Setup Guide for Azure AD App
Step 1: Setup Azure Active Directory as OAuth Provider
- Sign in to Azure portal.
- Click on view Manage Azure Active Directory.
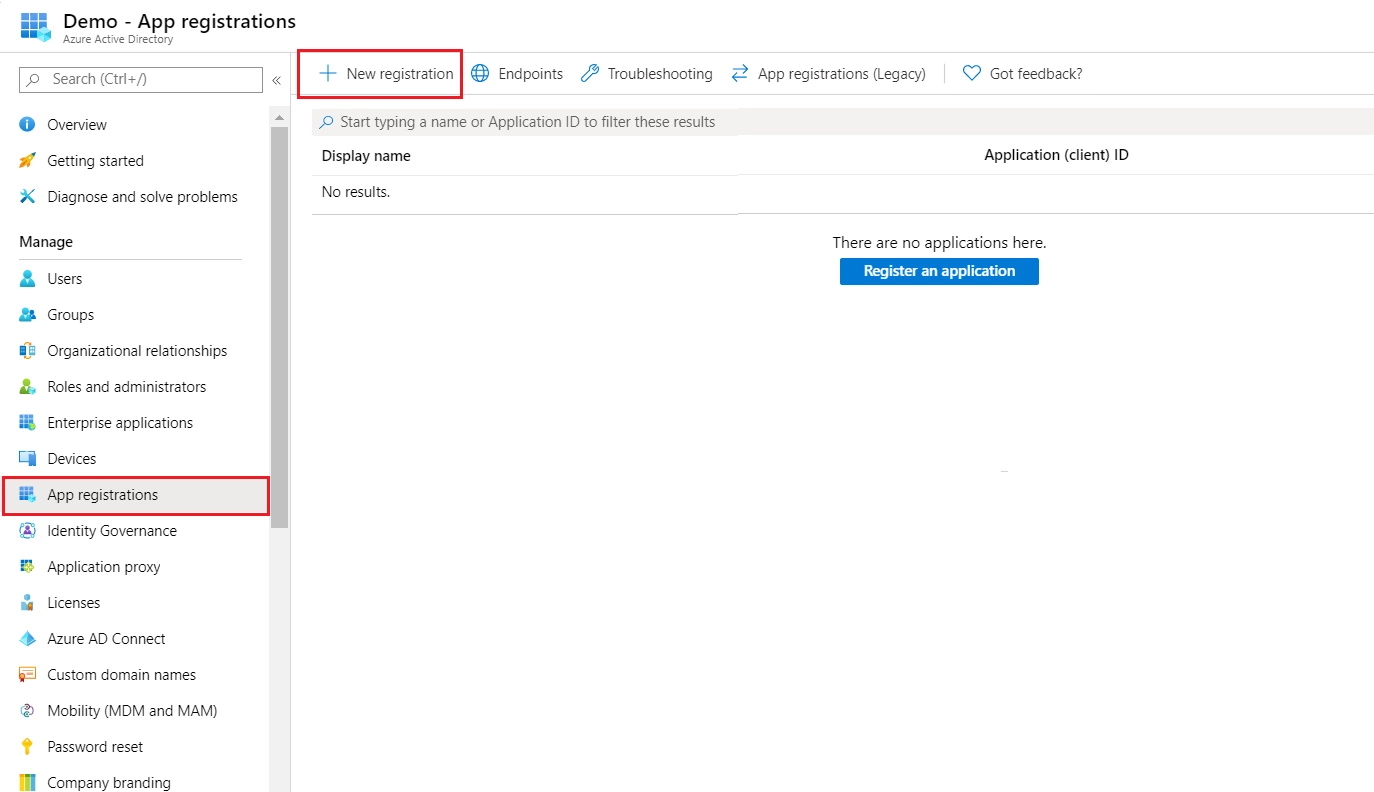
- In the left-hand navigation pane, click the App registrations service, and click New registration.
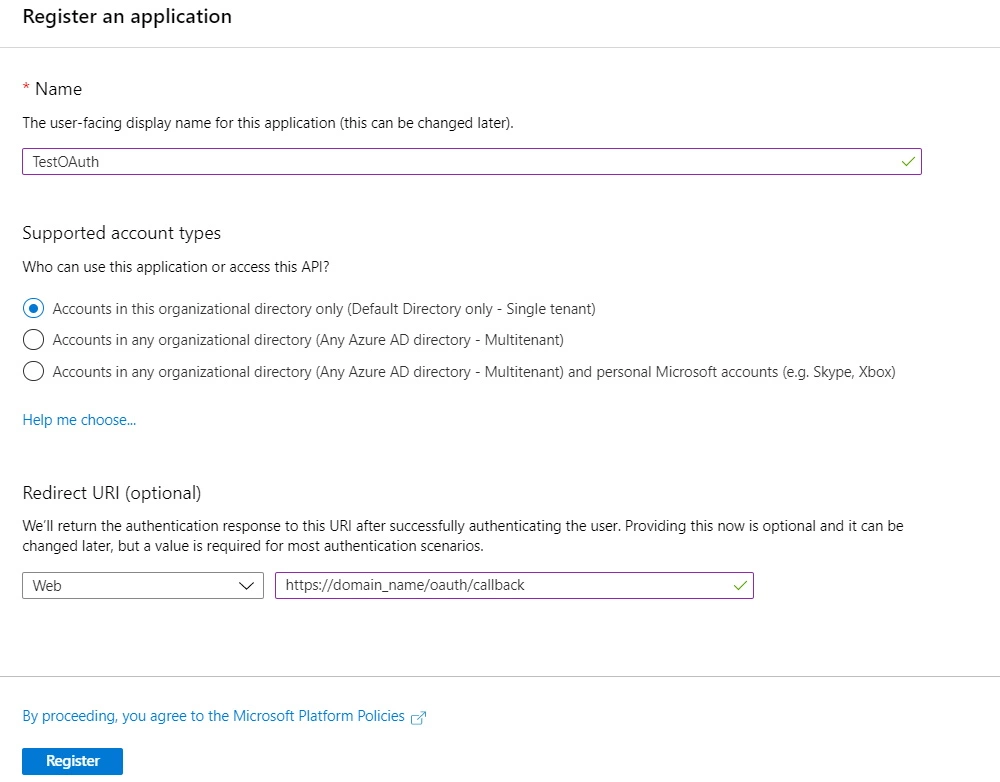
- When the Create page appears, enter your application's registration information.
- In the Redirect URI enter the Callback URL from the plugin. You will find it in the Configure OAuth tab eg: [applicatin-base-url]/plugins/servlet/oauth/callback
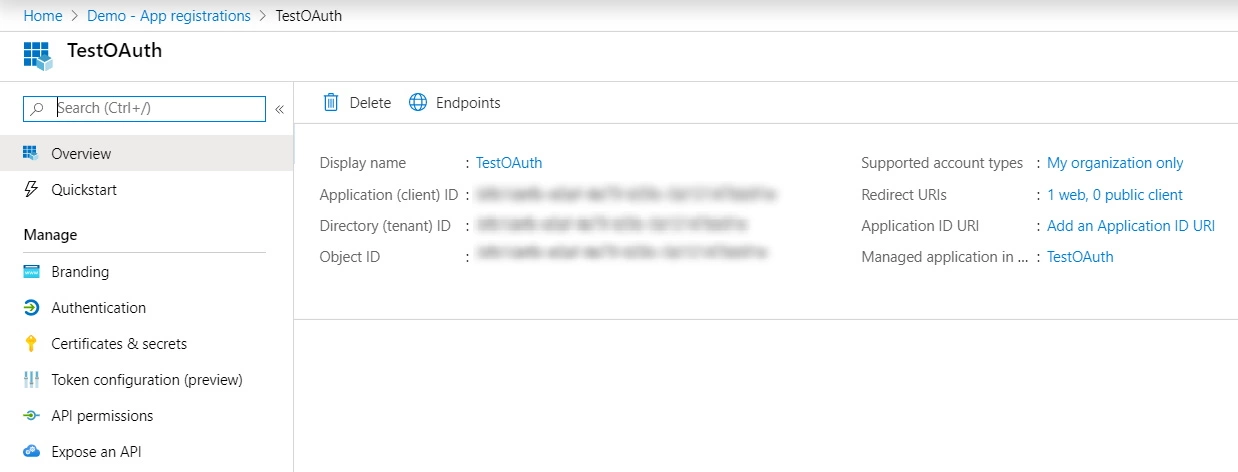
- When finished, click Register. Azure AD assigns a unique Application ID to your application. Copy Application ID and the Directory ID , this will be your Client ID and Tenent ID.
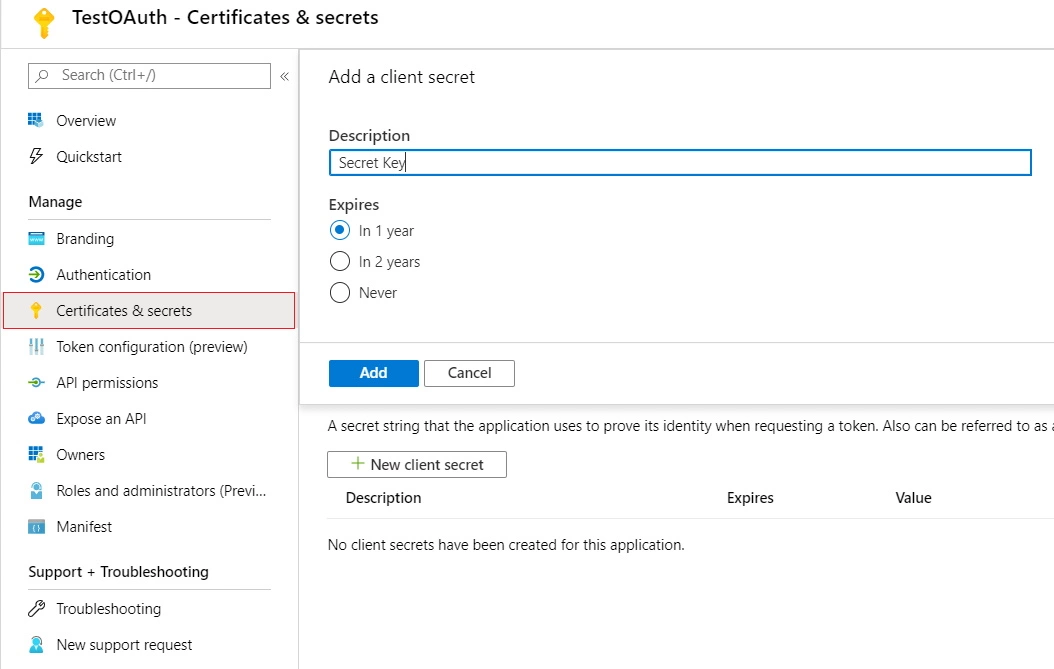
- Go to Certificates and Secrets from the left navigaton pane and click on New Client Secret. Enter description and expiration time and click on ADD option.
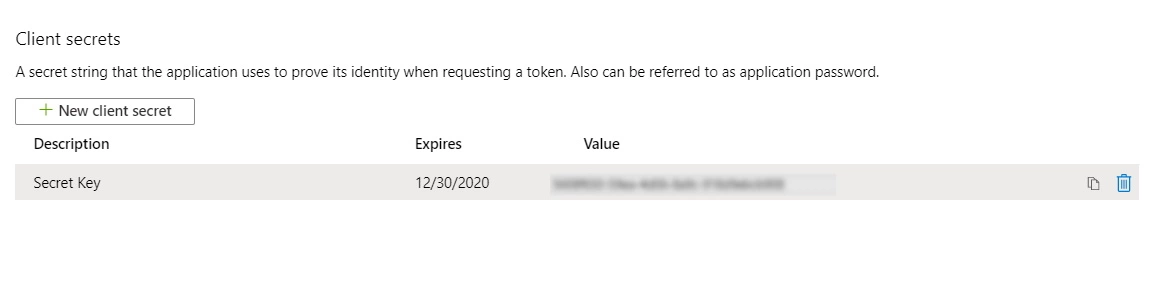
- Copy value. This will be your Secret key.
×
![centrify_3]()
Trending searches:

