Set Passwordless authentication with the Authy Authenticator | WordPress
Passwordless Authentication with Authy Authenticator
Passwordless authentication with Authy authenticator allows users to log in without the need of remembering a password. Instead of conventional username and password, users needs to scan the QR code to register their account. After successful registration you will get one time security token, which they can then use to log in. Unlike possession or something that a user has, authentication that is based on something the user know (such as a password, passphrase, or PIN code) is susceptible to easy theft, sharing by users, and requires constant management and handling by users as well as web servers. Most of the users might use the same credentials for different systems. This substantially weakens the security of all those websites if the credentials are leaked or obtained by an unauthorized user.You can download miniOrange 2-factor plugin using the following link.
What are the benefits of Passwordless Authentication with Auhty Authenticator?
Better Security
User controlled passwords are a major vulnerability because users reuse passwords and are able to share them with others. The security of passwordless authentication systems depends on the proof of identity required and their implementation. For example, using secure push notifications to the account holder’s mobile device is generally considered more secure than passwords. One TIme Password over SMS on mobile devices are generally used as a second factor of authentication apart from traditional username and password combination.
Better Control
Phishing, reuse, and sharing are common issues when relying on passwords, with passwordless login users have better control over their account and are less susceptible to phishing. With passwords out of the picture, both user experience and security improve.
What does Passwordless Login prevent with Auhty Authenticator?
Password Spraying
Password spraying is an attack that attempts to access a large number of accounts (usernames) with a few commonly used passwords. Traditional brute-force attacks attempt to gain unauthorized access to a single account by guessing the password. In password spraying, an attacker tries combinations of username and passwords from the list of commonly used passwords.
Credentials Stuffing
Credentials stuffing is a type of attack in which stolen credentials are used which consists of a list of usernames along with their passwords. Credentials stuffing is different from the brute force attack in the sense that it does not try to guess the credentials of a user rather uses a list of credentials leaked. Credential stuffing attacks are possible because many users reuse the same username/password combination across multiple sites, with one survey reporting that 81% of users have reused a password across two or more sites and 25% of users use the same passwords across a majority of their accounts.
Brute Force Attack
Brute force attack is a type of attack in which a combination of username and password is guessed by trial and error. It consists of repeated login attempts made with different combinations each time. Guessing a short password can be relatively simple, but that isn’t necessarily the case for longer passwords or encryption keys, the difficulty of brute force attacks grows exponentially the longer the password or key is.
Passwordless Login in WordPress using miniOrange 2 Factor Authentication plugin with Authy Authenticator
The login can be done by username and 2-factor or only username which can be decided based on the user role. If a role is not allowed for passwordless login they will log in with a password and username.
There are Two options:
Login with Password + 2nd Factor:
You can log in with WordPress username + password, and then 2nd-factor authentication.
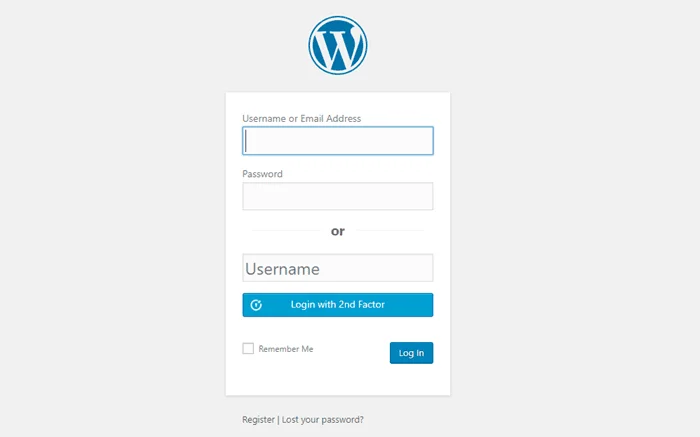
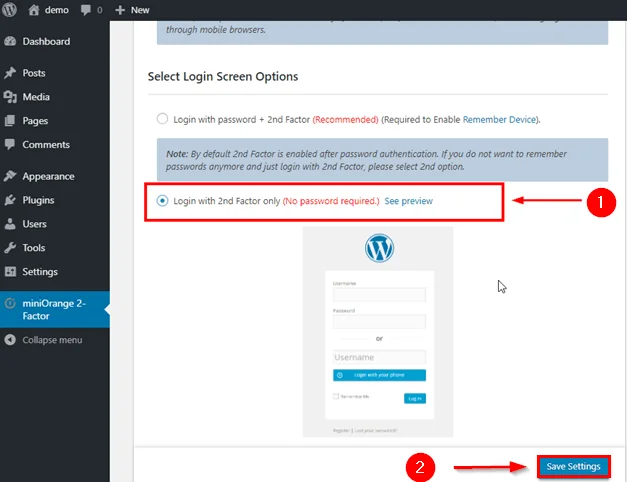
Login with 2nd Factor only:
In this second option you get variations of Username + Password and Username + 2-Factor Authentication in the same window.
What are the add-ons related to WordPress Login?
Enforce two-factor verification to WordPress users during user enrollment
With the miniOrange two-factor plugin for WordPress login, you can notify WordPress users to configure Telegram verification during inline registration so that the second security layer will get added to their WordPress account.two-factor verification compatible with Woocommerce forms
This method of verification is compatible with almost all WordPress login forms and also with the WooCommerce form.Passwordless Login with two-factor Verification
You can set Passwordless Login to your WordPress login with no worries by setting up Telegram verification with just simple steps.Customization
miniOrange login security also provides customization options. You can customize the two-factor prompt user interface according to the design of your WordPress website.Backup methods
In case you lose your two-factor authentication ability, you will also get backup methods like an alternate two-factor method or alternate extra security solution to get back to your WordPress account.
Business Trial For Free
If you don't find what you are looking for, please contact us at info@miniorange.com or call us at +1 978 658 9387.

