Okta as IdP for wordpress
Okta Single Sign-On (SSO) login for WordPress [SAML] can be achieved by using our WordPress SAML Single Sign-On (SSO) plugin. Our SSO plugin is compatible with all the SAML compliant Identity Providers and enables secure Okta Login into WordPress sites. Here we will go through a guide to configure WordPress Okta SSO / Login into WordPress site by considering Okta As IdP (Identity Provider) and WordPress as SP (Service Provider).To know more about other features we provide in WordPress SAML Single Sign-On (SSO) plugin, you can click here.
 Pre-requisites : Download And Installation
Pre-requisites : Download And Installation
To configure Okta Single Sign-On (SSO) / Login with Okta as SAML IDP into Wordpress, you will need to install the miniOrange WordPress SAML SP SSO plugin:
Steps to configure Okta Single Sign-On(SSO) Login into WordPress
Step 1: Setup Okta as IDP (Identity Provider)
Follow the steps below to configure Okta as IdP
 Configure Okta as IdP
Configure Okta as IdP
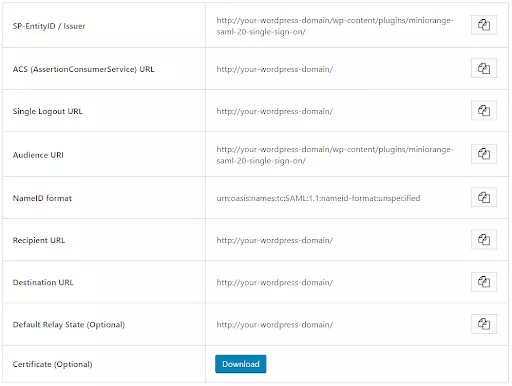
- In the miniOrange WordPress SAML SP SSO plugin, navigate to SP (Service Provider) Metadata tab. Here, you can find the SP metadata such as SP Entity ID and ACS (AssertionConsumerService) URL which are required to configure Okta as the IdP (Identity Provider).
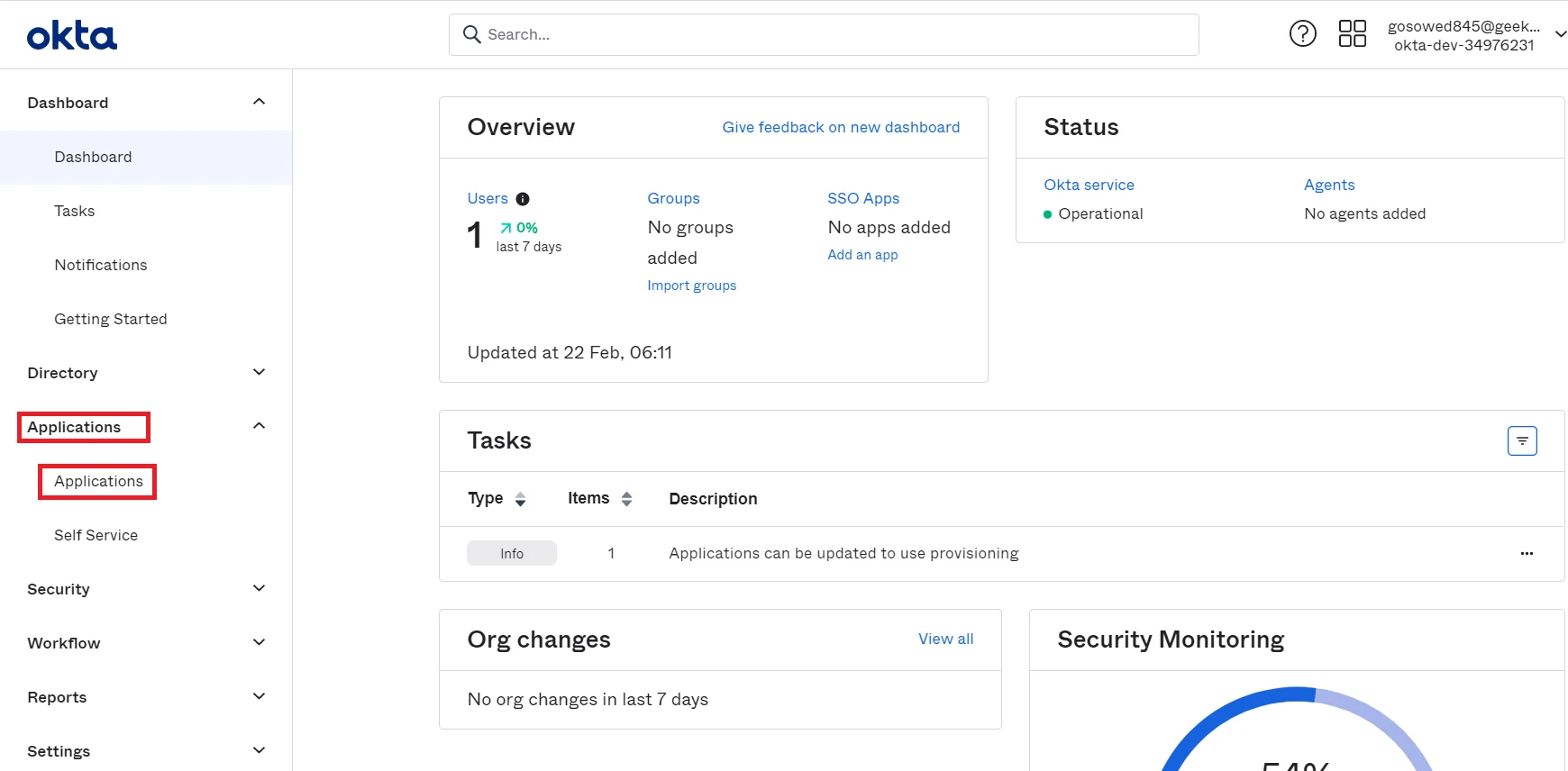
- Login into your Okta Admin dashboard.
- Then navigate to Applications tab and select Applications.
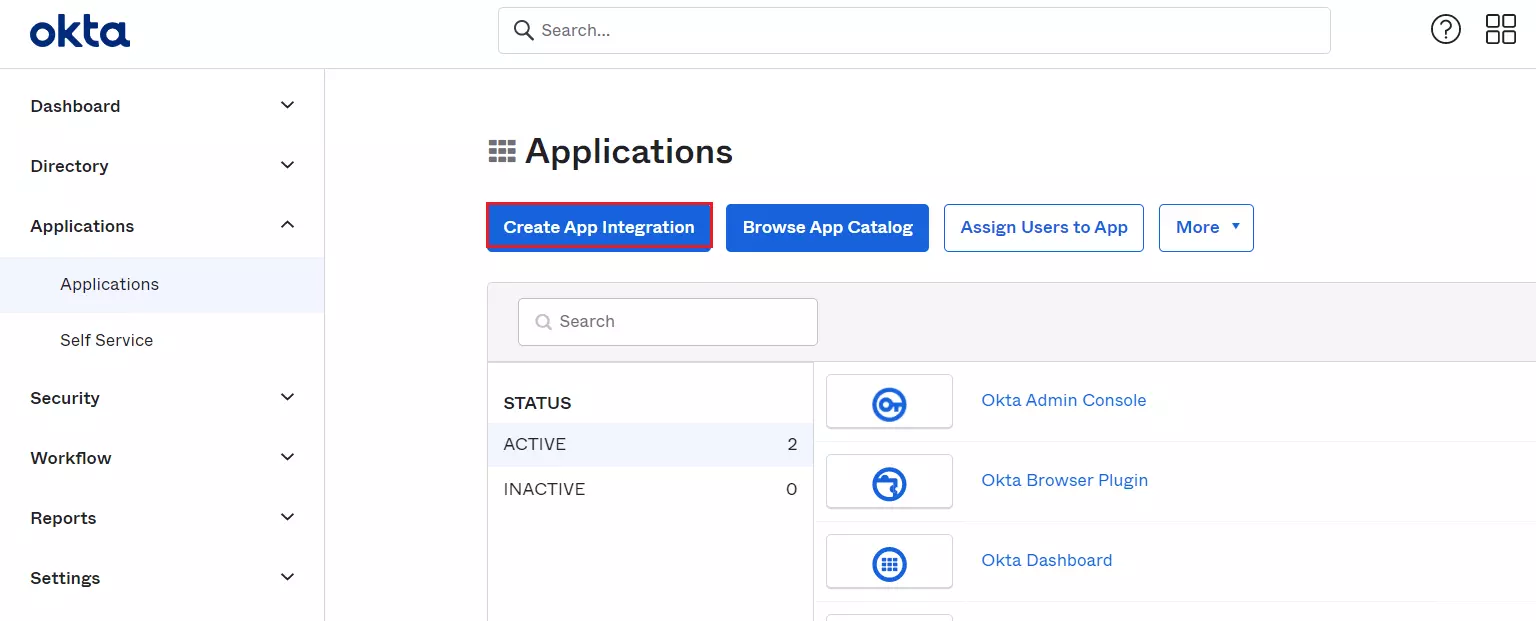
- Click on the Create App Integration button to create new app.
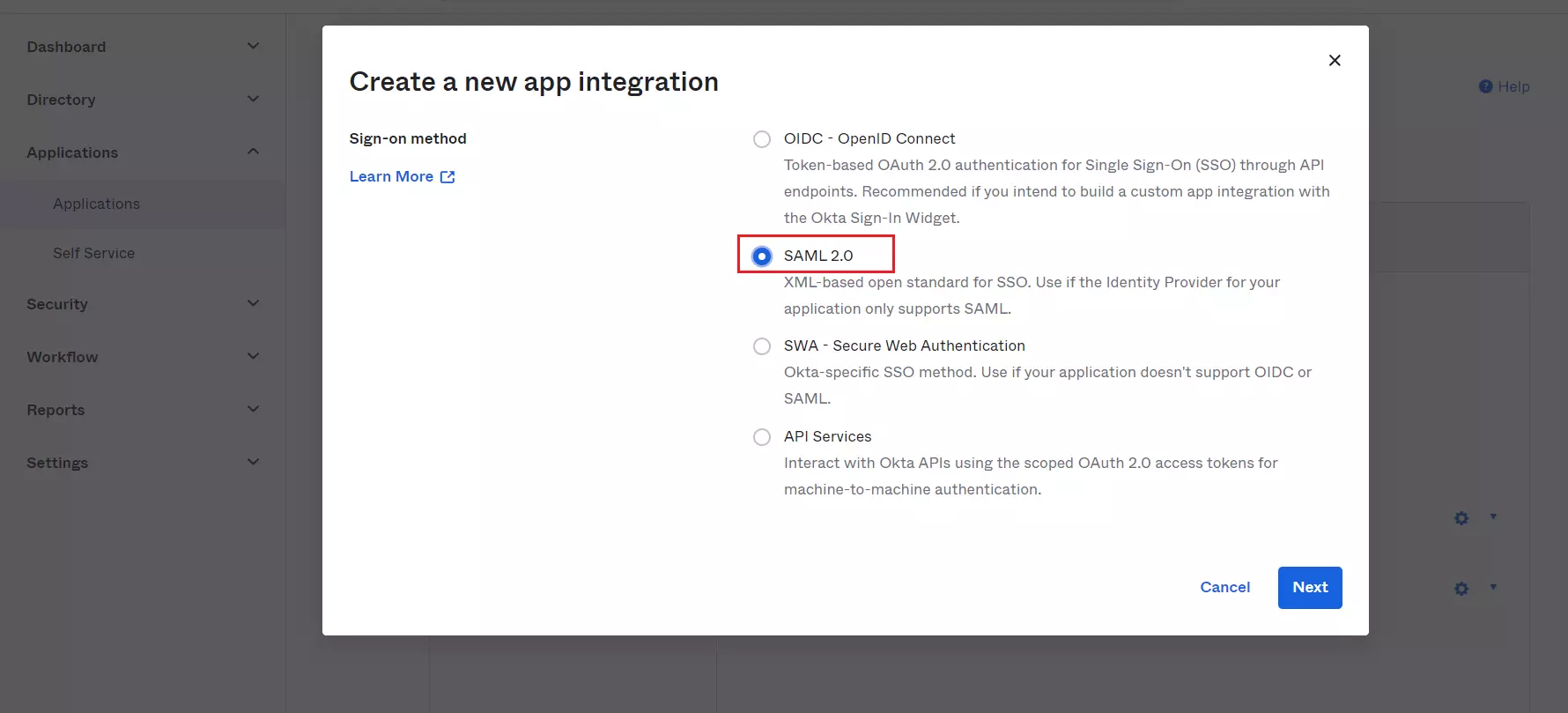
- Select SAML 2.0 as Sign-On method and Click on Next button.
- In General Settings tab, enter App Name and click on Next button.
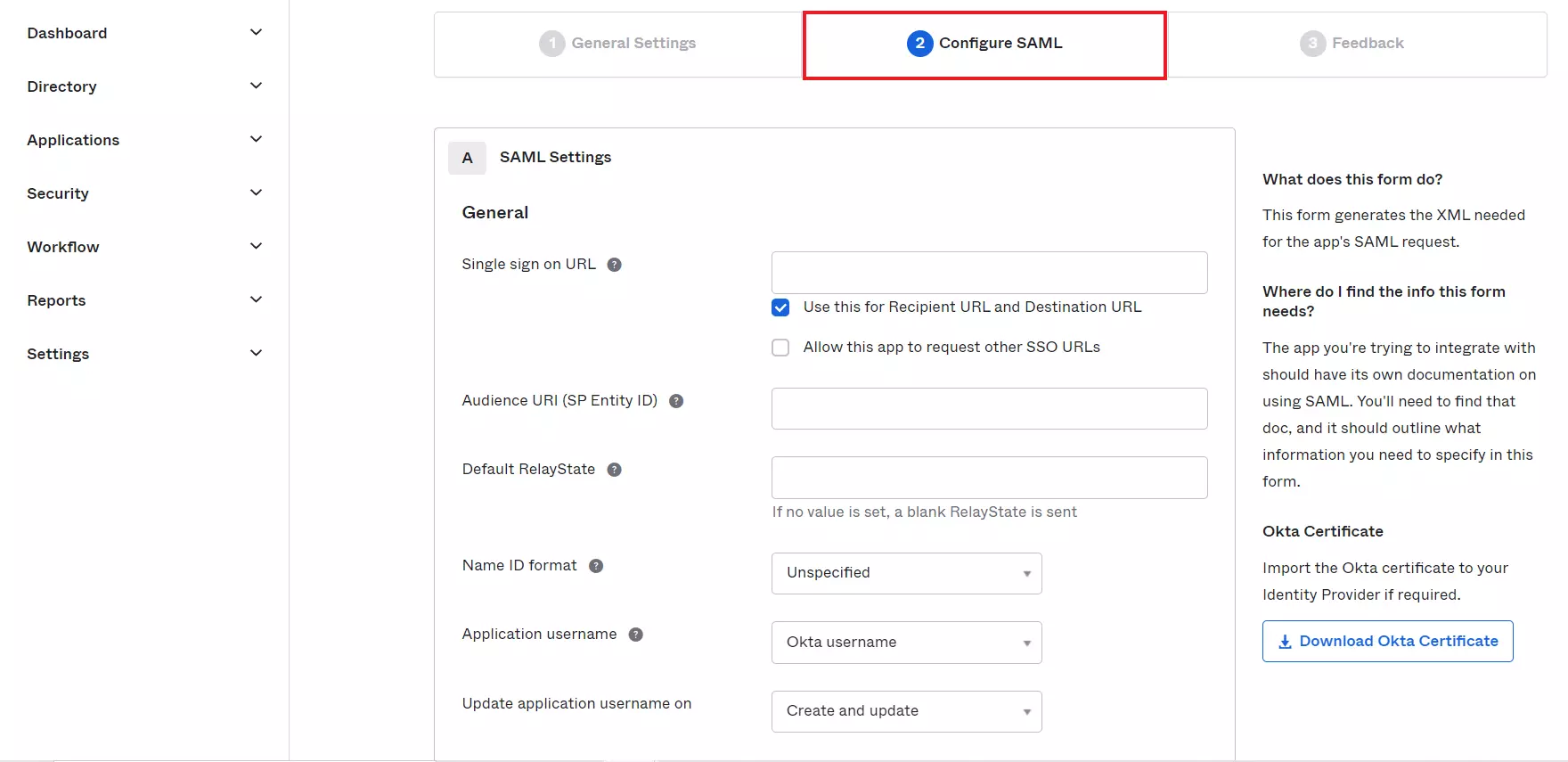
- In Configure SAML tab, enter the required details:
- Configure Group Attribute Statements (Optional) and click on Next button.
- If you have integrated your Active Directory in Okta and want to map the AD groups, please make sure
that you have added the OUs used to import groups.You will also need to map the memberOf
attribute under the integrated directory’s configuration.
| Single Sign On URL |
ACS (AssertionConsumerService) URL from the Service Provider Metadata tab of the Plugin |
| Audience URL (SP Entity ID) |
SP Entity ID / Issuer from the Service Provider Metadata tab of the Plugin |
| Default Relay State |
Relay State from the Service Provider Metadata tab of the Plugin |
| Name ID Format |
Select E-Mail Address as a Name Id from dropdown list |
| Application Username |
Okta username |
 Assigning Groups/People
Assigning Groups/People
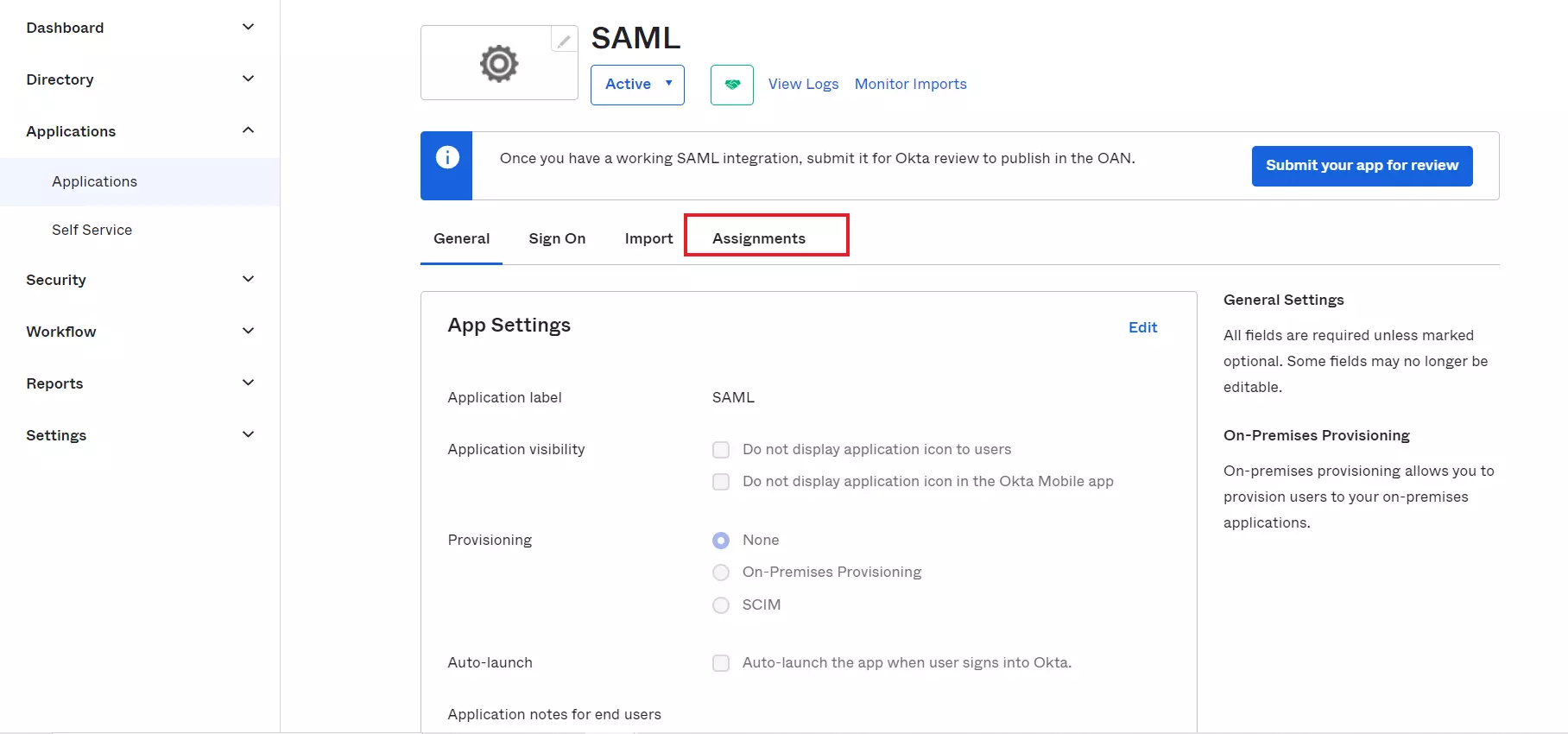
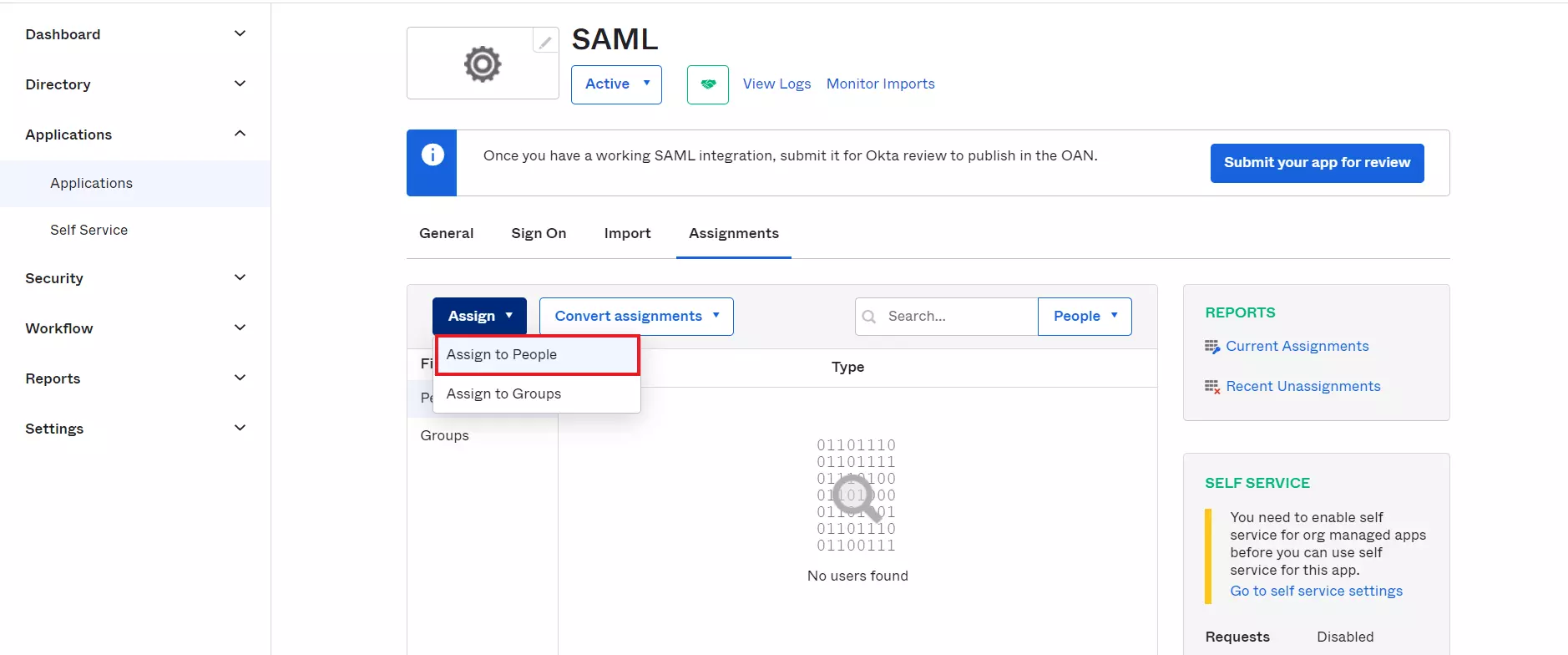
- Navigate to the application you created and click on the Assignments tab in Okta.
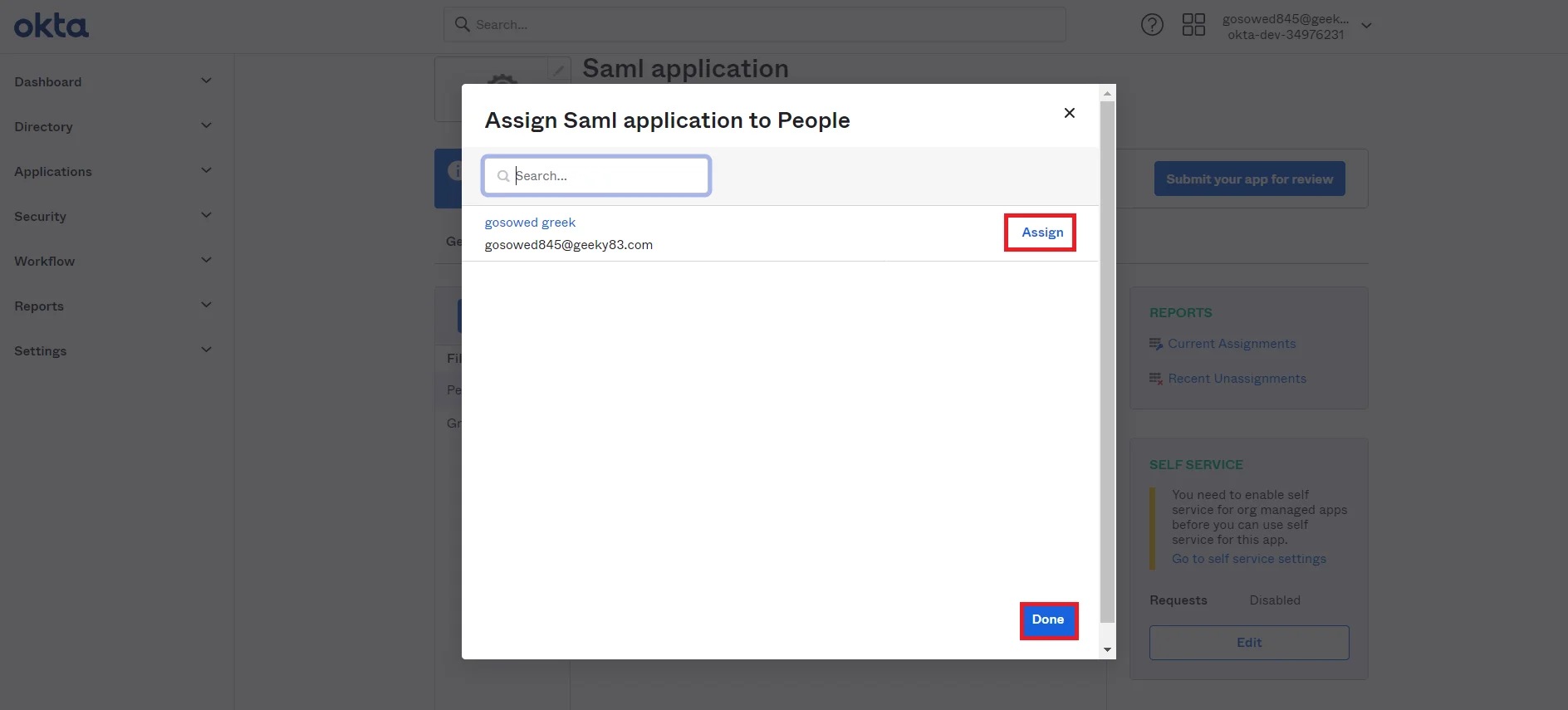
- Click on Assign button to Assign People and Assign Groups.
- Once you Assign the user, click on Done button.
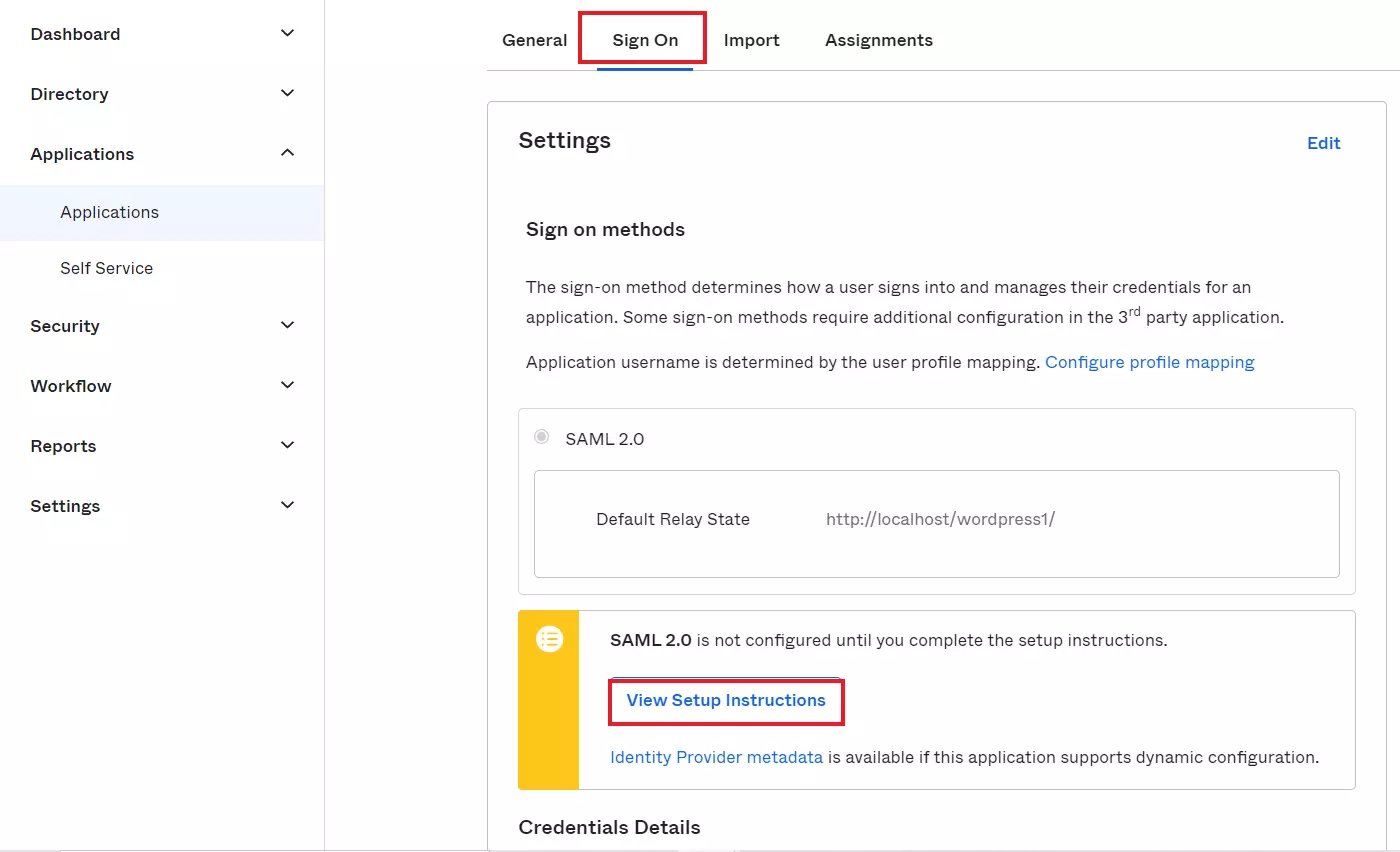
- Navigate to Sign On tab and Click on View Setup Instructions.
- You will get the Okta Metadata URL / SAML Login URL (Single Sign on URL), Single Logout URL, IDP Entity ID and X.509 Certificate. You will need this to configure the Service Provider.
- You have successfully configured Okta as SAML IdP (Identity Provider) for achieving Okta Single Sign-On (SSO) Login, ensuring secure Okta Login into WordPress (WP) Site.