Shibboleth-2 as Idp for Moodle
Step 1: Setup Shibboleth-2 as Identity Provider
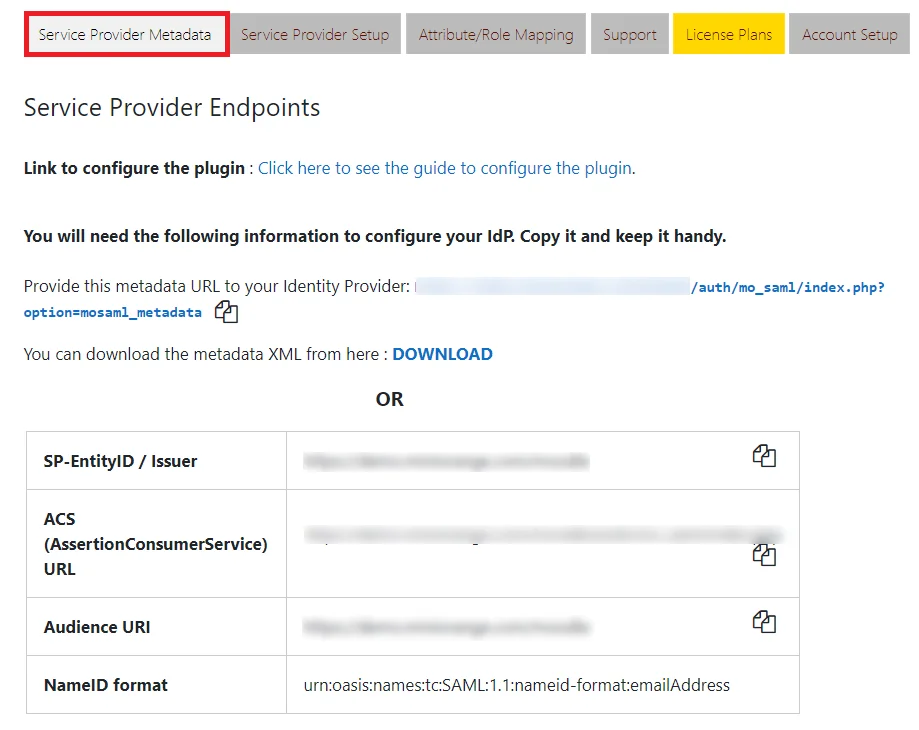
- In the miniOrange SAML 2.0 SSO plugin, navigate to Service Provider Metadata tab. Here, you can find the SP metadata such as SP Entity ID and ACS (AssertionConsumerService) URL which are required to configure the Identity Provider.
- In conf/relying-party.xml, configure Service Provider like this
- Make sure your Shibboleth server is sending Email Address of the user in Name ID. In attribute-resolver.xml, get the email attribute as Name ID:
- In attribute-filter.xml, release the email attribute:
- Restart the Shibboleth Server.
- You need to configure these endpoints in the Service Provider.
Follow the steps below to configure Shibboleth-2 as IdP
 Configure Shibboleth-2 as IdP
Configure Shibboleth-2 as IdP
<MetadataProviderxsi:type="InlineMetadataProvider"
xmlns="urn
:mace:shibboleth:2.0:metadata" id="MyInlineMetadata">
<EntitiesDescriptorxmlns="urn:oasis:names:tc:SAML:2.0:metadata">
<md:EntityDescriptorxmlns:md="urn:oasis:names:tc:SAML:2
.0:metadata"
entityID="<ENTITY_ID_FROM_PLUGIN>">
<md:SPSSODescriptorAuthnRequestsSigned="false"
WantAssertionsSigned="true" protocolSupportEnumeration=
"urn:oasis:names:tc:SAML:2.0:protocol">
<
urn:oasis:names:tc:SAML:1
.1:nameidformat:emailAddress</md:NameIDFormat>
<md:AssertionConsumerService
Binding="urn
:oasis:names:tc:SAML:2.0:bindings:https-POST"
Location="<ACS_URL_FROM_PLUGIN>"
index="1"/>
</md:SPSSODescriptor>
</md:EntityDescriptor>
</EntitiesDescriptor>
</MetadataProvider>
<resolver:AttributeDefinitionxsi:type="ad:Si
mple" id="email"
sourceAttributeID="mail">
<resolver:Dependency ref="ldapConnector" />
<resolver:AttributeEncoderxsi:type="enc:SAML2
StringNameID"
nameFormat="urn:oasis:names:tc:SAML:1.1:
nameid-format:emailAddress"/>
</resolver:AttributeDefinition>
<afp:AttributeFilterPolicy id="releaseTransientIdToAnyone">
<afp:PolicyRequirementRulexsi:type="basic:ANY"/>
<afp:AttributeRuleattributeID="email">
<afp:PermitValueRulexsi:type="basic:ANY"/>
</afp:AttributeRule>
</afp:AttributeFilterPolicy>
| IDP Entity ID | https://<your_domain>/idp/shibboleth |
| Single Login URL | https://<your_domain>/idp/profile/SAML2/Redirect/SSO |
| X.509 Certificate | The public key certificate of your Shibboleth server |
×
![]()
Trending searches:

