Shibboleth as Idp for wordpress
Shibboleth Single Sign-On(SSO) login for WordPress can be achieved by using our WordPress SAML Single Sign-On(SSO) plugin. Our plugin is compatible with all the SAML compliant Identity providers. Here we will go through a step-by-step guide to configure SSO login between Wordpress site and Shibboleth by considering Shibboleth as IdP(Identity provider) and WordPress as SP(Service provider).
 Pre-requisites : Download And Installation
Pre-requisites : Download And Installation
To configure Shibboleth as SAML IdP with WordPress, you will need to install the miniOrange WP SAML SP SSO plugin:
Steps to configure Shibboleth Single Sign-On (SSO) Login into WordPress(WP):
After successfully Downloading Shibboleth.
Step 1: Setup Shibboleth as IdP (Identity Provider)
Follow the steps below to configure Shibboleth as IdP
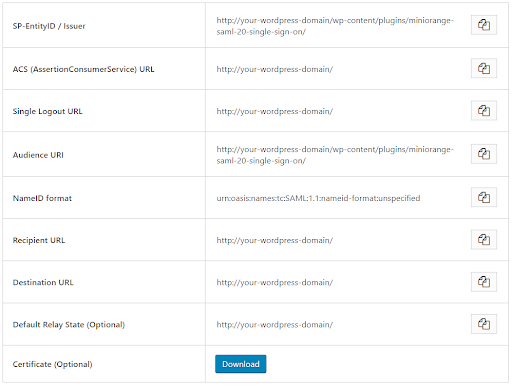
- In the miniOrange SAML SP SSO plugin, navigate to Service Provider Metadata tab. Here, you can find the SP metadata such as SP Entity ID and ACS (AssertionConsumerService) URL which are required to configure the Identity Provider.
- In conf/idp.properties, uncomment and set 'idp.encryption.optional' to true.
eg. idp.encryption.optional = true - In conf/metadata-providers.xml, configure Service Provider like this
- In conf/saml-nameid.properties, uncomment and set default NameID as Email Address like this
- In conf/saml-nameid-xml, search for shibboleth.SAML2NameIDGenerators. Uncomment the shibboleth.SAML2AttributeSourcedGenerator bean and comment all other ref beans
- Make sure you have defined AttributeDefinition in conf/attribute-resolver.xml.
- Make sure you have AttributeFilterPolicy defined in conf/attribute-filter.xml.
- Restart the Shibboleth server.
- You need to configure these endpoints in the miniOrange SAML plugin.
- You have successfully configured Shibboleth as SAML IdP ( Identity Provider) for achieving Shibboleth SSO login into your WordPress (WP) Site.
<MetadataProvider xmlns:samlmd="urn:oasis:
names:tc:SAML:2.0:metadata"
id="miniOrangeInLineEntity" xsi:type="InlineMetadata
Provider"
sortKey="1">
<samlmd:EntityDescriptor ID="entity" entityID="<SP-EntityID /
Issuer
from Service Provider Info tab in plugin.>"
validUntil="2020-09-06T04:13:32Z">
<samlmd:SPSSODescriptor AuthnRequests
Signed="false"
WantAssertionsSigned="true"
protocolSupportEnumeration="urn:oasis:names:
tc:SAML:2.0:protocol">
<samlmd:NameIDFormat>
urn:oasis:names:tc:SAML:
1.1:nameid-format:emailAddress
</samlmd:NameIDFormat>
<samlmd:AssertionConsumerService
Binding="urn:oasis:names:tc:
SAML:2.0:bindings:HTTP-POST"
Location="<ACS (AssertionConsumerService) URL from
Step1 of
the plugin under Identity Provider Tab.>"
index="1" />
</samlmd:SPSSODescriptor>
</samlmd:EntityDescriptor>
</MetadataProvider>
idp.nameid.saml2.default=urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress
<!-- SAML 2 NameID Generation -->
<util:list id="shibboleth.SAML2NameIDGenerators">
<!--<ref bean="shibboleth.SAML2TransientGenerator" /> -->
<!-->ref bean="shibboleth.SAML2PersistentGenerator" /> -->
<bean parent="shibboleth.SAML2AttributeSourcedGenerator"
p:format="urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress"
p:attributeSourceIds="#{ {'email'} }" />
</util:list>
<!-- Note: AttributeDefinitionid must be same as what
you provided in
attributeSourceIds in conf/saml-nameid.xml -->
<resolver:AttributeDefinitionxsi:type="ad:Simple"
id="email"
sourceAttributeID="mail">
<resolver:Dependency ref="ldapConnector" />
<resolver:AttributeEncoderxsi:type="enc:SAML2String"
name="email"
friendlyName="email" />
</resolver:AttributeDefinition >
<resolver:DataConnector id="ldapConnector"
xsi:type="dc:LDAPDirectory"
ldapURL="%{idp.authn.LDAP.ldapURL}"
baseDN="%{idp.authn.LDAP.baseDN}"
principal="%{idp.authn.LDAP.bindDN}"
principalCredential="%{idp.authn.LDAP.bindDNCredential}">
<dc:FilterTemplate>
<!-- Define you User Search Filter here -->
<![CDATA[
(&(objectclass=*)
(cn=$requestContext.principalName)) ]]>
</dc:FilterTemplate>
<dc:ReturnAttributes>*</dc:ReturnAttributes>
</resolver:DataConnector>
<afp:AttributeFilterPolicy id="ldapAttributes">
<afp:PolicyRequirementRulexsi:type="basic:ANY"/>
<afp:AttributeRuleattributeID="email">
<afp:PermitValueRulexsi:type="basic:ANY"/>
</afp:AttributeRule>
</afp:AttributeFilterPolicy>
| IDP Entity ID | https://<your_domain>/idp/shibboleth |
| Single Login URL | https://<your_domain>/idp/profile/SAML2/Redirect/SSO |
| Single Logout URL | https://<your_domain>/idp/shibboleth |
| X.509 Certificate | The public key certificate of your Shibboleth server |
×
![]()
Trending searches:

