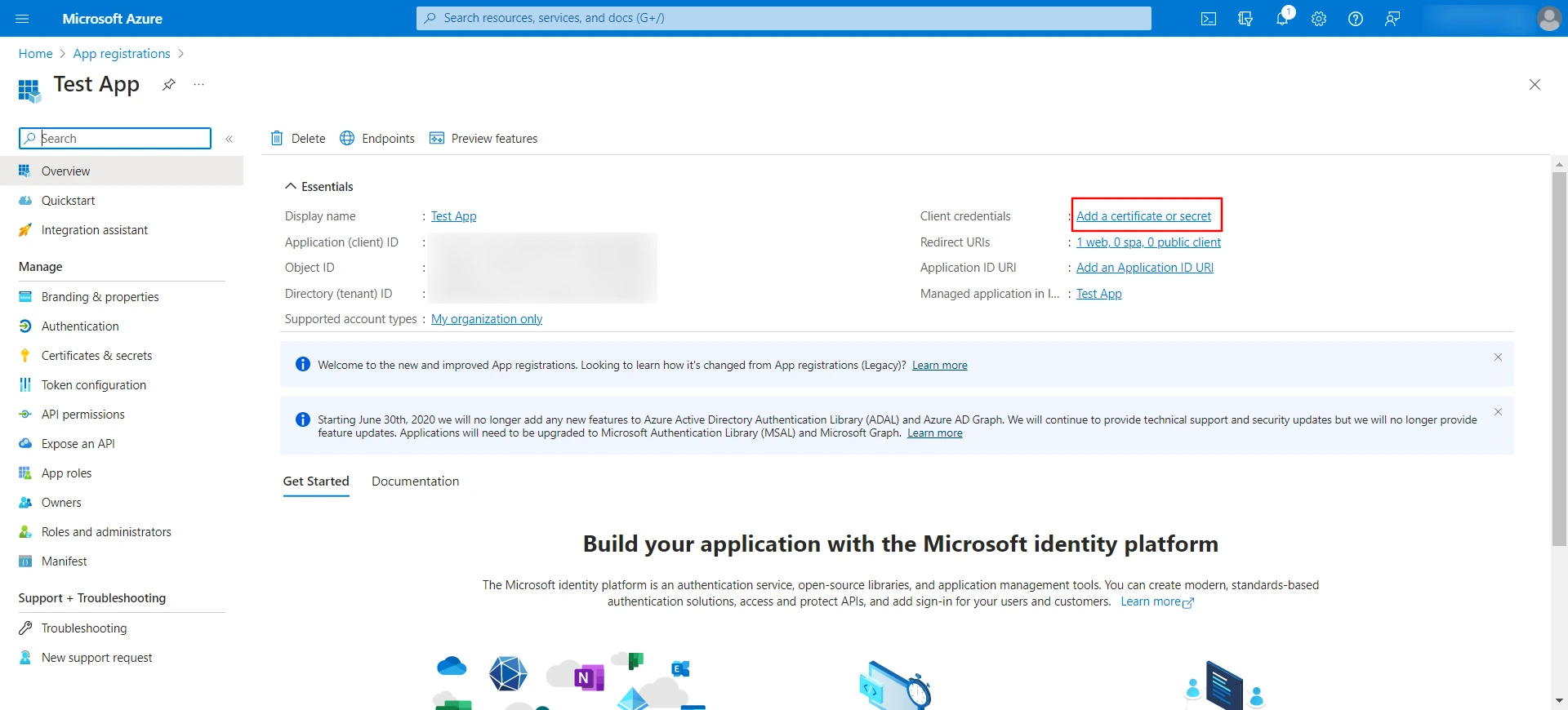
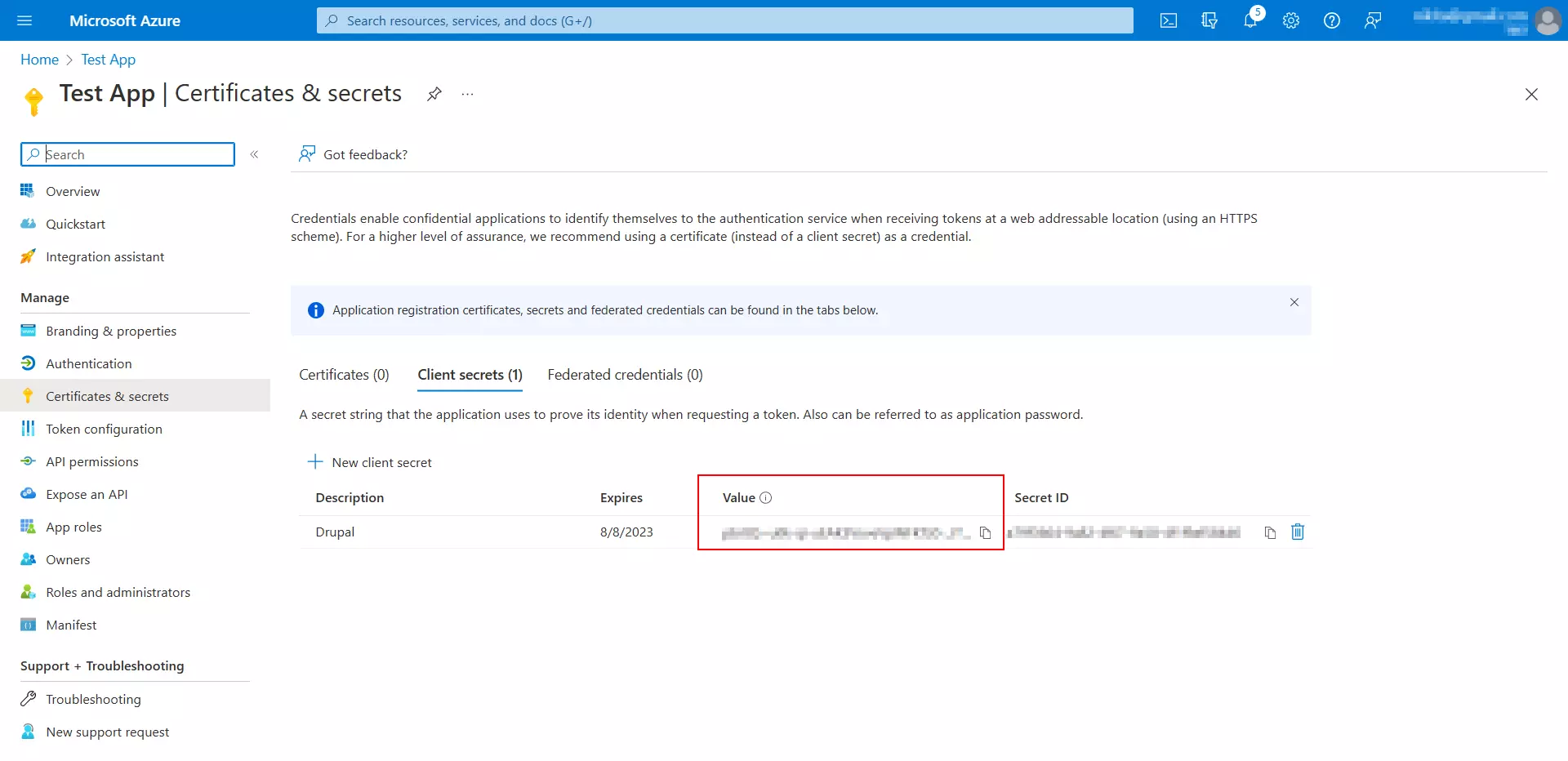
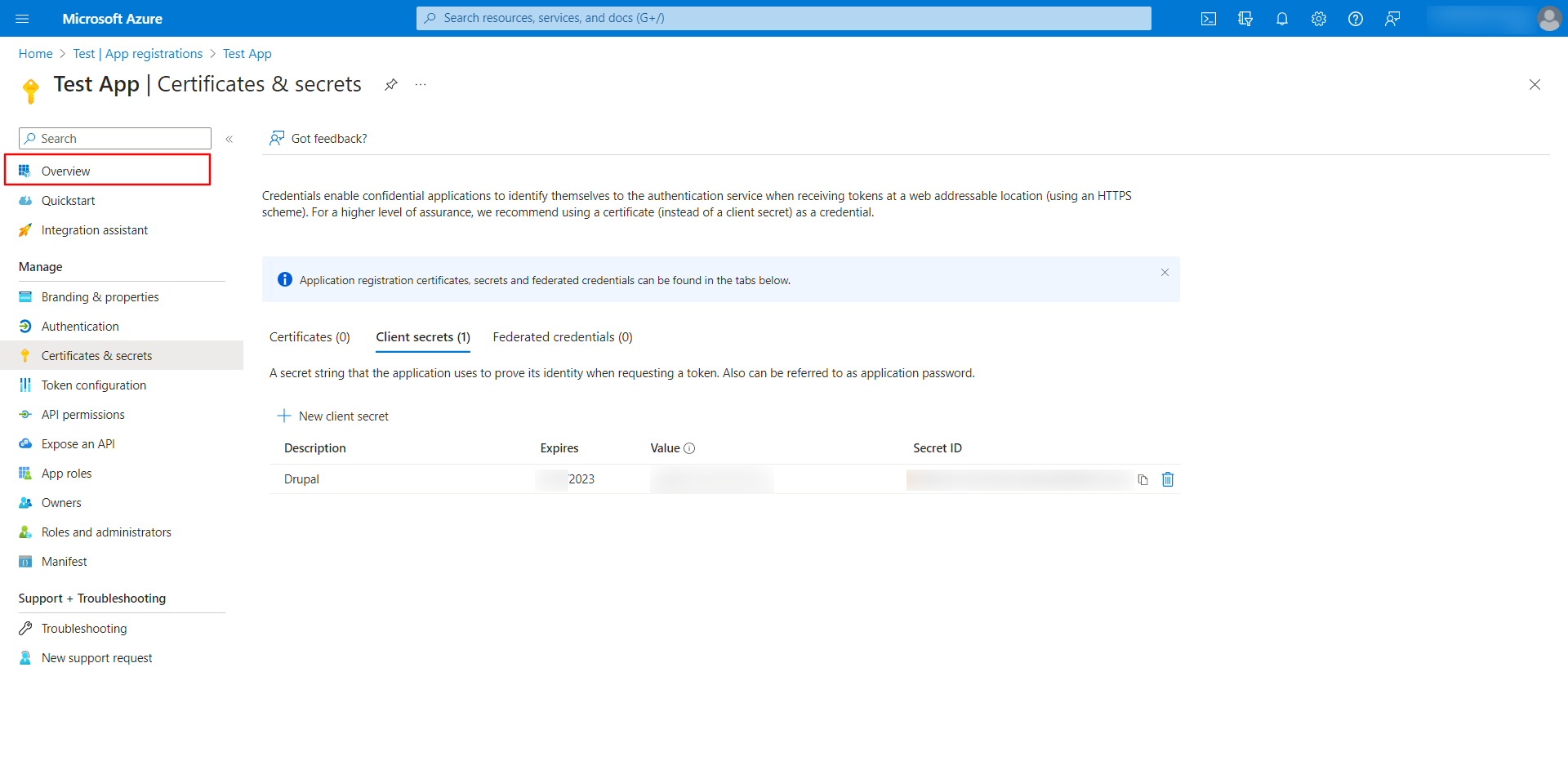
- Navigate to the Azure portal and click on the Add a certificate or secret link.
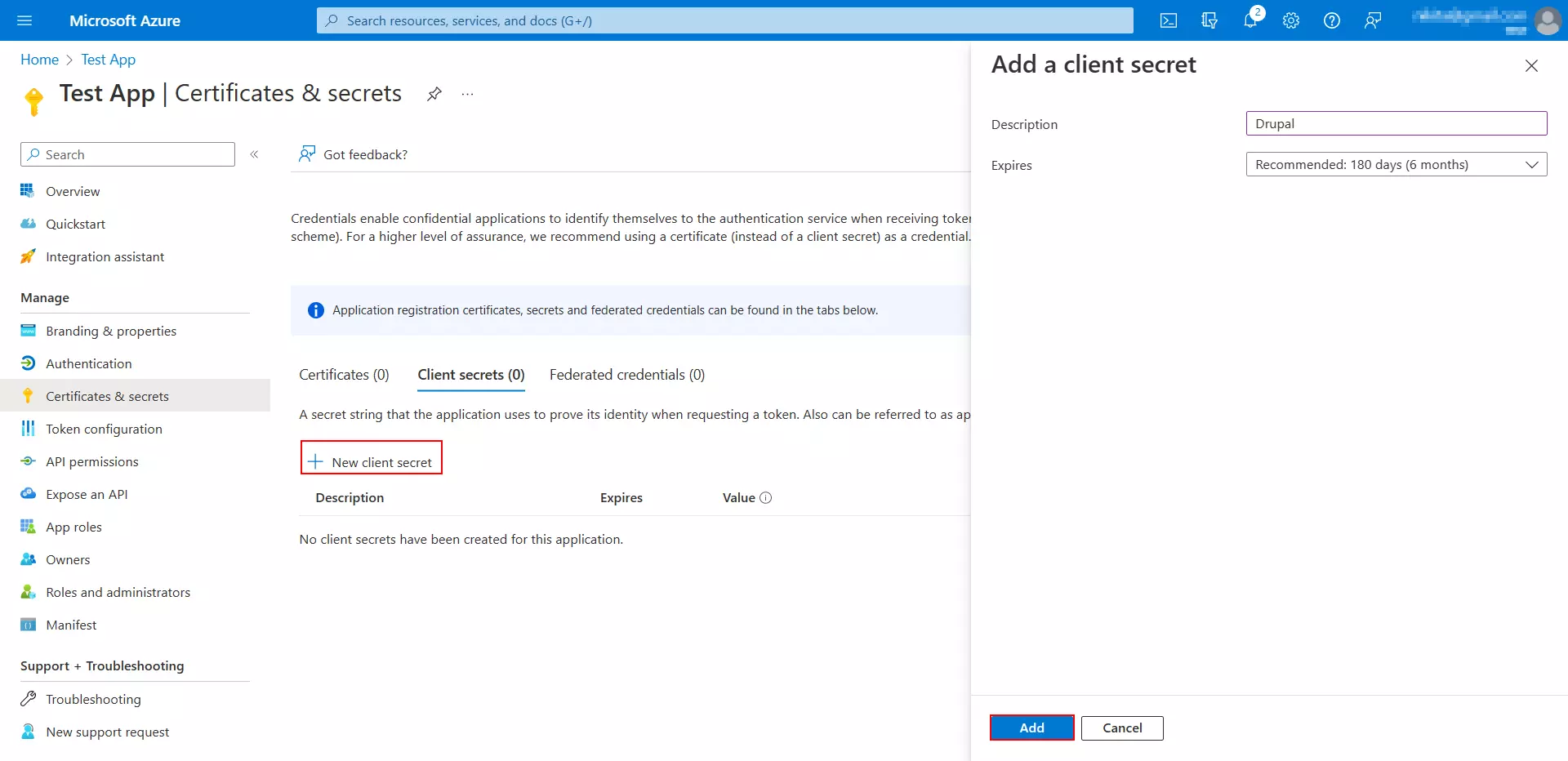
- Click on the New client secret button. In the Add a client secret popup, enter the required information:
- Description: Enter the description for this Secret.
- Expires: Select an expiry duration for this Secret from the dropdown.
- Click on the Add button.
- Copy the Value from the Client secrets tab. This is Client Secret.
- Navigate to the Configure OAuth tab in Drupal and paste the copied Client Secret into the respective text field.
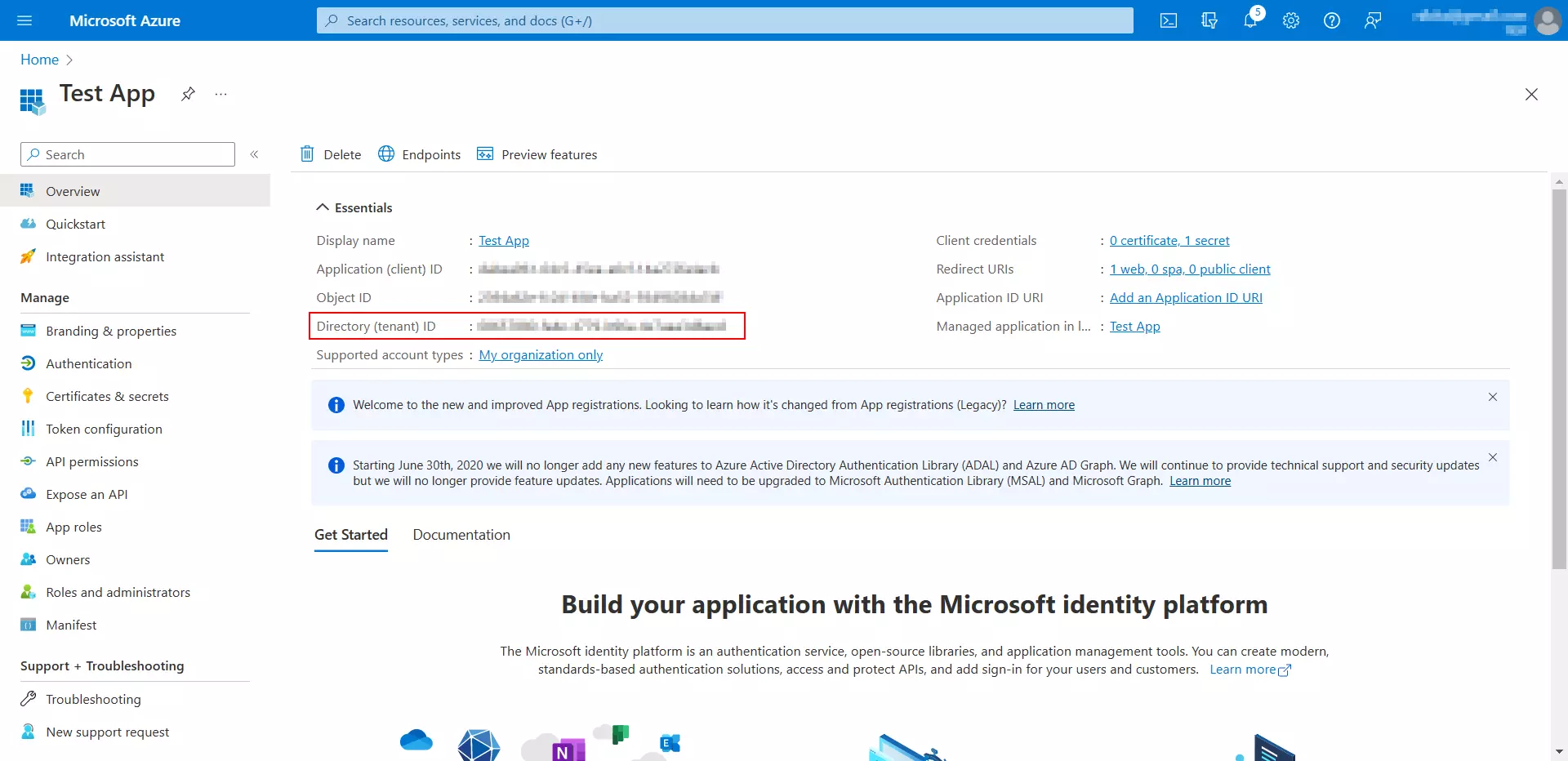
- Go to the Microsoft Entra ID portal.
- Navigate to the Overview from the left side panel.
- Under Essentials section, copy the Directory (tenant) ID. This will be your Tenant-ID.
- In Drupal's Configure OAuth tab replace the previously copied Directory (tenant) ID with the {tenant-id} in the Authorize Endpoint and Access Token Endpoint text fields, respectively.
- Click on the Save Configuration button.
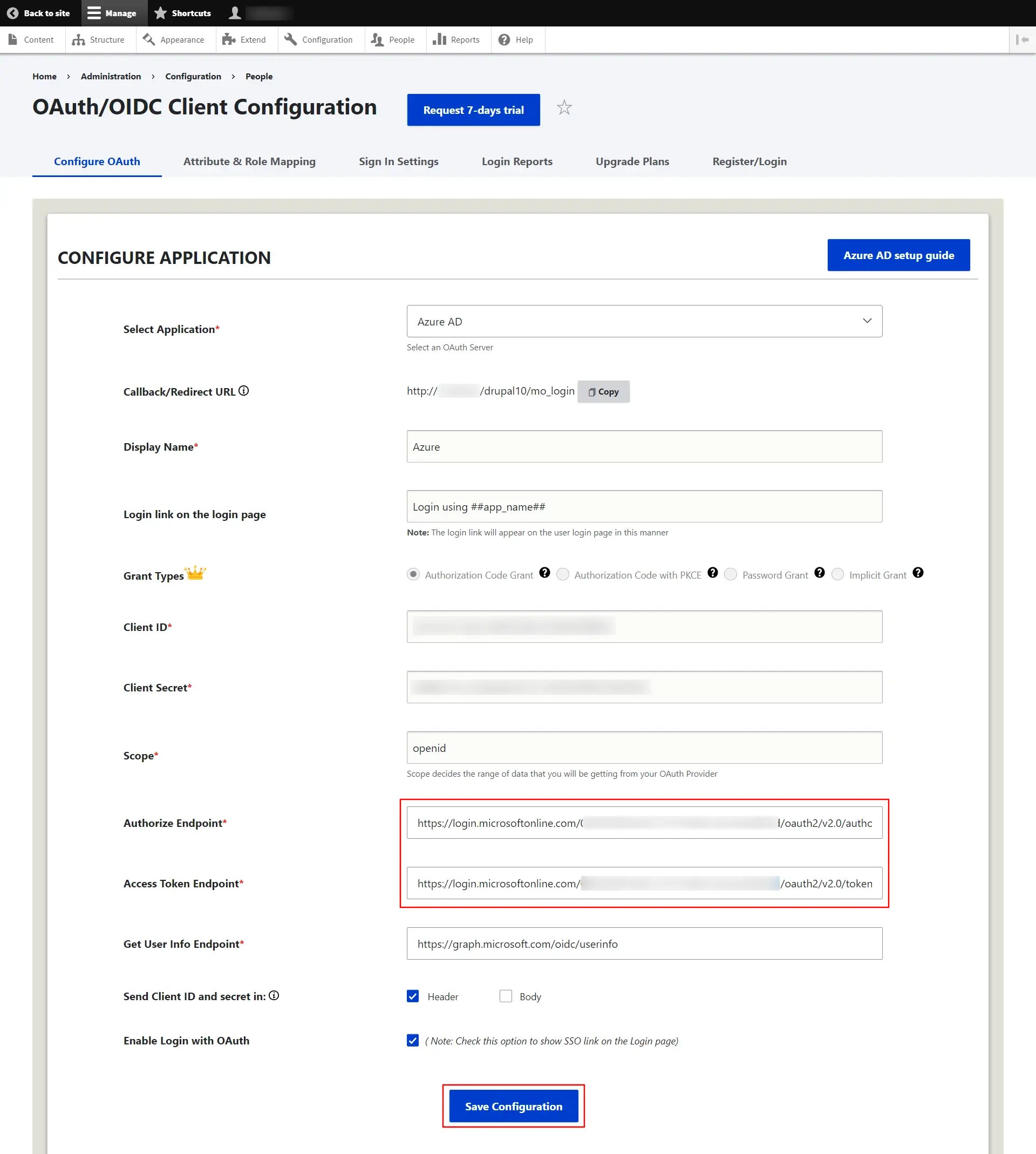
You can also refer to the Microsoft Entra ID Endpoints and scope from the table given below:
| Scope | openid |
| Authorize Endpoint: | https://login.microsoftonline.com/{tenant-id}/oauth2/v2.0/authorize |
| Access Token Endpoint: | https://login.microsoftonline.com/{tenant-id}/oauth2/v2.0/token |
| Get User Info Endpoint: | https://graph.microsoft.com/oidc/userinfo |
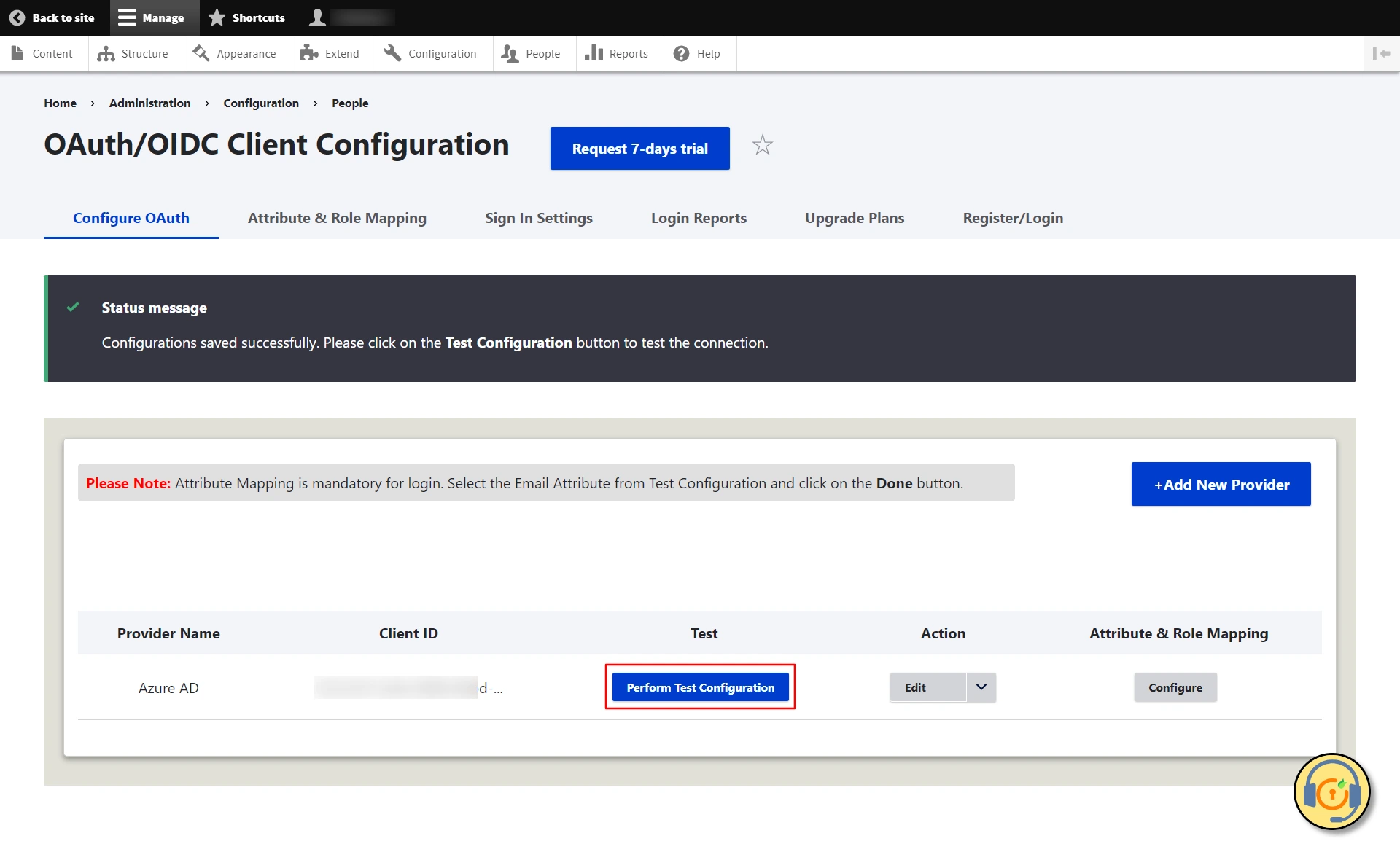
Test Connection between Drupal and Azure Active Directory:
- Click on the Perform Test Configuration button to test the connection.
- On a Test Configuration popup, if you don't have an active session in Microsoft Entra ID on the same browser, you'll be prompted to sign in to Microsoft Entra ID. Once successfully logged in, you'll receive a list of attributes retrieved from Microsoft Entra ID.
- Select the Email Attribute from the dropdown menu in which the user's email ID is obtained and click on the Done button.
- Once clicked on Done button, you will be redirected to the Attribute & Role Mapping tab, in which you can select the Username Attribute from the dropdown list and click on Save Configuration button.
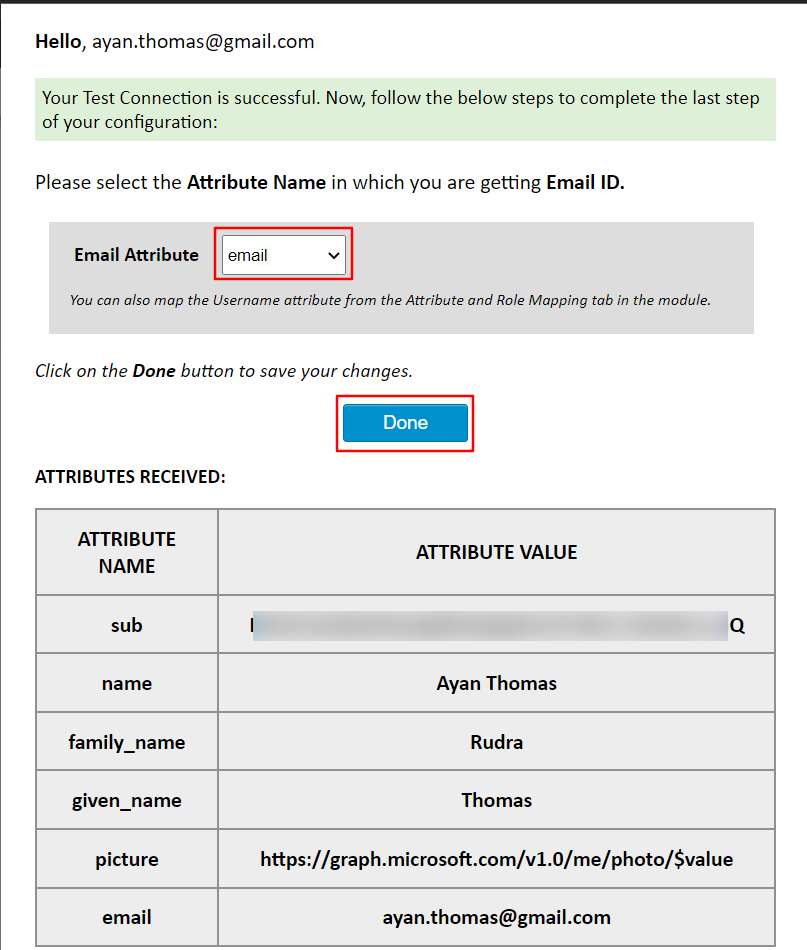
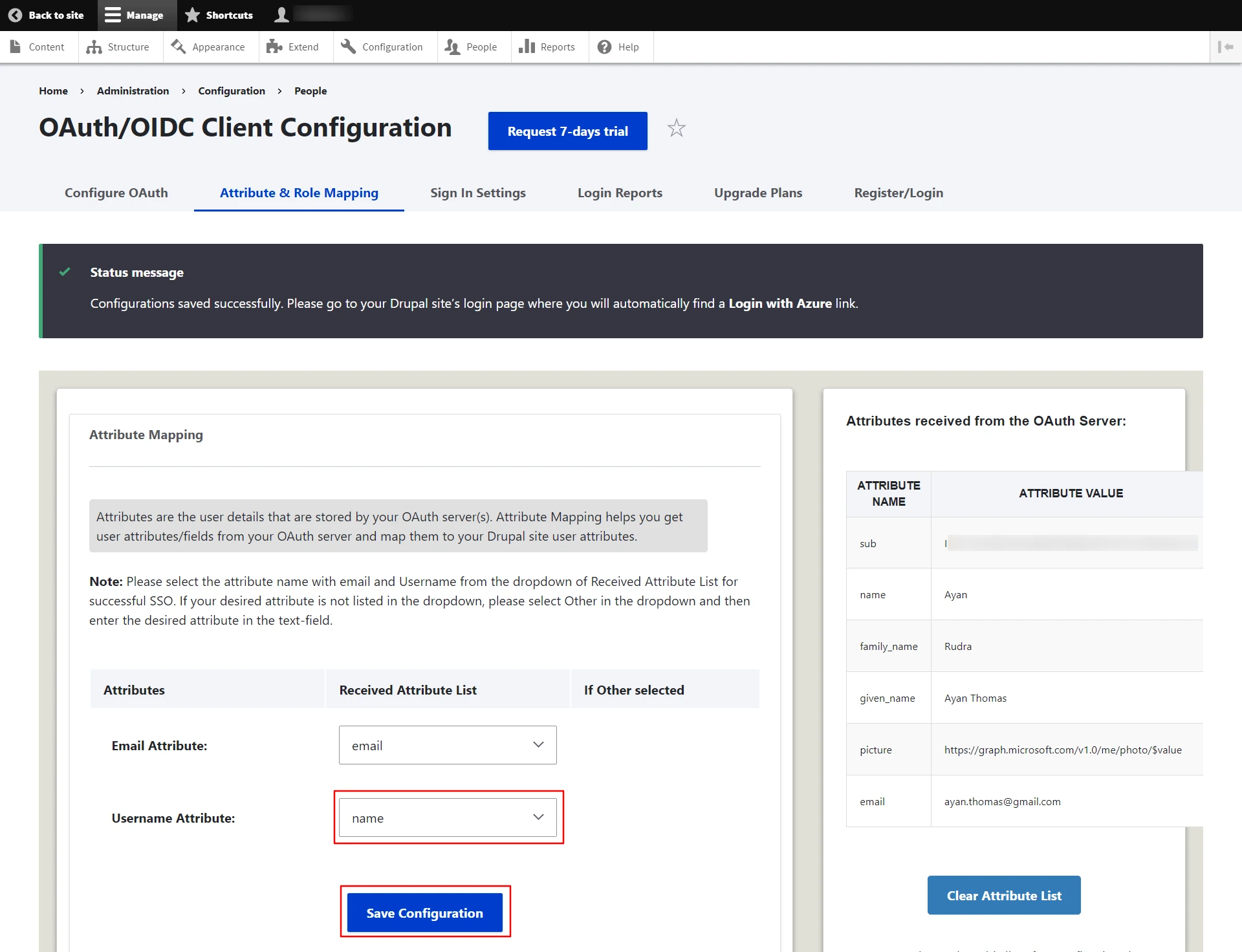
Please note: Mapping the Email Attribute is mandatory for Single Sign-On.
How to perform the SSO?
- Open a new browser/private window and navigate to the Drupal site login page.
- Click on the Login using Azure link to initiate the SSO from Drupal.
- If you want to add the SSO link on other pages, please follow the steps given in the image below:
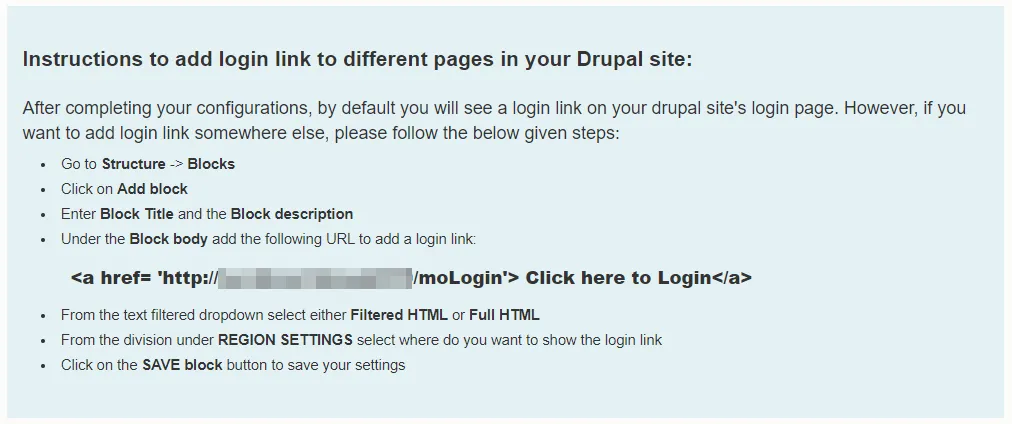
Need Assistance?
If you face any issues during the configuration or if you want some additional features, please contact us at drupalsupport@xecurify.com.
Additional Features:
- Attribute Mapping - map user’s attributes received from OAuth Provider with Drupal fields
- Role mapping - assign a Drupal Role to users on the basis of their role/attribute on the OAuth provider
- Enable single logout - Logout user from the OAuth Provider (i.e. AWS Cognito, Azure AD B2C, Keycloak, Okta) when they logs out form Drupal
- Restrict anonymous access to the complete site or a particular section of the site
- Add Multiple OAuth Provides
- Explore All the features offered by the OAuth Client
Troubleshooting:
Follow the steps mentioned HERE
Follow the steps mentioned HERE
The logout functionality you’ve mentioned here is the default behavior of a module. It’s logging you out of Drupal but not from your Application/Provider. To allow the module to logout from your provider/application account (what you are looking for), you need to make the below configurations: [know more]
As you have upgraded to one of our paid versions of the Drupal module and replaced the free module with the paid one, you must first activate the paid module. Please refer to the below steps. [Know more]
Need Help? We are right here!

Thanks for your inquiry.
If you dont hear from us within 24 hours, please feel free to send a follow up email to info@xecurify.com
Cookie Preferences
Cookie Consent
This privacy statement applies to miniorange websites describing how we handle the personal information. When you visit any website, it may store or retrieve the information on your browser, mostly in the form of the cookies. This information might be about you, your preferences or your device and is mostly used to make the site work as you expect it to. The information does not directly identify you, but it can give you a more personalized web experience. Click on the category headings to check how we handle the cookies. For the privacy statement of our solutions you can refer to the privacy policy.
Strictly Necessary Cookies
Always Active
Necessary cookies help make a website fully usable by enabling the basic functions like site navigation, logging in, filling forms, etc. The cookies used for the functionality do not store any personal identifiable information. However, some parts of the website will not work properly without the cookies.
Performance Cookies
Always Active
These cookies only collect aggregated information about the traffic of the website including - visitors, sources, page clicks and views, etc. This allows us to know more about our most and least popular pages along with users' interaction on the actionable elements and hence letting us improve the performance of our website as well as our services.
