Step By Step Guides to set up Jboss Keycloak, Bitium, G Suite, Centrify as IDP for Bitbucket
miniOrange SAML Single Sign On (SSO) For Bitbucket allows users sign in to Bitbucket Server with your SAML 2.0 capable Identity Provider. SAML Single Sign on (SSO) acts as a SAML 2.0 Service Provider and securely authenticate users with your SAML 2.0 Identity Provider.
Here are the Step by Step Guides for different Identity Providers for BitBucket
| IDP | Links |
|---|---|
| ADFS | Click Here |
| Azure AD | Click Here |
| Bitium | Click Here |
| Centrify | Click Here |
| G Suite | Click Here |
| Jboss Keycloak | Click Here |
| Okta | Click Here |
| OneLogin | Click Here |
| Salesforce | Click Here |
Step 1: Download the plugin from marketplace and Install it in Bitbucket
- Login as administrator in Bitbucket.
- Click the administration and choose Add-ons.
- The Manage add-ons screen loads.
- Locate SAML Single Sign On for Bitbucket via search.
- Results include add-on versions compatible with your Bitbucket instance.
- Click Install to download the add-on.
Step 2: Register/Login with miniOrange using addon
- Click on Configure button after installing the add-on.
- Register with miniOrange using a simple form in add-on.
- If you are Already Registered with miniOrange, you can direclty login in to the plugin .
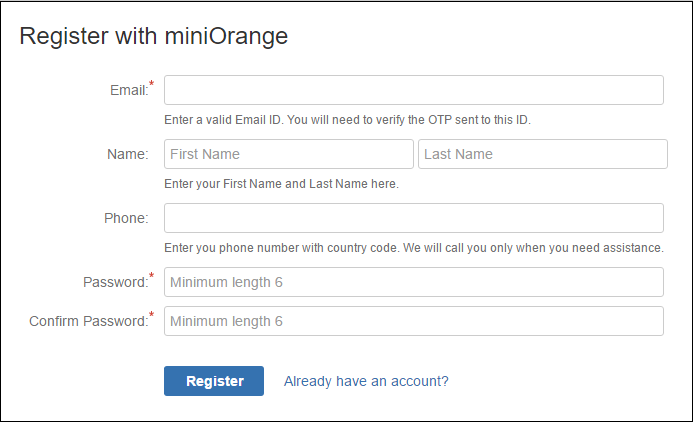
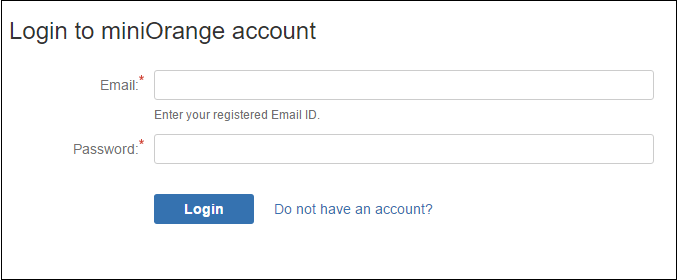
Step 3: Configuring the plugin
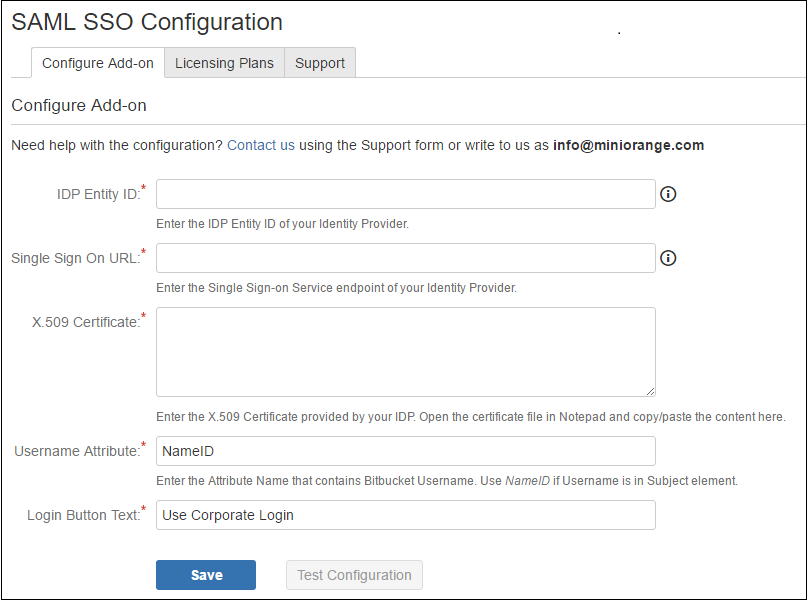
- Using IdP information user could add details in Configure SP.
- Provide the required settings (i.e. IdP Entity ID, IdP Single SignOn Service Url, X.509 certificate) in the plugin and save it.
FOR EXAMPLE
| IdP Entity Id | https://auth.miniorange.com/moas |
| Single Sign On URL | https://auth.miniorange.com/moas/idp/samlsso |
| Identity Provider Certificate | Upload the certificate downloaded from miniOrange Admin Console |
| Username Attribute | Bitbucket Username |
| Login Button Text | miniOrange |
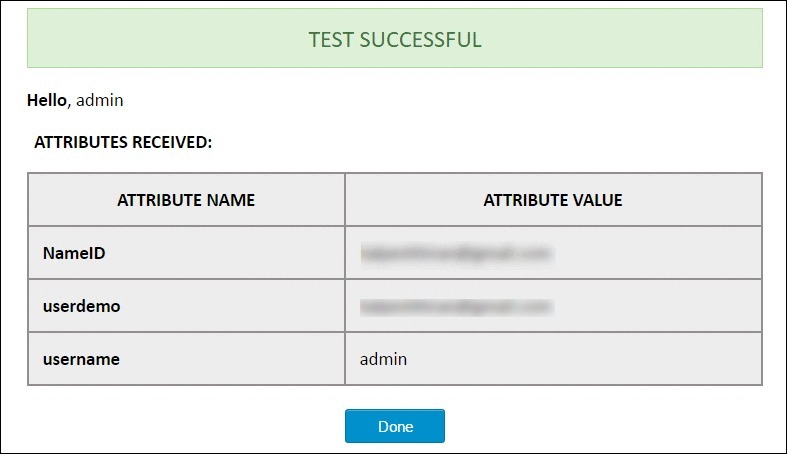
Step 4: Test Configuration
- The below screenshot shows the successful result.
- This screenshot shows the attributes that are received and are mapped by attribute mapping.
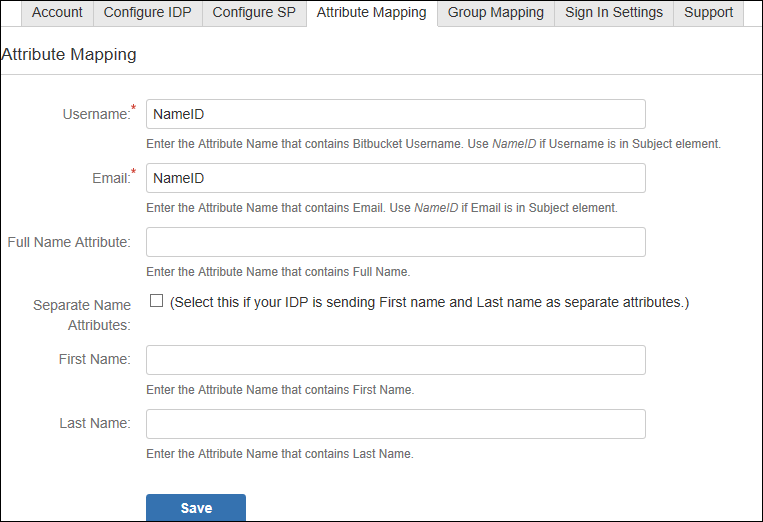
Step 5: Attribute Mapping
- Attribute Mapping is used by the Identity Provider(IdP) and the Bitbucket group(SP) to map user information from IdP to SP.
- Attribute Mapping helps you to get user attributes from your IdP and map them to Bitbucket user attributes.
- Attributes received in successful Test congiguration are used for Attribute Mapping.
- In Attribute Mapping, Details like username and NameID as shown in step 4 of Test Successful are mapped to Username and Email respectively.
- Also Full Name or Separate Name (i.e First and Last Name) attributes are given as options according to Bitbucket user attributes.
- While auto registering the users in your Bitbucket group these attributes will automatically get mapped to your Bitbucket user details.
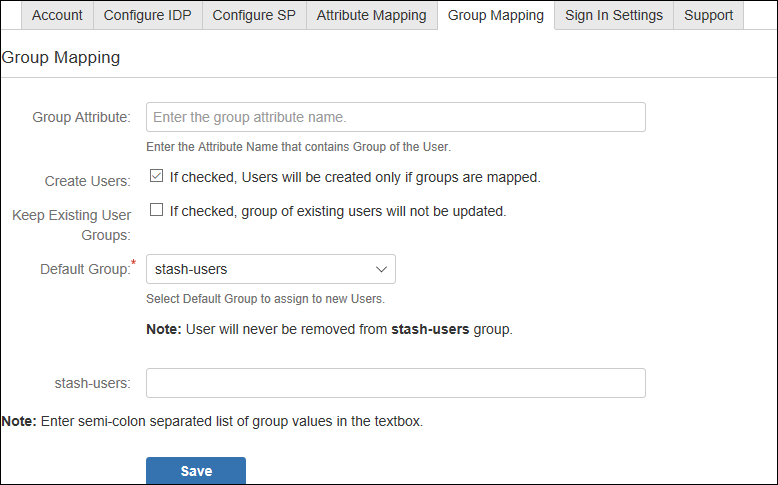
Step 6: Group Mapping(optional)
- Bitbucket plugin assigns roles to groups which are mapped against those groups.
- Bitbucket uses a concept of Groups, designed to give the site owner the ability to control what groups can and cannot do within the site.
- In Group Attribute enter the Attribute Name given against role value of Test Configuration for the user.
- Clicking Create Users checkbox will allow user creation for only those roles whose role is mapped to Bitbucket groups in Group Mapping tab. If unchecked, users whose groups are not mapped to Bitbucket groups, their group will be set as Default Group.
- Group mapping helps you to assign specific roles to users of a Bitbucket group from your IdP.
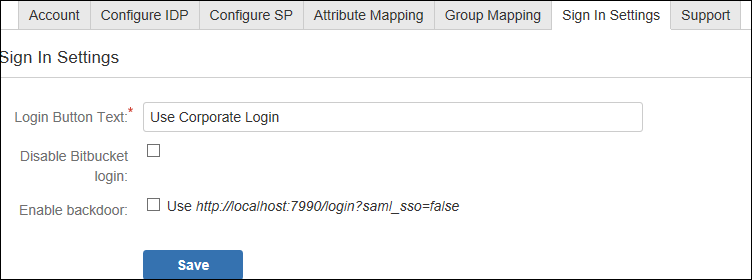
Step 7: SSO Sign In Settings
There are different ways to login to your Atlassian Bitbucket Website.
- Login Button Text make your organization's SSO easy for Bitbucket users to recognize.
- You also have option to disable your Bitbucket login by clicking Disable Bitbucket Login checkbox if you have enable a Single Sign-On plugin. (If disable your Bitbucket Login all users will be redirected to IdP for login)
- Enable backdoor checkbox allows Administrators to bypass external authentication and log in with a Bitbucket administrator using user name annd password. Note: that a logged-in user cannot access this page only an administrator could.
×
![]()
For Further Details Refer :
https://blog.bitbucket.org/2013/05/07/beautiful-and-relevant-notifications/https://marketplace.atlassian.com/plugins/com.miniorange.sso.saml.bitbucket-sso/server/overview
Business Trial For Free
If you don't find what you are looking for, please contact us at info@miniorange.com or call us at +1 978 658 9387 to find an answer to your question about Atlassian Single Sign On (SSO).
Watch the videos to learn more
Watch Demo
Trending searches:

