JIRA provides REST APIs to perform a number of operations such as Create Issue, Delete Issue, Add Comment, Create Space, etc. However, it supports only two authentication methods for REST APIs:
- Basic Authentication
- Using JIRA as OAuth 1.0 Provider
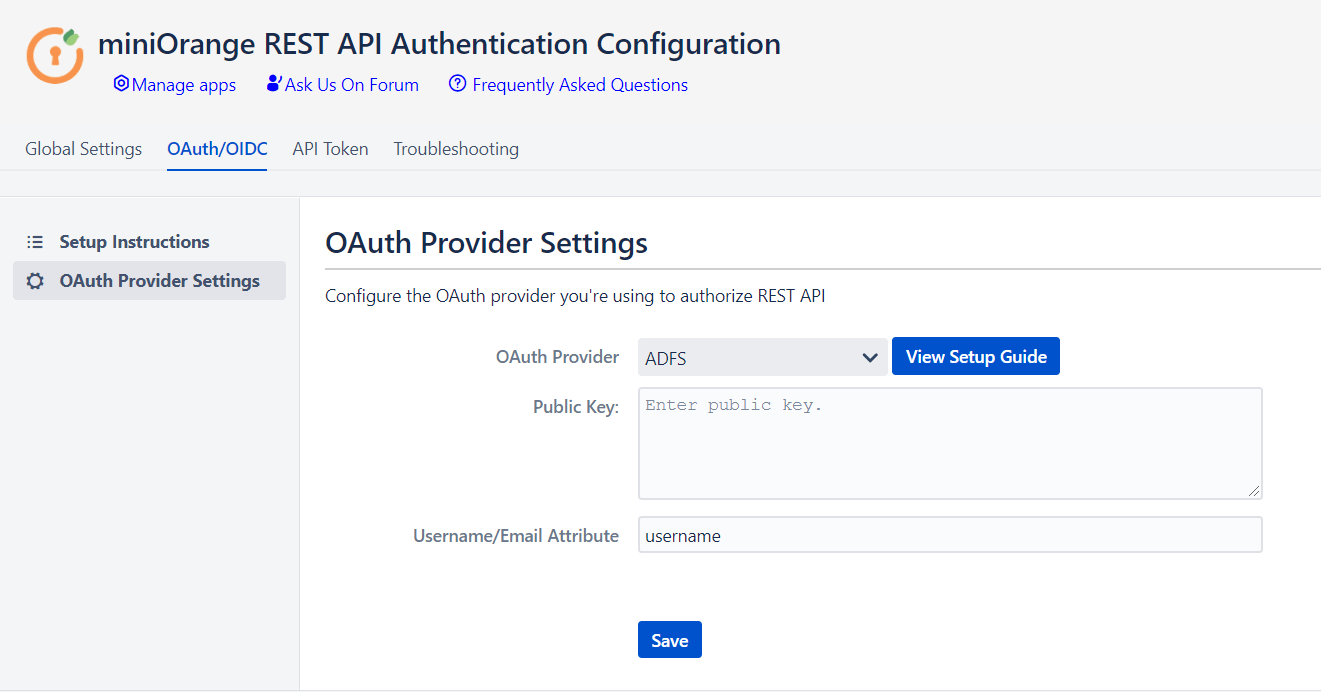
The REST API Authentication plugin for JIRA allows you to use any third party OAuth 2.0 provider/ OpenID connect to authenticate REST APIs. Here we will go through a guide to configure ADFS as Provider.
Step 1: Setup ADFS as OAuth Provider
- To perform SSO with ADFS as Provider, your application must be https enabled.
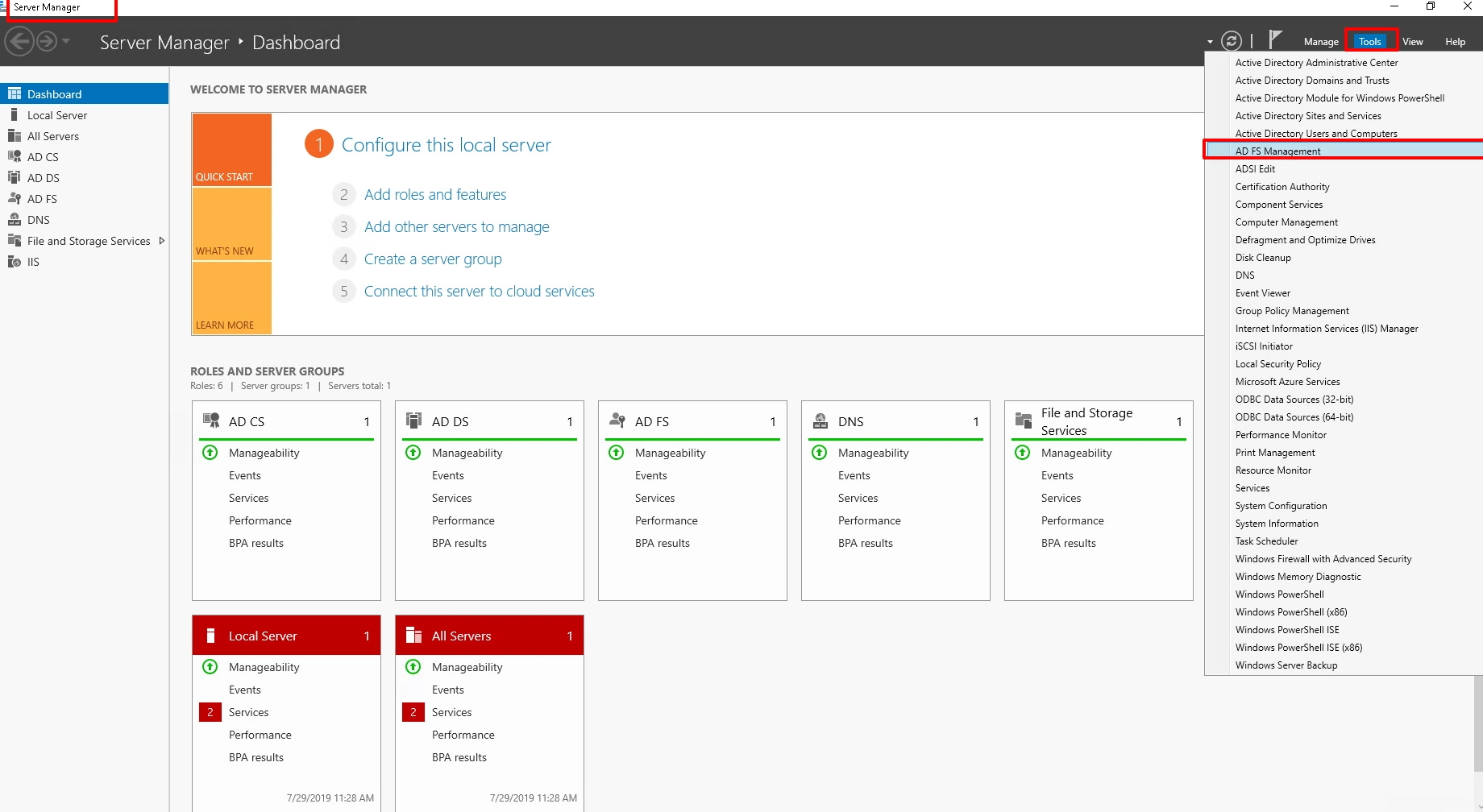
- Navigate to Server Manager Dashboard->Tools->ADFS Management.
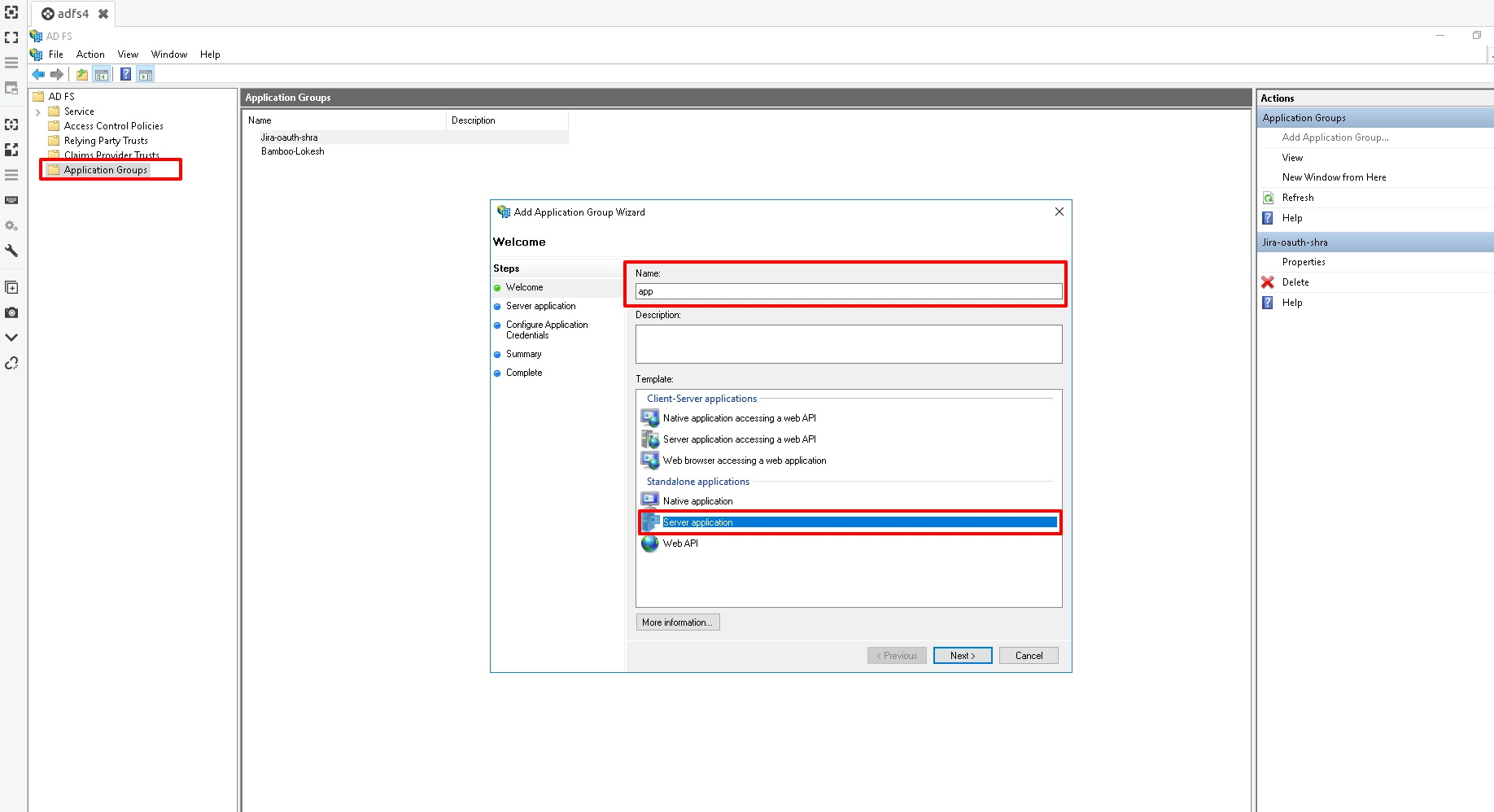
- Navigate to ADFS->Application Groups. Right click on Application Groups & click on Add Application group then enter Application Name. Select Server Application & click on next.
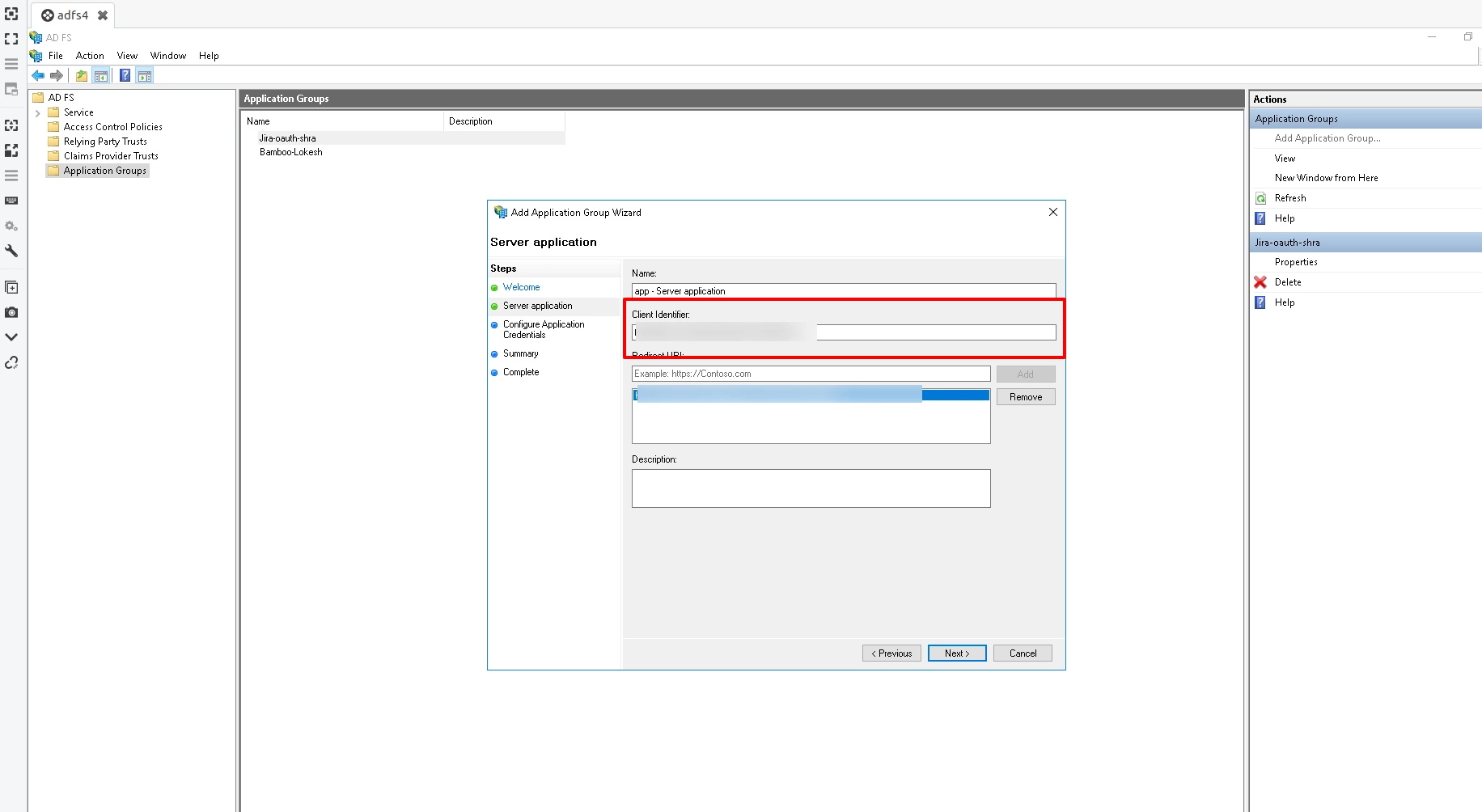
- Copy Client Identifier. This is your Client ID. Add Callback URL in Redirect URL. You can get this callback URL from plugin. Click on next.
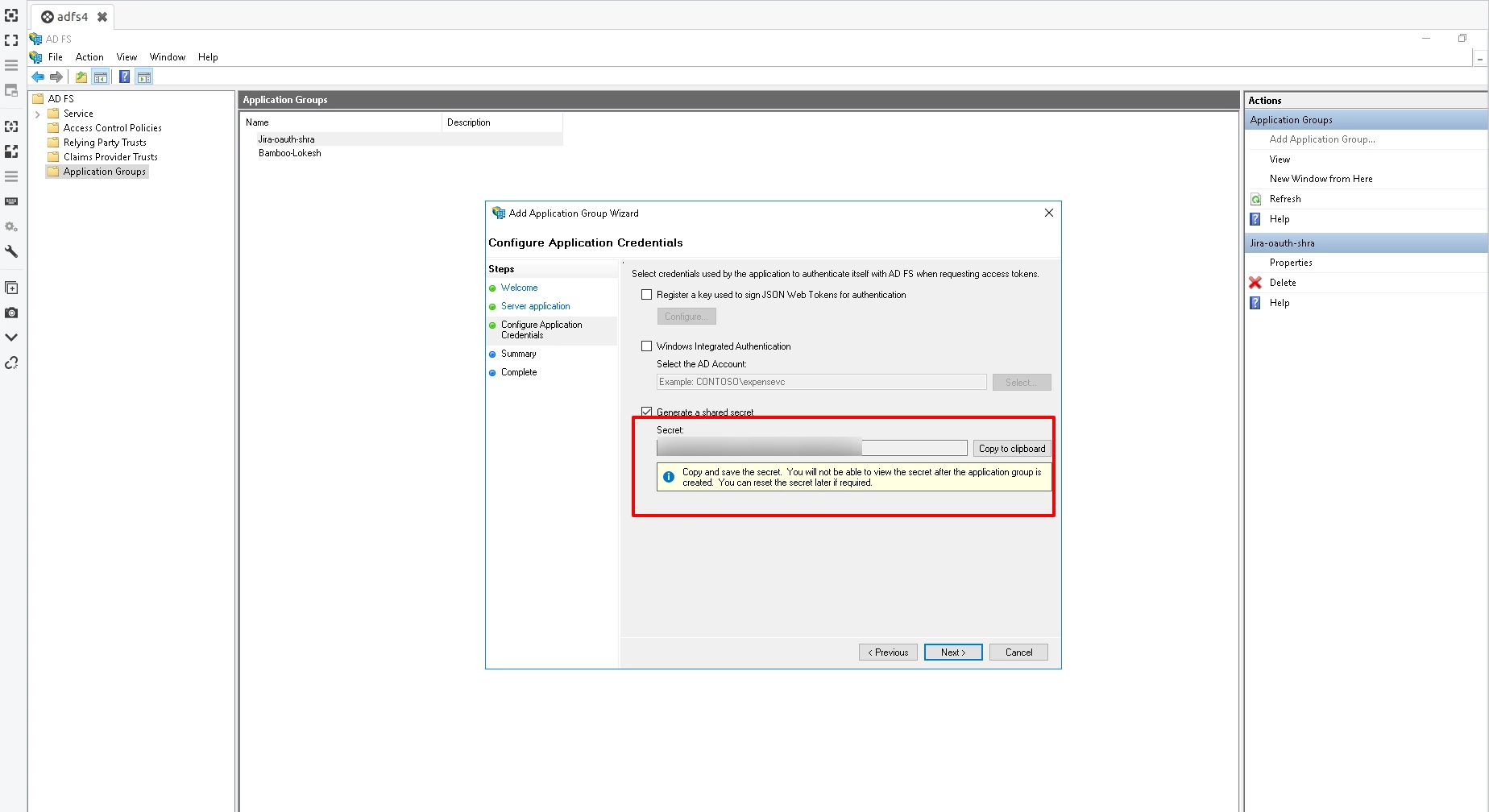
- Click on Generate shared secret. Copy the Secret value. This is your Client Secret. Click on Next.
- On the Summary screen, click Next. On the Complete screen, click Close.
- Now, right-click on the newly added Application Group and select Properties.
- Click on Add application from App Properties.
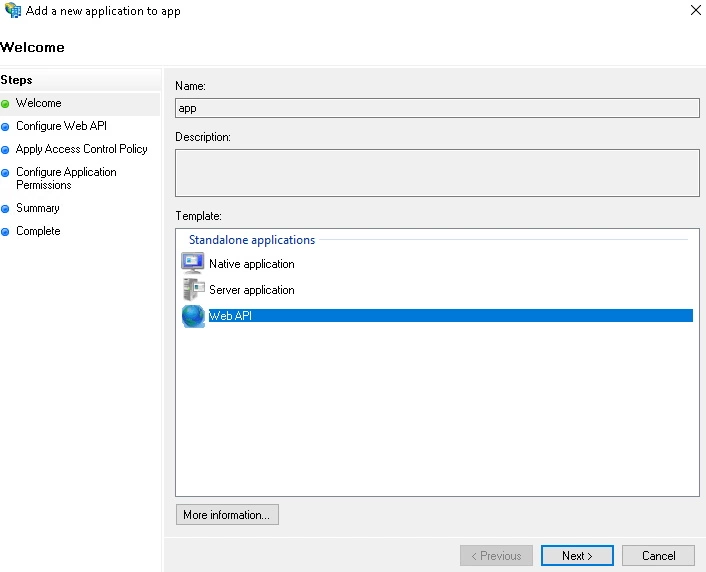
- Click on the Add application. Then select Web API and click Next.
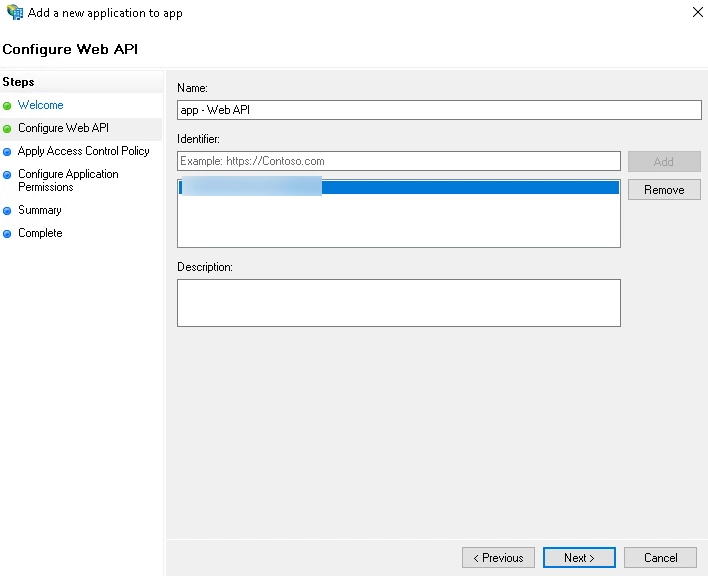
- On the Configure Web API screen, enter the domain name address into the Identifier section. Click Add. Click Next.
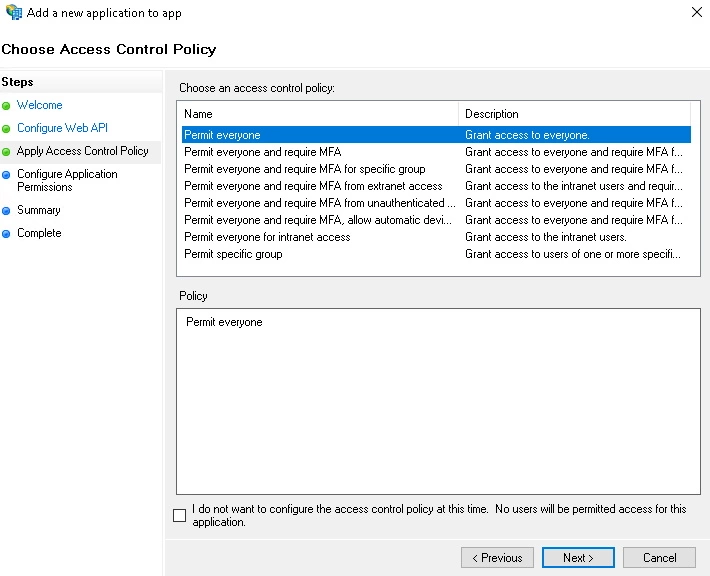
- On the Choose Access Control Policy screen, select Permit everyone and click Next.
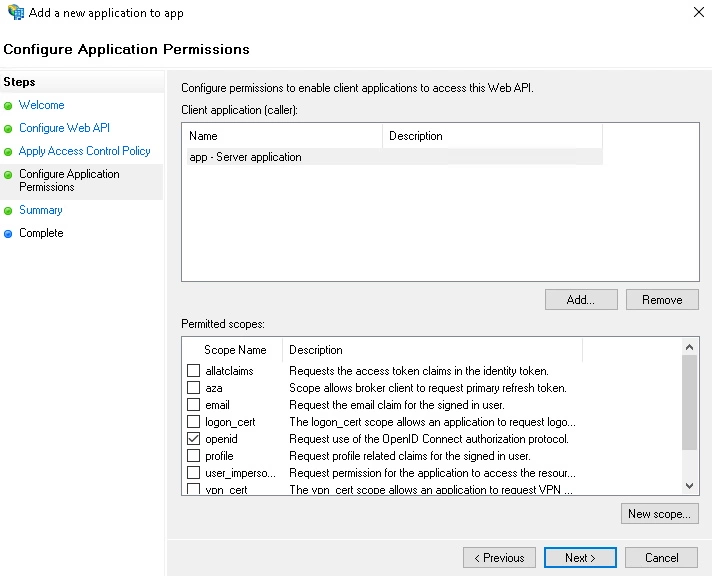
- On the Configure Application Permission, by default openid is selected as a scope & click on next.
- On the Summary screen, click Next. On the Complete screen, click Close.
- On the Sample Application Properties click OK.